Table of Contents
What is a session?
Imagine session hijacking as someone sneakily taking the wheel of your car while you’re still in it, thinking you're heading to your chosen destination. But instead of driving towards a scary cliff, these digital hijackers are cruising through your online sessions, rifling through your glove box of personal information and changing your radio station to "Steal Your Data FM."
Sounds exciting? Not really. Let’s explore what session hijacking actually is, how it works and is there something you can do to prevent it and protect your organization from costly headaches.
What is a session?
To understand session hijacking, it’s important to know the basics of sessions and session management.
At its core, a session represents a sequence of interactions between two entities—typically a client and a server—occurring over a single connection period. This process begins when a user logs into an application, initiating the creation of a new session coupled with the assignment of a unique session ID. This ID is a complex alphanumeric string, consistently exchanged between the server and the client to maintain the session's continuity. It's often embedded within session cookies, URLs, or hidden within forms on a webpage. This is why session hijacking is also called cookie hijacking or cookie side-jacking.
The need for sessions stems from the stateless nature of HTTP: Each request operates independently without any recollection of previous interactions. Theoretically, this means that users would have to re-authenticate themselves for every activity within the application, a requirement that would severely impair the user experience.
Sessions, therefore, provide a seamless solution by keeping track of user-specific parameters necessary for an optimal application experience, allowing users to navigate and interact with an application without the need for constant re-authentication. These sessions remain active until the user chooses to log out or after a predefined period of inactivity, after which the session is terminated, and the user data stored during the session is purged from the memory.
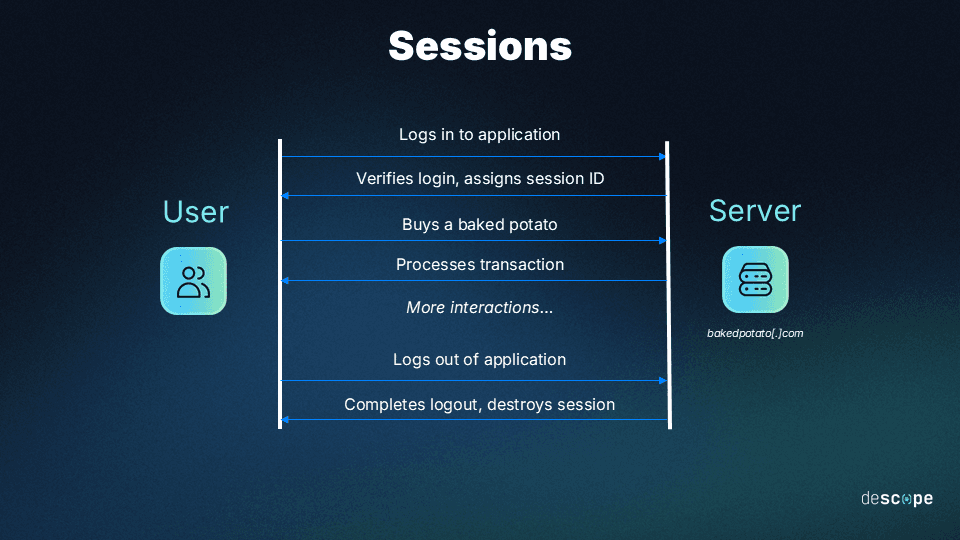
So, what is session hijacking?
Session hijacking is a cyberattack where adversaries take over a valid session ID to impersonate the legitimately authenticated user. It is one of the most common ways of exploiting poor authentication practices to gain unauthorized access that can lead to privacy breaches, unauthorized transactions, and other security concerns.
A session ID for a valid session is considered a very strong authentication method. In other words, obtaining a user’s session ID is as bad as getting their login credentials.
How session hijacking works
In session hijacking, an attacker gets hold of a valid user session to gain unauthorized access to the account. This is typically done through three methods:
Brute force: The attacker keeps trying session IDs until they are successful.
Calculation: If the session IDs are generated in a non-random manner, the attacker can calculate them.
Theft: The attacker acquires the session ID through techniques like session sniffing, session fixation, and cross-site scripting.
The attacker with a stolen session ID can access resources and functionalities as a legitimate authenticated user, leading to:
Identity theft and account takeover
Fraudulent banking transactions and purchases
Exfiltration of the user’s personal information or their company’s sensitive data
Read more: Broken Authentication 101
Common session hijacking methods
Here are some common ways in which session hijacking attacks are carried out:
Session sniffing
Session sniffing, also known as session side jacking, involves attackers using a sniffer like Wireshark to inspect network traffic and extract the session key. Session sniffing is particularly effective on unencrypted networks like public Wi-Fi.
Applications that don’t use SSL/TLS encryption – or use it selectively – are also vulnerable to session side jacking attempts. For example, if the login page uses SSL/TLS encryption, attackers can’t view a user’s password. But if the rest of the application does not use SSL/TLS encryption, session hijacking can still occur.
Cross-site scripting (XSS)
In cross-site scripting, attackers exploit web application or server vulnerabilities by injecting malicious scripts from the user’s device. This is commonly done by sending users emails with script-injected links. The user will click the link because it points to a known, trusted website. But when they click the link, the injected script will execute.
If the code copies the user’s active session cookies and sends them to a server controlled by the attacker, they can hijack the user’s session.
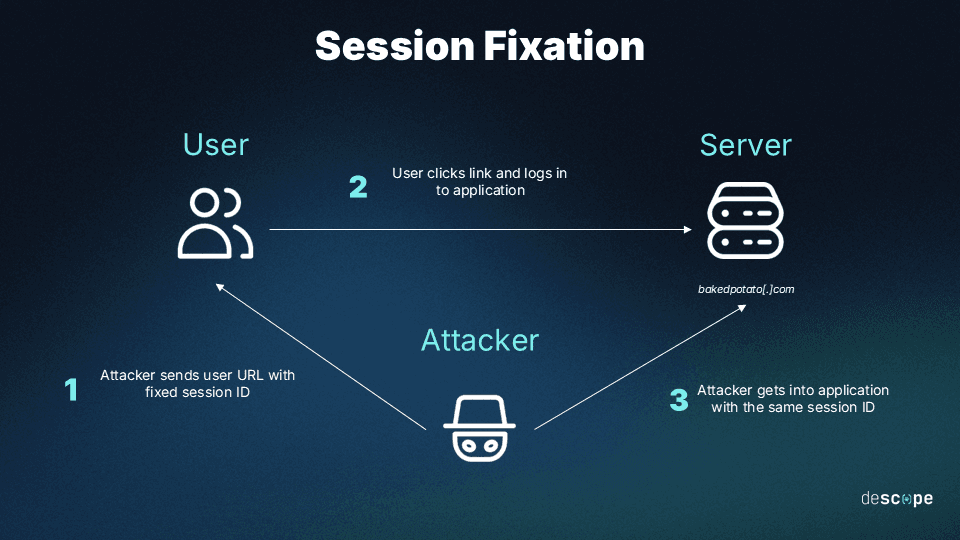
Session fixation
In session fixation, attackers take over user accounts by setting their session ID to a string known by the attackers. Websites that accept session IDs within URLs and do not perform security validation on them are particularly prone to session fixation attacks.
In practice, session fixation starts by attackers sending users a URL that contains a session ID, usually in a phishing email. When the user clicks the link and logs into the application, the attacker knows the valid session ID and can remotely hijack the session.
Session hijacking prevention tips
Here are some security measures your organization can take to prevent session hijacking attacks:
Keep an eye on session duration
Different applications will have different levels of tolerance to long session lengths. A streaming or social media app might keep users logged in for weeks, while a banking or healthcare app might log users out after a few minutes of inactivity due to the increased risk of session hijacking.
Developers should ensure that session durations align with the level of sensitivity of the application. For example, implementing a short session timeout period reduces the risk window for an attacker. So if a session ID is stolen, it will be valid only for a limited time.
Moreover, automatically logging users out after a set period of inactivity or when suspicious behavior (such as a change in IP address) is detected can further secure the session.
Terminate sessions timely
Providing a visible and easily accessible logout button allows users to end their sessions when they are done. This is especially important in shared or public environments, where an open session could be hijacked by the next person who uses the computer.
By default, the session ID should be invalidated on the server-side once the user logs out, making it unusable for future requests. This ensures that even if an attacker obtains the session ID, they won’t be able to use it.
Regenerate session IDs
Change session IDs at key points during the user's interaction with the application, especially after login or a critical action (e.g., changing passwords). This prevents session fixation because the session ID provided by the attacker will not persist after the user logs in. Any session-related tokens should be immediately invalidated when the session ends to prevent attackers from reusing them.
Don’t put session IDs in URLs
Another way to prevent session fixation is to not accept session IDs in URLs. More broadly, session IDs should not be accepted from any GET or POST variable.
Use HTTPS
It’s important to use HTTPS on the entire application or website, not just the login page. Using HTTPS everywhere encrypts all traffic and prevents attackers from sniffing for session IDs.
Set session ID cookies to HttpOnly
Session ID cookies should be flagged as HttpOnly to prevent client-side JavaScript from accessing any session details. This reduces the likelihood of cross-site scripting attacks.
Add MFA
Multi-factor authentication adds an additional layer of security, making it more difficult for attackers to gain unauthorized access even if they manage to hijack a session.
Educate users
Users should be encouraged to use secure, trusted devices and avoid public Wi-Fi networks when accessing sensitive accounts. Public Wi-Fi networks are often unsecured, making it easier for attackers to intercept data, including session IDs.
Moreover, you should educate them about the dangers of phishing and how to recognize suspicious emails, links, or websites.
Prevent session hijacking with Descope
The battle against session hijacking is a dynamic and ongoing challenge that requires vigilance and robust security.
For developers and organizations looking to prevent session hijacking, Descope offers easily-implemented yet secure session management and customer authentication solutions. With a drag-and-drop platform and a host of SDKs, Descope makes building authentication and authorization flows a breeze
Sign up for a Free Forever account with Descope for better and safer session management. Have questions about our platform? Book time with our experts.





