Stop
credential stuffing
attacks
attacks
Eliminate brute force and credential stuffing with strong passwordless authentication like passkeys.
Block bot traffic with built-in protection and 3rd-party risk identification integrations.
Reduce fraud with risk-based MFA and step-up authentication.
Popular security content
Security and ATO prevention with Descope
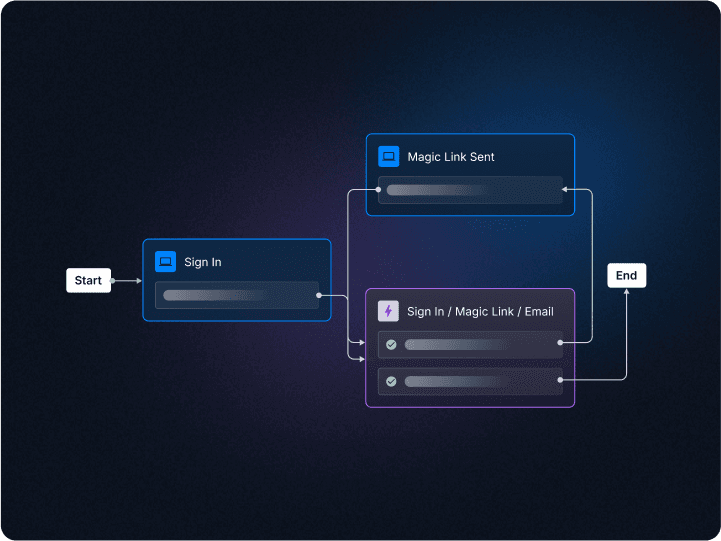
Passwordless + Password Security
Reduce your attack surface
Improve security and UX with passwordless authentication (passkeys, magic links, social login, etc.).
Run A / B tests on different onboarding paths to pressure-test them for security.
Leverage breached password detection with Have I Been Pwned.
Easily create and customize password complexity rules.
MFA
Fast, frictionless, flexible MFA
Choose any MFA method, including phishing-resistant ones like passkeys.
Add adaptive MFA for risky logins without impacting real users.
Choose from a variety of native and third-party risk signals.
Enable step-up auth for sensitive user actions.

Fraud Prevention
Identify and mitigate anomalous login behavior
Leverage native risk signals like new devices, impossible traveler, and VPN checks.
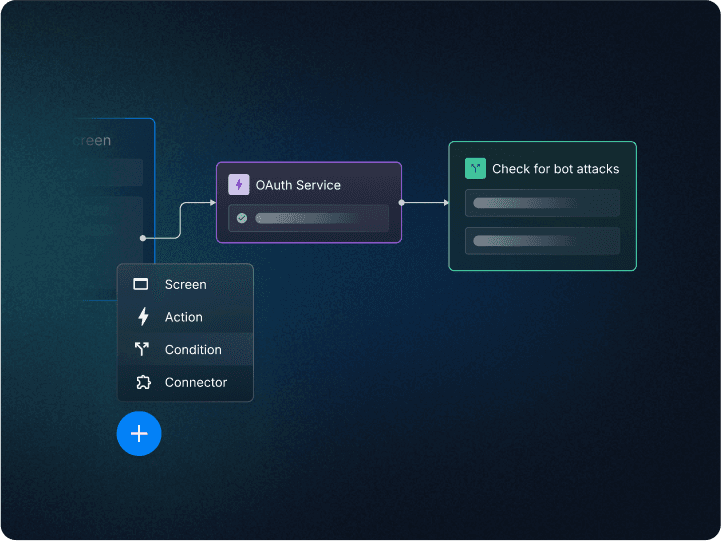
Utilize risk signals from connectors with AbuseIPDB, reCAPTCHA, Forter, Fingerprint, and many others.
Spot and stop bot attacks on your auth systems like GradRight did.
Why customers choose Descope
Fast
Set up and migrate in days and weeks rather than months and years with visual workflows.
Flexible
Choose from flows, SDKs, and APIs. Rip-and-replace or augument what you already have.
Future-proof
Change users journeys without redeploying your app or tinkering with your codebase.
We play well with others
Enrich and secure your user journeys with third-party connectors. Go passwordless without changing your primary IdP using OIDC federated authentication.
All your auth is secure with us
Security is serious business. Built by a team that has been on the security frontlines for decades, Descope is committed to exceeding industry standards in keeping your organization and user data safe and compliant.
Auth that meets devs where they are
Code as much (or little) as you want. Your choice: no-code workflows, SDKs / APIs, and everything in between.
Descope SDKs
“I’ll build the authentication screens and flows, but may need help with session management.”
Explore SDKsReady for liftoff?
If you’ve seen all you need to see, sign up and get started with Descope. If you'd like a demo, meet with our auth experts.