Table of Contents
What are passwords?
In an ironic turn of events, Google announced its rollout of passkeys on World Password Day in 2023, proclaiming the “beginning of the end of the password.” But when it comes to the passkey vs. password debate, were they right?
In a word: probably.
Whether it’s because of passkeys or another form of passwordless authentication, experts tend to agree that apps on the Internet need to move away from passwords. To understand what this shift means for apps, websites, developers, and end-users, it’s essential to grasp the key differences between passkeys and their predecessor, along with the reasons why passkeys are considered superior.
Main Points
Passwords are familiar but flawed – They remain the default login method because everyone knows how to use them, but they come with serious usability and security weaknesses.
Passkeys solve those weaknesses – By replacing memorized strings with device-based cryptography and biometrics, passkeys eliminate phishing risks, reduce user friction, and offer stronger privacy.
The shift is already underway – Tech leaders like Apple, Google, and Microsoft are rolling out passkeys as the new standard, meaning organizations and developers need to prepare for a passwordless future.
What are passwords?
Passwords are the oldest and most common method of logging into digital systems. A user creates a string of characters (letters, numbers, symbols) and provides it alongside a username to access an account.
Here’s how it works behind the scenes:
The password is usually stored on the service’s server in hashed form.
At login, the user types their password, which the server hashes and compares against its stored value.
If the two match, access is granted.
Passwords are simple and familiar, and that’s their biggest advantage. Everyone knows how to use them, and nearly every system in the world supports them.
But they come with major drawbacks:
Human factors: Users often pick weak passwords, reuse them across accounts, or forget them entirely.
Security risks: Even strong, unique passwords can be stolen in breaches, guessed through brute force, or tricked out of users via phishing.
User friction: Managing dozens of credentials is frustrating and slows down the login process.
In short, passwords are easy to implement and familiar to users, but their weaknesses make them one of the riskiest authentication methods still in use today. Unless it’s paired with other requirements in a multi-factor authentication (MFA) flow, that is all a user—or cyber-attacker for that matter—needs to know to access sensitive data.
Read more: 4 Safest MFA Methods & Flows to Implement
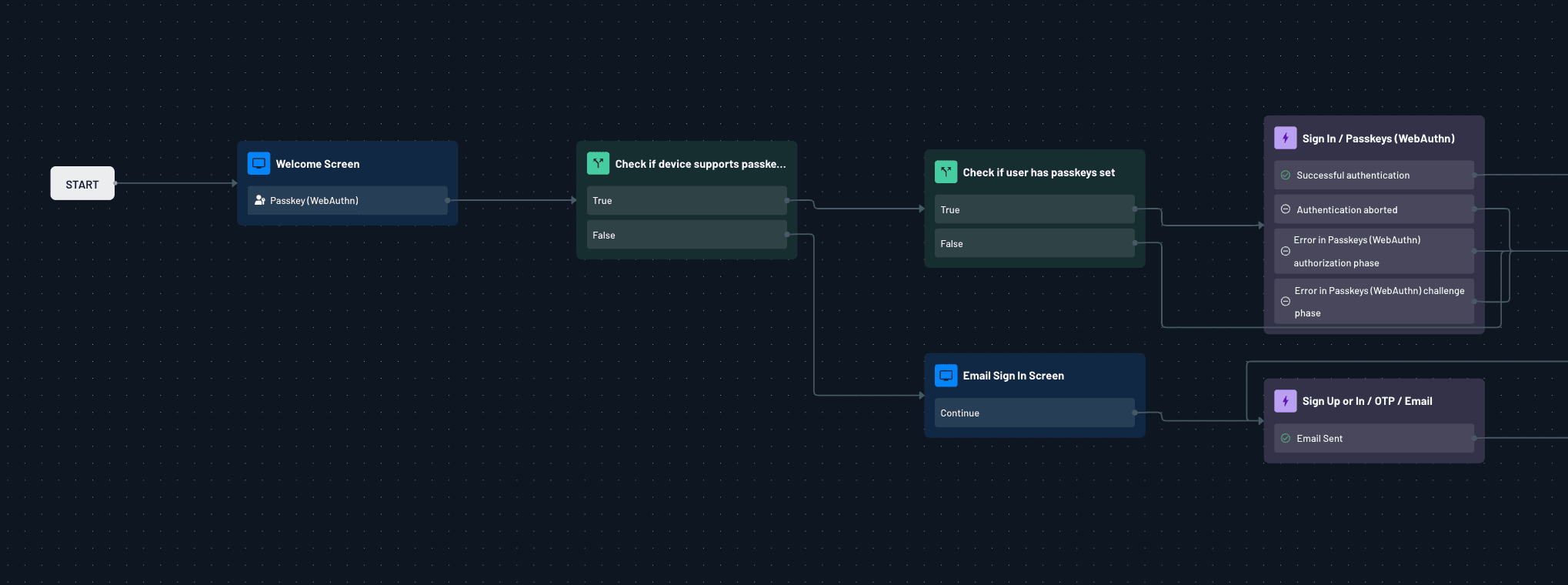
What are passkeys?
Passkeys are a new form of passwordless authentication that replace something you know (a password) with something you have (your device) and something you are (your biometrics).
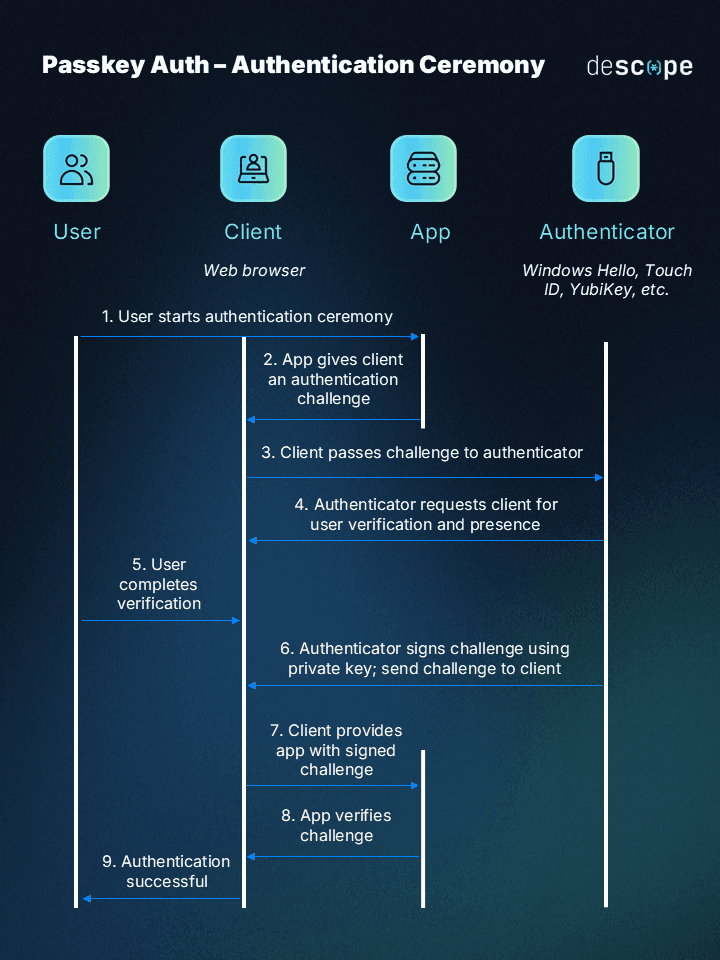
Here’s how they work in practice:
When a user sets up a passkey, their device (phone, laptop, tablet) generates two linked cryptographic keys:
A private key that never leaves the device and is protected by the user’s biometric or screen lock.
A public key that is safely stored on the service’s server.
When the user tries to log in, the service sends a challenge request. The device uses its private key to sign that challenge, and the server verifies it with the matching public key.
Because the private key never leaves the device, there’s nothing for attackers to steal or phish. And because the action usually requires a biometric check (like facial recognition, fingerprint, or a device PIN), only the rightful user can complete the login.
In simple terms: with passkeys, you don’t need to type or remember anything. You just unlock your device as you normally would, and cryptography handles the rest in the background.
Passkeys vs. passwords
At a surface level, passkeys and passwords serve the same purpose: verifying that the person trying to log in is who they claim to be. But the way they achieve that goal couldn’t be more different, and those differences have big implications for security, user experience, and implementation.
Here’s how the two compare across the factors that matter most:
Factors | Passkeys | Passwords |
|---|---|---|
Authentication | Public key cryptography + biometrics/screen lock | User-entered string of characters |
Security | Resistant to phishing, credential theft, and impersonation | Vulnerable to brute force, phishing, reuse, and breaches |
Convenience | Fast, no memorization, device-based unlock | Requires remembering/typing, often frustrating |
Implementation | Newer, requires dev integration (but resources are growing) | Built-in support across all systems |
Compatibility | Moving toward cross-platform standardization | Universally supported today |
Privacy | Biometric data stays on device | Passwords stored server-side, at risk in breaches |
Login Success Rate | Higher success rates (63.8% in Google trials) | Lower success rates (13.8% in same trials) |
Security
Passwords expose organizations to some of the most common attack vectors, including phishing, credential stuffing, brute force, and large-scale breaches. Passkeys eliminate shared secrets entirely, which means there’s nothing for attackers to steal or reuse. For businesses, this translates directly into fewer breaches, lower remediation costs, and reduced compliance headaches.
For example, PayPal observed a 70% drop in ATO attempts after introducing passkeys.
Privacy
With passkeys, biometric data never leaves the device. Only a cryptographic signature travels to the server, limiting exposure. Passwords, on the other hand, must be stored in centralized databases, which are prime targets in data breaches.
User experience
Passwords have long frustrated users with forgotten credentials, resets, and mistyped logins. Passkeys, by contrast, simplify the experience to a single biometric scan or device unlock. And the data is clear:
Login success rates: Microsoft reports a 98% success rate with passkeys compared to just 32% for passwords.
Speed: Microsoft also found logins with passkeys are up to 8× faster than with passwords.
Google’s early trials: In 2023, Google measured passkey logins averaging 14.9 seconds vs. 30.4 seconds for passwords.
Adoption in practice: Authsignal analyzed one million authentication attempts and found passkeys used in 62% of flows, surpassing SMS codes.
User perception: A 2025 FIDO Alliance study revealed 54% of users consider passkeys more convenient and 53% say they feel more secure than passwords.
For users, this means fewer headaches and faster access. For organizations, it translates into fewer helpdesk tickets, lower abandonment rates, and reduced fraud. The combination of smoother experiences and stronger security is a rare win–win.
Implementation
Passwords are nearly effortless to support because they’ve been the default for decades, but that simplicity comes with long-term costs: resets, fraud monitoring, and breach response.
Passkeys once required more effort, but that landscape has shifted. Thanks to standardized support across Chrome, Safari, Edge, Android, iOS, and Windows, organizations can now implement passkeys with APIs and SDKs from providers like Apple, Google, Microsoft, and identity platforms like Descope.
Read more: Managing Passkeys on Apple, Google, and Microsoft Platforms
Passkeys and passwords together with Descope
Passkeys outperform passwords across security, privacy, speed, and user experience. While passwords are familiar, they’ve long outlived their usefulness and the industry momentum behind passkeys makes their replacement inevitable. For organizations and developers, the question is no longer if you’ll adopt passkeys, but when.
If you’re building an app or modernizing authentication, Descope makes the transition simple. With drag-and-drop workflows, SDKs, and APIs, you can add passkeys (and even keep passwords for fallback if needed) with just a few lines of code—no reinventing the wheel.
Sign up for a Free Forever Descope account and simplify your authentication while saving developer time. Have questions? Book time with our experts.