Table of Contents
What is TOTP?
Conventional passwords are among the least secure authentication methods developers can build into their apps and websites. Even though passwords continue to be widely adopted, they are steadily being supplanted by more secure and user-friendly passwordless options.
One way to prepare people for a passwordless future is using one-time passwords (OTP), which sound similar to their near-namesakes but offer much better security assurance. Looking beyond traditional SMS-based OTP, two common approaches worth comparing are TOTP and HOTP.
What is TOTP?
A time-based one-time password (TOTP) is exactly what it sounds like – a password that works once and only for a limited time. It’s a covert form of multi-factor authentication (MFA) that leverages a second device or account owned by the user to grant access to a given app, website, or other digital location. It’s safer and (arguably) easier than a conventional password.
The first step in any OTP protocol is registration. A shared secret (a seed) is generated and stored on the server when the user registers with the OTP platform. All OTPs generated in future login attempts will validate the user based on the same seed, even though the code will differ.
When users attempt to log in, the app or website will generate a code based on the seed and a moving factor. In the case of TOTP, the moving factor is based on Unix time, which means the OTP will expire if the user does not enter it within a given interval — commonly, this is set between 30 and 90 seconds.

The user can see this code on their authenticator app and input it in the relevant field. Independently, the server generates a code using the same seed and moving factor. If the codes inputted by the user and generated by the server match, the user is logged in.
With TOTP, there is no static password for users to memorize or for cybercriminals to guess or steal. However, the login process relies on the end user’s ability to input the OTP within the time allotted. That said, TOTP is much more secure than SMS authentication, which is more commonly vulnerable to MITM (man-in-the-middle), phishing, and other attacks.
What is HOTP?
HOTP is an abbreviation for another acronym, Hash-based Message Authentication Code (HMAC). HOTPs are HMAC-based one-time passwords, meaning that the moving factor is not the ticking hands of a clock but a counter that moves upon request. Specifically, the event iterates when a request is validated.
Otherwise, HOTPs function in almost the same way that TOTPs do.

At a base level, the one-time password via HOTP lasts longer than TOTPs, which hedges against some delivery issues or other logistical challenges that can render TOTPs inconvenient or unfeasible.
This is considered a convenience for end users since they have more time to log in before the OTP changes. However, that convenience comes at a cost, as HOTPs have a built-in vulnerability of leaving the door open longer for brute force and similar attacks.
Comparing HOTP and TOTP
Here’s how the HOTP vs. TOTP comparison shakes out:
| TOTP | HOTP |
|---|---|---|
Generation and Delivery | Codes based on the seed are generated and viewable on authenticator apps. | OTPs based on the seed are generated and viewable via authenticator apps or other hardware / software tokens. |
OTP Expiration | Upon delivery, OTPs only work for a given time (usually 60-90 seconds) until they expire. | After being delivered, OTPs will typically remain valid until used, with no expiration. |
Convenience | Users need to input the OTP within the time allotted. | Users can input the OTP at any point in the future. |
Security | TOTPs are more secure than passwords, HOTPs, and SMS authentication. | HOTPs are more secure than passwords but less so than TOTPs. They are vulnerable to brute force attacks. |
HOTPs and TOTPs are not entirely unique protocols from scratch; they’re two means of achieving the same end. Their differences amount to how the OTPs iterate: by time or event.
Choosing between TOTP vs HOTP
Choosing between TOTP and HOTP will depend on various factors:
Security requirements: TOTP provides higher security due to its time-based nature, reducing the window of opportunity for an attacker. If the company requires stricter security, TOTP might be the preferred option, especially as a second authentication factor for step-up authentication.
User experience: TOTP offers a smoother user experience since passwords are automatically generated, while HOTP requires manual entry. If user convenience is a priority, TOTP might be the better choice.
Time synchronization: If time synchronization between the server and the user's device is challenging or unreliable, HOTP might be a more suitable option. However, HOTP has its own synchronization challenges.
Implementation complexity: HOTP is generally easier to implement, so this might be a deciding factor if the company has limited resources or time.
You can often incorporate both, allowing users to choose the best method. However, these are relatively niche authentication approaches (especially HOTP), so be sure to provide adequate end user education if you do end up choosing both methods for your app.
Drag-and-drop TOTP auth with Descope
If you’re looking for a strong, device-based second factor for your application as a developer, consider implementing TOTP. With Descope, developers can seamlessly add TOTP authentication – or any other authentication method – to their app or website with no-code workflows.
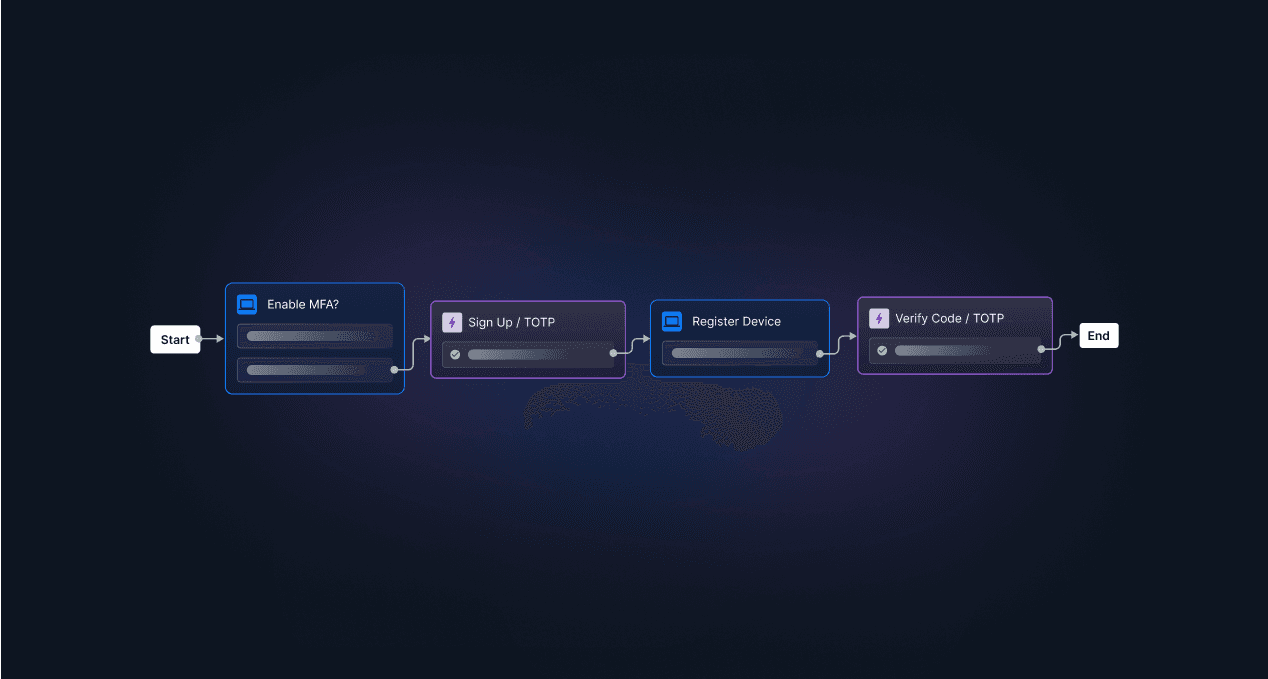
Sign up for a Free Forever account with Descope and drag-and-drop TOTP functionality into your next project.