Table of Contents
Four of the safest MFA methods
Main takeaways
The safest MFA methods like passkeys, email magic links, authenticator apps, and hardware security keys offer superior protection against phishing and credential theft.
Developers should view SMS-based authentication and push notifications with caution due to vulnerabilities including SIM swapping and MFA fatigue.
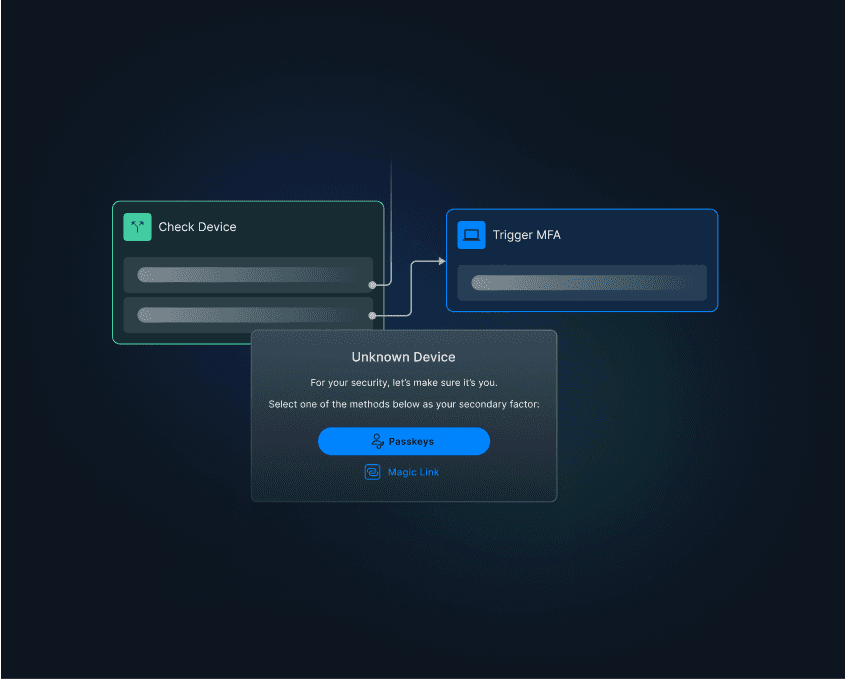
The strong authentication flows combine different factors, which include inherence (something you are), possession (something you have), and knowledge (something you know).
MFA can be one of the safest authentication methods when implemented effectively.
In particular, effective MFA is resistant to phishing, preventing credential theft via deceptive links that some other auth methods are susceptible to. Phishing-resistant MFA also mitigates MFA fatigue attacks in which cybercriminals spam users with approval requests.
Sound MFA has strong fallback mechanisms built-in, obviating redundant or insecure recovery methods that introduce new risks—along with additional friction. It also enables secure session handling, seamlessly managing user access sessions and reducing the risk of session hijacking.
But, to take advantage of these benefits, developers should leverage the safest MFA methods.
Four of the safest MFA methods
MFA is inherently secure and seamless when implemented correctly. But there are certain ways to approach MFA that maximize its security without adding friction. Four of these methods are:
Passkeys
Email magic links
Authenticator apps
Hardware security keys
Let’s take a closer look at each one.
Passkeys
One of the safest MFA methods available leverages passkeys to safely and seamlessly identify users. Passkeys utilize public key cryptography, with an app or program giving a client (e.g., a browser) the configurations to create a new credential (a passkey) for the user. Then, an authenticator (e.g., Apple Face ID) verifies the user’s presence. Typically this is confirmed through a biometric scan, though using a PIN is possible. The registration process creates a public-private key pair, storing it on the user’s device for seamless auth.
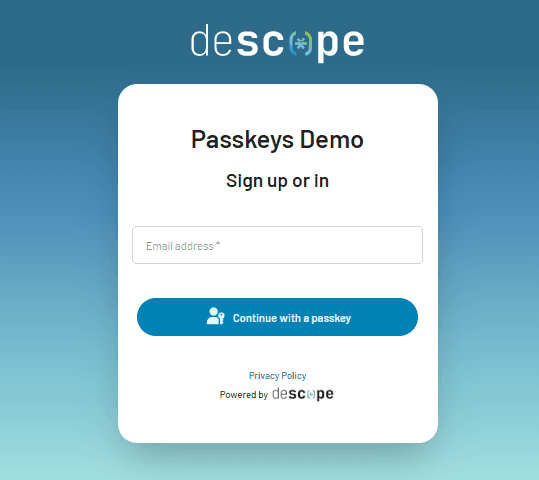
Try out passkey authentication as an end user on our demo site.
One of the main reasons passkeys are considered secure is that passkey-based auth typically focuses on inherence-based factors like biometric scanners and other on-device methods that prove possession. Because they commonly rely on biometrics, passkeys are generally safer than relying on knowledge factors like passwords. Unlike passkeys, these can be forgotten by users, intercepted or stolen by cybercriminals, or even guessed when not strong enough.
One limitation of passkey auth, per a Consumer Reports deep-dive, is that their adoption is somewhat limited relative to other common auth methods. Users may not be able to use passkeys on every site and service, depending on what devices they are using.
Email magic links
Similar to passkeys, email magic links are a safe way to use MFA because they also forgo using a password. On the user side, the process is as simple as inputting an email address, getting mailed a link, and seamlessly following it to log in. However, on the backend, a more complicated process is working to ensure that the session is secure.
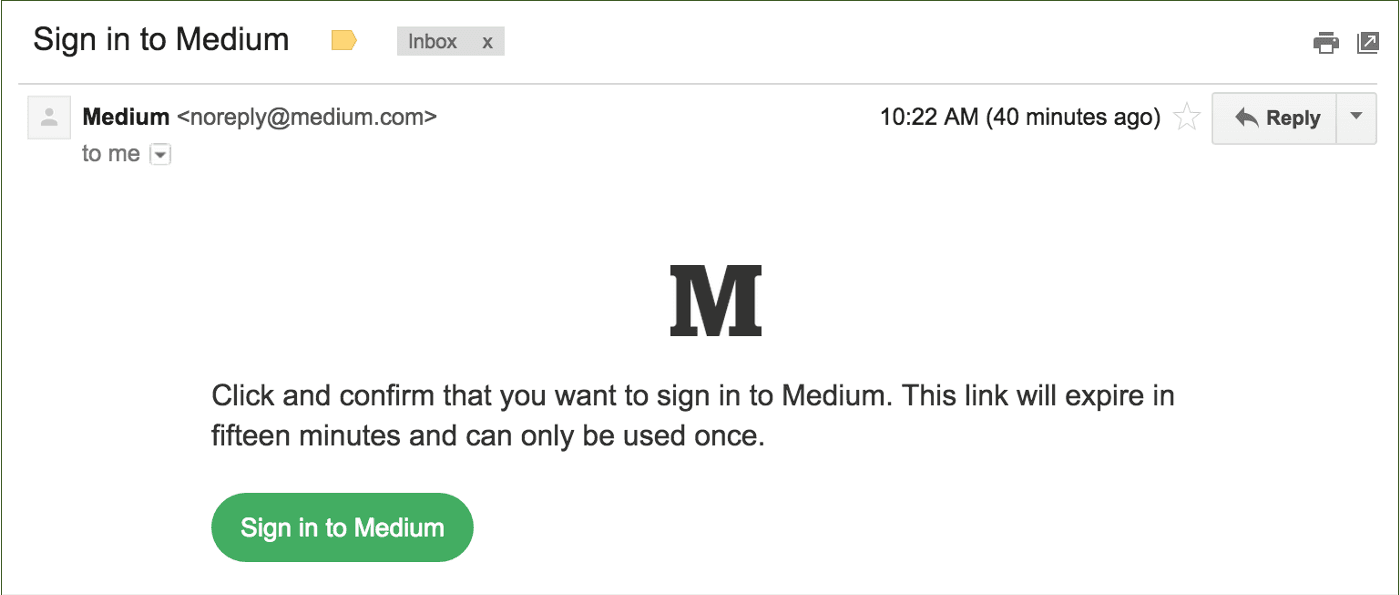
Magic links depend on the security of a user’s email account. Services using this method check the registry for an active user account with a given email, then embed a token in a link sent to the address.
One challenge with email magic links is deliverability—if the email doesn’t reach the user’s inbox, they can’t log in. Factors like spam filters, low domain reputation, or improper email authentication settings can all impact deliverability.
To improve reliability, businesses should:
Send from a high-authority domain.
Set up SPF, DKIM, and DMARC to authenticate outgoing emails and prevent spoofing.
Monitor bounce rates and spam complaints to catch deliverability issues early.
Authenticator apps
Authenticator apps are one of the safest MFA methods, especially when paired with encrypted backups. Applications such as Google Authenticator and Authy leverage a variety of tools to ensure users are who they say they are—and authorized to access specific content or systems.
For example, most authenticator applications utilize time-based one-time passwords (TOTP). In the authenticator app use case, a TOTP is typically a software security key sent to the user in the app. While the seed will remain constant on a device or platform, the time-sensitive element typically expires between 30 and 90 seconds, meaning there is very little time to log in securely.
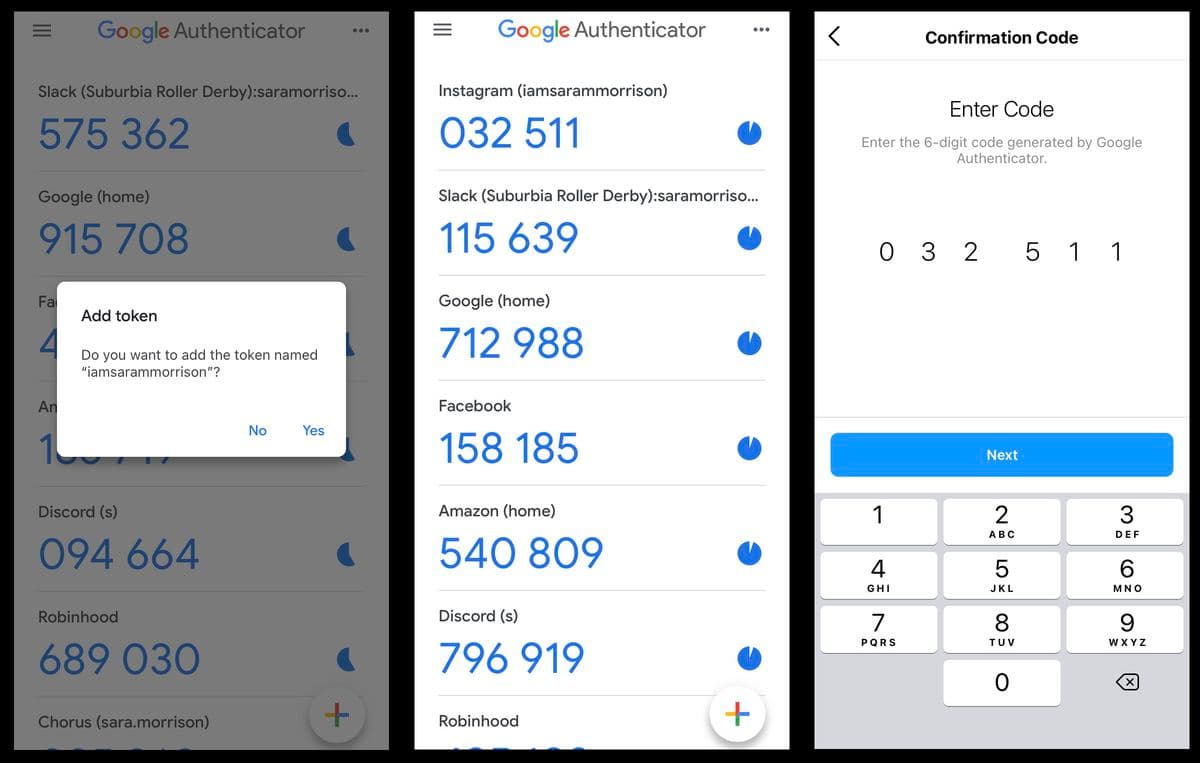
This limitation makes TOTPs significantly more secure than standard OTPs, as even the most sophisticated cybercriminals would struggle to intercept and use them before they expire.
These apps are also more secure than SMS-based MFA, which can be vulnerable to phishing.
However, there are possible drawbacks or pitfalls, such as insecure backups and the potential for a device to be lost or stolen. But these risks affect most other methods, as well.
Hardware security keys
Another safe MFA method involves the use of hardware security keys as a primary guarantor of identity. These small physical devices (such as USB or NFC keys) are inherently phishing-resistant since they use cryptographic protocols.
One of the most commonly used hardware security keys is YubiKey. It supports multiple authentication methods, including OTPs, passkeys, and other cryptographic protocols. Compared to standard six-digit codes, YubiKey’s OTPs use 128-bit encryption, making them significantly more secure.
Hardware security keys are particularly useful for high-risk accounts of IT admins, executives, or anyone handling sensitive data. They’re also a great choice for organizations that prioritize security over convenience, especially in industries where phishing attacks are a major concern.
That said, they aren’t for everyone. Some devices don’t support them natively, and for businesses with a large workforce, the cost of purchasing physical keys for everyone can add up. But if your budget allows, they’re one of the strongest defenses against account takeovers.
MFA methods to use with caution
While the safest MFA methods are near-foolproof when implemented carefully, developers should practice caution when they are limited to more baseline MFA deployments. For example, a basic SMS-based MFA system could leave users susceptible to SIM-swapping and phishing attacks.
Push notifications can leave users and systems vulnerable to MFA fatigue. If using these baseline systems, developers should consider additional backend controls to monitor and potentially terminate sessions.
Examples of safe MFA flows
Often, the safest MFA methods are best when implemented in specific, pre-set configurations that are tried and tested for both user-friendliness and security. Three examples include:
Password + hardware token
Passkey-based authentication flow
Password + email magic link
Let’s examine them.
Password + hardware token
This flow is best suited for high-security environments. Here’s how the process works:
Step 1 – A user enters a strong password, ideally of a minimum length and complexity set by the app and/or the cybersecurity policy of the organization utilizing the software.
Step 2 – The user plugs in or taps a hardware token (e.g., Yubikey), which finishes authenticating the individual.
The reason this flow is ideal is that it makes good on the promise of MFA.
It requires one thing the user knows (a password) and one thing they have (via a hardware token). Requiring two factors makes for a much more robust setup without adding too much overall friction.
Passkey-based authentication flow
This flow is a form of passwordless login that uses a passkey (public key cryptography). It’s one of the safest MFA methods for passwordless auth.
Here’s what the flow looks like in practice:
Step 1 – Users are prompted to sign in with a passkey. Typically, platforms like Apple’s iCloud Keychain, Google’s Password Manager, or Windows Hello enable secure cryptographic key storage.
Step 2 – Users perform biometric authentication or enter a PIN via their registered device. Fingerprint, facial scans using built-in sensors, or the PIN will confirm the identity of the individual.
This flow is strong because passkeys are inherently resistant to phishing. They don’t involve transmitting passwords, and the cryptographic nature of the passkey ensures that even if an attacker gains access to a device, they cannot use the passkey without biometric authentication.
Put another way, there are no shared secrets in this passwordless methodology. The passkey cannot be intercepted or reused; it will only work on the associated app or site.
Password + email magic link
Another two-step method, this flow assumes that the user's phone number has been collected during account creation. The process is as follows:
Step 1 – The user enters a secure username and password.
Step 2 – The app sends a magic link to the user’s email address, which they follow.
While passwords are relatively risky on their own, adding another step to the process verifies users’ identities and mitigates any concerns that come along with the method. With the right preparation, magic link-based MFA can function excellently as a final step.
Implement the safest MFA methods with Descope
Implementing the safest MFA methods is a crucial step in protecting your organization from cyber threats. By choosing strong, phishing-resistant authentication factors, you can reduce the risk of account takeovers.
Looking for an easier way to implement secure MFA? Descope’s drag-and-drop editor simplifies the process with seamless integrations and flexible authentication options.
Sign up for a Free Forever account on Descope and bolster your security without added complexity. Have questions? Our experts are here to help—reach out to learn more.