Table of Contents
A primer on passkeys
Happy(?) World Password Day 2023 everyone! Someone remind us why we are celebrating this?
For more than half a century, passwords have taken a lot from us and given little in return. They remain the preeminent cause of data breaches and the most common way attackers gain initial access to victims’ systems. They also put a lot of responsibility on end users – creating, remembering, managing, and resetting passwords can make even the most patient person feel like Sisyphus.
Yesterday, Google announced the rollout of passkeys for personal Google accounts, following on the heels of similar support for Chrome and Android. Since our mission at Descope is to help rid the world of passwords one app at a time, we think this is great news. We are big believers in the potential of passkeys to herald a passwordless future for the Internet.
A primer on passkeys
Passkeys are a new way for users to sign in to apps without needing a password. In practice, using passkeys is exactly like unlocking your device – with a fingerprint, face scan, or PIN. You can check out this demo site to see passkeys in action.
Let’s take a look at why passkeys tick so many boxes as a strong, convenient authentication method.
No shared secrets
Passkeys use asymmetric cryptography and public-private key pairs to function. Essentially, when you create a passkey for an account, a private key is stored on your device and the public key is stored on the account server. Whenever you sign in, your device signs a unique challenge with the private key, which is then matched with the public key. Think of it like a mailbox with different keys for the mailman and the homeowner.
No app ever stores your private key on their servers, which means there is nothing for attackers to steal. You can’t write down passkeys on sticky notes or accidentally share it with cybercriminals. Moreover, the private key on your device is only meant to work with the public key on the account where the passkey was created – making any fake credential harvesting sites moot.
We have receipts for the effectiveness of public-private key pairs in preventing attacks. Recently, Cloudflare was able to thwart a phishing attack because their employees used hardware security keys based on the WebAuthn standard (the same standard used by passkeys).
TL;DR passkeys are virtually unphishable.
MFA in one step
Multi-factor authentication has largely been effective in reducing the impact of phishing and account takeover attacks. However, the extra authentication step adds user friction, which can start to grate if you need to do it every time you sign in.
Passkeys check two authentication factors without the extra step. The first check is biometrics (who you are), which unlocks the private key on your device. This proves you are in possession of your device, which is the second factor (what you have). All these checks happen under the hood, with the only part exposed to the user being the one second it takes to swipe a fingerprint.
TL;DR passkeys increase security while also increasing convenience.
Privacy-first
“But what about my biometric data? I can change my passwords, but I can’t change my fingerprints.”
The above rejoinder is a common one, but it’s based on a misconception. Your biometrics never leave the device the passkey was created on. Moreover, your biometrics are just used to unlock the private key on the device – the real authentication starts there.
So there’s no need to worry about attackers somehow stealing your fingerprint scan while it’s in transit in bits and bytes over the Internet. Your biometrics stay local. The FIDO standard also has requirements for both False Acceptance Rate (FAR) and False Rejection Rate (FRR) to ensure that incorrect users aren’t falsely accepted or correct users aren’t falsely rejected.
What’s more, passkeys are account-specific and cannot be used to track you across apps and websites. The standards used to build passkeys place a great deal of emphasis on privacy, and it shows.
Interoperable
Passkeys are built on standards such as FIDO2 and WebAuthn, which are a cross-industry effort with support from Google, Apple, Microsoft, and other heavyweights. There is room for improvement in terms of compatibility and interoperability, but the initial signs are positive.
You can create passkeys on multiple devices today. Providers like Apple even backup and sync the passkeys across devices if they use the same iCloud account. Around 95% of global user devices support the WebAuthn standard today, so it’s only a matter of time before the remaining compatibility gaps are fixed.
A comparison (there’s no comparison)
How do passkeys compare against passwords? It makes for pretty one-sided reading.
| Passwords | Passkeys |
User experience | Creating, remembering, managing, resetting passwords is a pain. | Using passkeys is identical to unlocking your device: fingerprint and face scans, PINs. |
Security | Passwords are the mayor of Phish City. They can easily be stolen by attackers. | Passkeys are unphishable. There is nothing for attackers to steal. |
MFA | Passwords need to be supplemented with additional auth factors since they are weak on their own. | Passkeys offer MFA (who you are, what you have) in one step. |
Dev / IT burden | Password storage, reset flows, and fraud prevention adds to dev and IT work. | Passkeys prevent server-side authentication sprawl and complexity. |
Passkeys are still young and have ground to cover. But technology shifts like this tend to be gradual and then sudden. With continued cross-industry backing, proper end user education, and developer enablement, passkeys will supplant passwords in the years to come.
We look forward to the day when World Password Day isn’t a thing anymore.
Drag-and-drop passkeys authentication with Descope
Interested in adding passkeys to your app or website? Poring over the protocols involved and implementing them correctly can be tricky. Descope’s drag-and-drop workflows help developers abstract away the complexity of authentication – while also making it frictionless and secure – so that app builders can spend more time building.
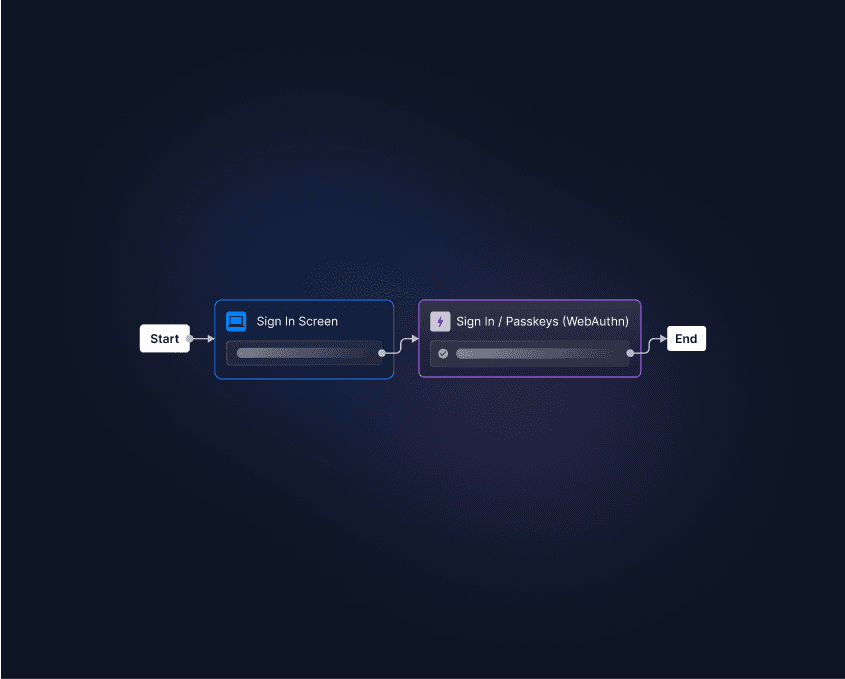
Sign up for Descope and start your app’s passkeys implementation today.






