Table of Contents
What is SCIM and how does it work?
Developers working on apps, programs, and other software projects need effective and secure authentication and identity protocols for adopters and end-users. A common debate that arises in this regard is between SCIM vs SAML. While these protocols have similarities, there are also key differences between them.
Below, we’ll explain what these protocols are and how they work, provide a side-by-side comparison of them, and break down which is the better choice for specific situations.
What is SCIM and how does it work?
System for Cross-Domain Identity Management (SCIM) is an open standard based on hypertext transfer protocol (HTTP). Its primary use case is identity management, including identity provisioning and de-provisioning, or streamlining functions like creating, reading, updating, and deleting (CRUD) user identities. SCIM empowers rapid, secure syncing by facilitating identity management across many platforms.
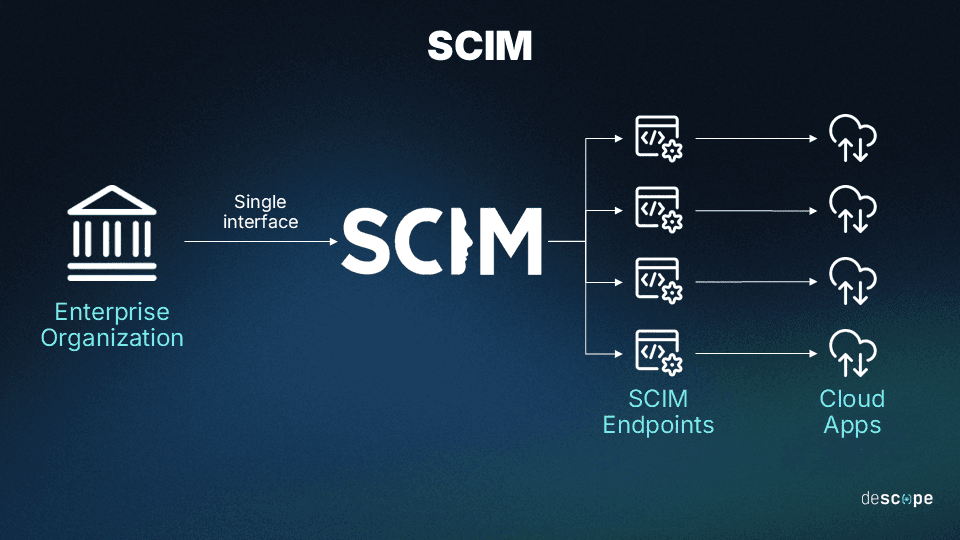
SCIM uses RESTful APIs to manage IDs between identity providers (IdPs) and service providers (SPs). These APIs allow for automation of the provisioning and de-provisioning of user accounts across different systems.
SCIM allows for seamless identity management for both IT teams and end users by reducing the overall complexity at login and throughout account management. This in itself leads to better security, as users are less vulnerable to credential theft and social engineering. It also improves the user experience and supports scalability by removing the burden of custom API navigation.
B2B Enterprise Readiness Checklist
Score your tech stack on enterprise readiness pillars - from dev and IT experience to security and architecture.
Download
What is SAML and how does it work?
Security Assertion Markup Language (SAML) is an XML-based protocol used to create assertions related to user authentication and authorization. It is a central part of many auth processes, creating uniform processes by which IdPs and SPs recognize their end users.
Almost all software using SAML today uses SAML 2.0, which was released in 2005.
SAML allows users to access multiple applications and platforms with a single account, which is why SAML is commonly used for single sign-on (SSO) and federated authentication.
Read more: SAML vs. SSO: Understanding the Differences
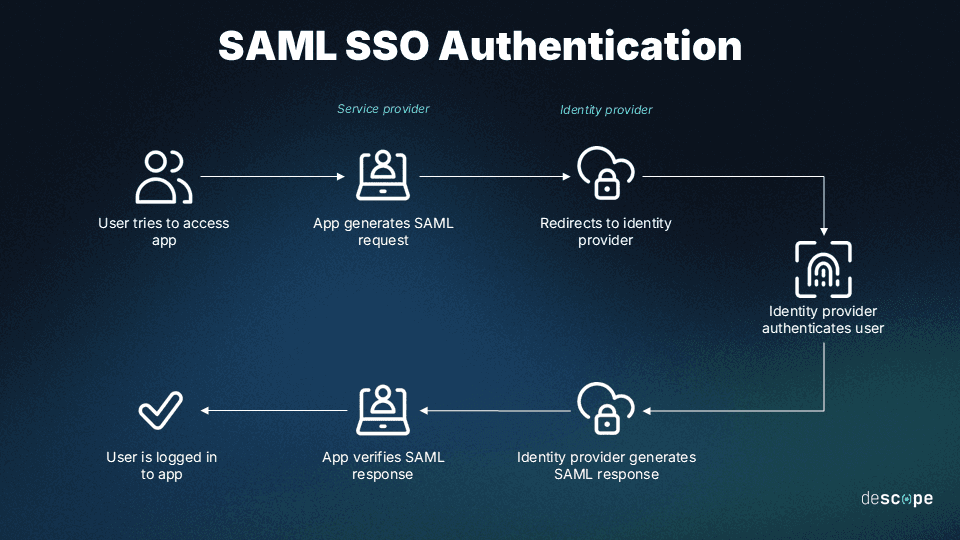
SAML works primarily through three kinds of assertions:
Authentication: These assertions verify a user’s identity, along with other pertinent details such as login time, location, and method of authentication.
Attribution: These assertions transfer attributes critical to authentication and authorization (i.e., department, status, contact information) from the IdP to the SP.
Authorization: These assertions detail whether or not the user has authorization to access a specific location or perform a specific action, empowering SP enforcement.
By exchanging these assertions back and forth, IdPs, SPs, and other stakeholders can be certain that users are who they say they are and have authorization to access certain files or systems.
SAML auth provides security assurance by eliminating the need for multiple accounts, which benefits both IT teams and end users. Users have fewer credentials and login protocols to memorize, which facilitates safer and easier account management. IT teams field fewer account resets and other calls, reducing IT spend. And developers can focus their attention more directly on mission-critical elements of a given software project, speeding and scaling up production.
SCIM vs SAML: Side-by-side comparison
SCIM and SAML serve distinct yet complementary roles in identity and access management. SAML focuses on authentication, powering SSO to simplify and secure user access across multiple applications. On the other hand, SCIM streamlines user identity management by automating account provisioning and de-provisioning. Together, they create a cohesive, secure, and efficient user experience in enterprise environments.
Here’s how SAML vs SCIM stack up:
| SCIM | SAML |
|---|---|---|
Functionality | Identity management across different systems | Authentication and authorization across different systems |
Methodology | RESTful APIs facilitate CRUD functions in a standardized, JSON-based format | XML-based assertions to exchange data between IdPs and SPs |
Security assurance | High, with secure API communications and consistency in user data management across systems
| High, with support for digital signatures, encryption, and secure transmission of authentication assertions |
User experience | Improves user management efficiency by automating account creation and removal, minimizing manual errors | Enhances user experience by enabling seamless SSO, reducing the need for multiple logins |
Main use cases | Automated user provisioning and cross-platform management | SSO for enterprises, federated identity management |
How to choose between SCIM and SAML
SCIM plays a major role in future-focused identity management, especially in systems that make heavy use of cloud technology. It’s a great choice for growing organizations and those with rapidly evolving tech stacks that need to maintain consistent and up-to-date user information.
On the flipside, SAML is one of the longest-running technologies in auth and across IT more broadly, powering secure communication and verification for two decades. It’s a great choice for more mature organizations that make use of legacy software, or service-based businesses whose clients use such legacy programs and ecosystems either primarily or exclusively.
However, organizations don’t necessarily need to choose between SCIM and SAML but rather make them work together.
So, if you need:
Seamless user access across multiple applications, choose SAML
To automate identity management across different accounts, choose SCIM
Comprehensive identity and access management, choose both
Need both SCIM and SAML? Turn to Descope
To bridge the gap between the intricacies of SAML and SCIM implementation, Descope offers you a simple, innovative solution. Descope's CIAM platform offers enterprise-ready features such as SSO, fine-grained authorization, and SCIM provisioning with easy-to-implement drag-and-drop functionality.
Sign up for Descope or schedule a demo today to start your journey toward seamless identity and access management with SAML and SCIM.





