Table of Contents
How AuthQuake works
A critical vulnerability in Microsoft’s MFA infrastructure would have allowed attackers to bypass the second auth factor in under 70 minutes with no user prompts, potentially affecting over 400 million users. Microsoft has since patched the issue.
Dubbed “AuthQuake” by security researchers, the exploit combined two implementation flaws: extended TOTP validity windows (3 minutes instead of 30 seconds) and unlimited parallel authentication attempts, yielding a 50% login success rate.
AuthQuake is a stark reminder that not all MFA implementations are created equal. While traditional TOTP-based MFA may be vulnerable to timing attacks, modern solutions like passkeys eliminate these risks.
It’s easy to imagine the researchers who discovered AuthQuake humming The Rolling Stones' "Time Is on My Side" as they validated their findings. After all, time is supposed to be on the side of security. That's the whole point of time-based authentication codes: They expire quickly, making them nearly impossible to bypass before they vanish forever.
The team at Oasis Security wasn’t looking to break things maliciously. They were doing what security researchers do best: testing systems to find and fix vulnerabilities before malicious actors could discover them. "The bypass was simple,” explained Tal Hason, Oasis Security Research Engineer, “It took around an hour to execute, required no user interaction and did not generate any notification or provide the account holder with any indication of trouble."
The aptly named AuthQuake vulnerability is groundbreaking (pun intended) not just for its broad impact—potentially affecting hundreds of millions of users—but also for its simplicity. Understanding how AuthQuake works reminds us of a hard lesson in cybersecurity: sometimes the most damaging vulnerabilities aren’t highly sophisticated attacks, but operational oversights and misconfigurations*. And AuthQuake is an example of one that might change how you think about MFA.
*See also: nOAuth
How AuthQuake works
At the core of AuthQuake, there are two seemingly innocuous implementation choices in Microsoft’s TOTP (Time-based One-Time Password) validation process. The first involves the time window during which a generated code remains valid. While default TOTP standards suggest a 30-second window for each code, Microsoft’s implementation kept codes valid for approximately 3 minutes.
The second choice leading to this exploit was the rate limit on failures. Hason writes, “The limit of 10 consequent fails was only applied to the temporary session object, which can be regenerated by repeating the described process, with not enough of a rate limit. Simply put - one could execute a lot of attempts simultaneously.”
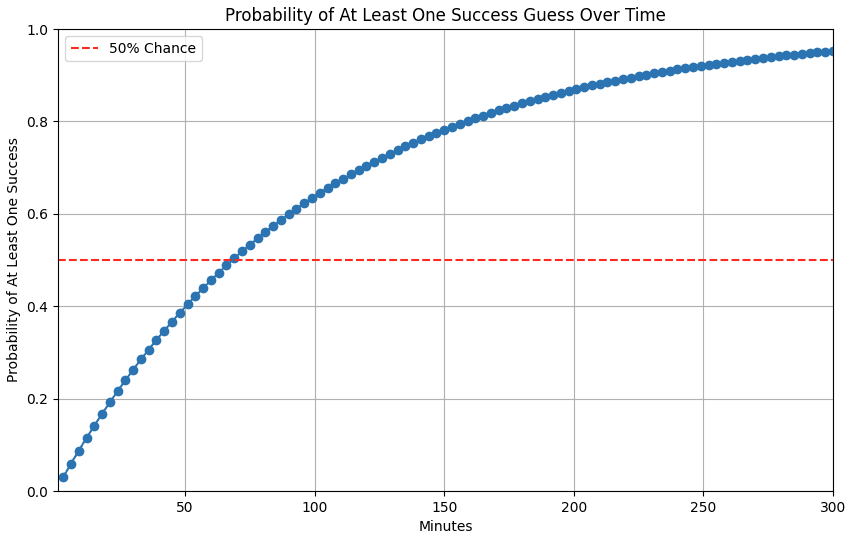
These two implementation choices led to a perfect storm, allowing Oasis Security to elicit a staggering 50% login success rate in under 70 minutes. The kicker is that this method wouldn’t issue notifications or prompts to the end user, effectively eliminating any warning signs that something was amiss.
The evolution of MFA bypass attacks
What sets AuthQuake apart from typical MFA bypass techniques is that its fundamental nature relies on specific exploits in the Microsoft authenticator ecosystem. Most MFA bypasses we’ve seen in recent years rely on a combination of social engineering, phishing, and man-in-the-middle or adversary-in-the-middle attacks to intercept communication. These tactics typically require user interaction: clicking a link, entering credentials on a fake site, or approving a push notification just to stop a barrage of prompts.
AuthQuake represents something different: a loophole in the very mechanics of Microsoft’s time-based authentication. There’s no phishing, no malicious proxy, no social engineering ploys. Just patience and processing—which is what makes it so noteworthy.
Modern exploits require modern solutions
While Microsoft has since patched this specific vulnerability with stricter rate limiting that kicks in after a number of failed attempts (and lasts for around half a day), AuthQuake should be a wakeup call for security decision-makers. This discovery perfectly demonstrates how battle-tested standards like TOTPs are still fallible and ripe for attack if implemented incorrectly. Meanwhile, modern solutions like passkeys, which leverage yet-to-be-compromised public key cryptography rather than time-based codes, are gaining much-deserved traction.
With passkeys, the vulnerability shown by AuthQuake becomes mechanically impossible. Instead of relying on time windows and guessable codes, passkeys use public-private key pairs where each authentication attempt must be cryptographically signed. The private key is unphishable as it is stored securely within a Trusted Platform Module (TPM) on the user’s device. There’s no code to intercept, no window to extend, and no way to parallelize authentication attempts.
While TOTP-based MFA significantly improves security over using passwords alone—when properly implemented, that is—the industry’s momentum toward passkeys amounts to more than an incremental improvement. It’s a fundamental restructuring of authentication methods that eliminates entire threat categories and attack vectors.
That’s not to say you should only use passkeys, though that wouldn’t be a terrible thing. Instead, be aware of the risks when choosing your MFA method, remembering that not all MFA methods are created equally. But for the app builders and security-conscious organizations witnessing the AuthQuake post-mortem, take note: It’s better to start your passkeys journey now than to wait until you’re the easiest target around.