Table of Contents
Physiological biometric authentication methods
The use of biometrics has surged in recent years, with the global market for related authentication and identification methods growing by nearly 15% annually since 2019. As the market size expands, so do the available biometric authentication methods.
From your digits to your DNA, there’s not much that modern technology can’t scan. To that end, if you’re thinking about implementing biometric authentication for your app, organization, or digital service, you can offer your users a range of options.
Physiological biometric authentication methods
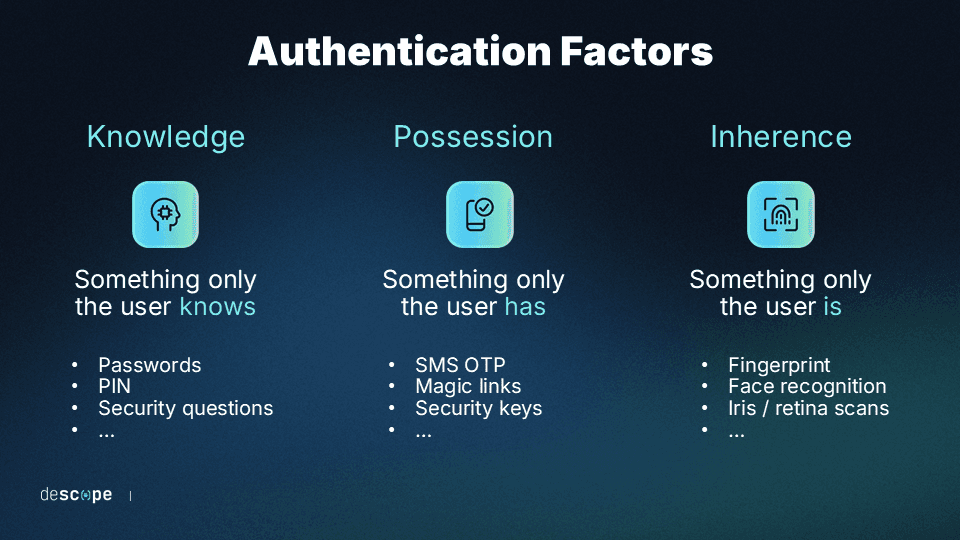
Modern authentication methods will test at least one of three possible variables when verifying a user’s identity:
Something the user knows
Something the user has
Something the user is
Consider the following examples of biometric authentication methods to determine which suits your purposes:
Facial recognition
Fingerprint scanning
Iris/retina recognition
Voice recognition
Hand geometry
Facial recognition
Facial recognition systems generally function by mapping a user’s facial features, then storing that information in a database. Then, when the user makes an authentication request, their face is checked against the biometric data saved in the repository to verify their identity.
Employing facial recognition technology to authenticate users offers a quick, effortless user experience (UX), which is why some of the most popular devices prefer it. It’s also hyper-secure — Apple’s Face ID has complex mapping procedures and depth-perceiving technology that make the chance of misreads less than one in one million.
That said, facial recognition may not work equally well for everyone. For example, a recent Harvard study found that age, race, and gender can affect the accuracy ratings of popular facial recognition software.
Thus, facial recognition is best used where it’s seen most often: to unlock phones and complete other less critical authentication tasks. If you’re using it for more complex functions, consider backing it up with a secondary authentication method to avoid misreads.
Fingerprint scanning
Fingerprint scans work similarly to facial recognition technologies, mapping the unique ridges of the user’s digit then checking it against stored data. Fingerprint recognition technology is around 99% accurate, and over 90% of modern devices have fingerprint-compatible capabilities.
Some individuals’ fingerprints, however, may not be as clearly defined as others. In such cases, users may have to scan multiple times or use another authentication method.
Nonetheless, fingerprint scanners have numerous applications. You can trust them for simple functions like unlocking devices and critical tasks like verifying identities for money transfers. Hence, you can find fingerprint-scanning technology everywhere, from banking apps to theme parks.
Iris/retina recognition
Iris recognition scans use infrared light to illuminate the user’s eye. A complex recognition algorithm takes a detailed scan of the iris, saves it in its database, and checks it against future authentication attempts.
Retina recognition, on the other hand, uses near-infrared irradiation to illuminate the blood vessels at the back of the eye and map out their unique pattern.
Both methods have extremely low false match rates, as ocular qualities are hard to duplicate. Thus, they’re cornerstones of authentication in high-security facilities, such as government and military compounds.
While ocular scanners are impressive and secure, their costs make them prohibitive for consumer purposes. So, while iris and retina scans may have a home in government entities and organizations, they’re still beyond the price point of the average app developer to be practical.
Voice recognition
If you’ve ever used a digital assistant to send a text or play a song, you’re familiar with the power of voice recognition technology. Speaker identification software creates profiles of users’ unique vocal characteristics to match against stored data for smooth and speedy verification.
Of course, voice recognition has its downsides, as anyone who has tried to use their digital assistant in a noisy environment (or with a sore throat) will tell you. These limitations, however, didn’t stop over 4 billion users from utilizing the technology in 2022.
From Alexa to Siri, voice recognition is best used for completing minor tasks on personal devices, as recent research has found that even the most sophisticated vocal recognition technologies can be fooled by impersonators. So, if sensitive information is involved, vocal cords are not necessarily the safest authentication tool.
Hand geometry
Like other biometric identification methods, hand scans function by mapping the unique characteristics of your hand and checking it against stored profiles.
Accurate hand geometry scans require specialized equipment, and scans taken on mobile devices yield less accurate results than other biometric authentication methods. Thus, from the Olympics to Disney World Resorts, the technology is primarily used by massive entities with significant security concerns.
In fact, with starting prices ranging in the thousands of dollars, palm scanners have limited consumer application. Other authentication methods are likely a better fit for the job unless you protect a sizable physical location or valuable goods.
Up-and-coming biometric authentication methods
While DNA-based identity verification may seem like works of science fiction, they already exist and are becoming more affordable and accurate. Soon, a drop of blood may be the quickest and most effective way to authenticate a user.
For now, however, other similarly futuristic authentication methods, such as gait and vein recognition, may make users feel like they're living in 3023.
Gait recognition
Identifying walking patterns has niche uses for law enforcement and related organizations. Generally, such software analyzes video footage to locate individuals based on the length of their strides, steps, and footprints. While some gait recognition software has results approaching 95% accuracy, it can easily be thrown off by individuals intentionally manipulating their walk.
For identification and authentication purposes, gait recognition helps search for missing persons or pursue criminals.
Vein recognition
The future is here for those who dream of unlocking their doors, devices, and digital services with a palm scan. Infrared palm scans penetrate the skin to map the unique web of veins beneath the palm’s surface. Vein scans can be highly accurate, with some technologies boasting correct recognition ratings of over 99.9%.
Due to its high accuracy, palm vein scans are the preferred authentication method of the national certification exam administrator, Pearson VUE. Like other methods that require expensive hardware, however, vein recognition as a whole is more suited to organizational applications rather than consumer use.
Factors to consider when choosing a biometric authentication method
When determining which biometric authentication method fits your needs, there are several considerations to keep in mind, including:
Security: Using secure biometric technology is paramount if you’re safeguarding extremely sensitive data, such as users’ banking information or trade secrets. Fingerprint scans, for instance, have a lower chance of being falsified than other widely-accessible methods, like signatures. Biometrics should be part of an MFA process that employs additional identification approaches.
Accuracy: If your service has a large volume of users, you’ll want to pick a method that can quickly and accurately differentiate between biometric markers without potentially confusing similar credentials.
UX: If a quick and effortless experience is paramount, easy-to-use and familiar technologies such as fingerprint and face scans present optimal choices.
Cost: For commercial and consumer-oriented apps, any solution requiring hardware beyond a standard mobile device may make the method cost-prohibitive for many users.
A note on FIDO authentication
Open standards such as FIDO2 and WebAuthn have rapidly gained adoption in the past few years. Passkeys – a consumerization of these standards – have been adopted by Google, Microsoft, Apple, Shopify, and others.
FIDO authentication uses asymmetric cryptography and biometrics to make authentication both secure and frictionless. Moreover, the biometric data never leaves the user’s device, making it virtually impossible for cybercriminals to conduct account takeover.
Adding passkeys to a consumer application offers a great balance between security and user experience.
Add biometric authentication to your app with Descope
With most mobile devices now natively supporting biometrics, applications that allow users to authenticate with a swipe of their finger can simplify onboarding, increase retention, and improve security.
Descope helps developers easily add biometrics to their apps using drag-and-drop workflows that abstract away the complexity of authentication, enabling app builders to spend more time building.
Sign up for Descope on our “Free Forever” tier and see how easy it is to build biometric authentication flows for your app.






