Table of Contents
What is a magic link?
“Science is magic that works.” - Kurt Vonnegut.
Passwords are a hassle—forgotten, stolen, or reused across multiple accounts. Magic links offer a seamless alternative, allowing users to log in with a single click on a secure link. This passwordless approach eliminates friction while keeping security intact, making user authentication faster and more user-friendly.
But what exactly are magic links and how do they work? Let’s explain this magic trick and see if this is the right authentication method for your application.
Main points
Ditch the passwords: Magic links offer one-click secure access without the hassle of forgotten credentials.
Simple by design: Just open the email, click the link, and you're in—perfect for low-friction customer journeys.
Boost conversions: Reduce abandoned carts and boost sign-ups with smoother authentication flows.
What is a magic link?
Magic links are a passwordless authentication method using URLs with unique and time-limited embedded tokens to verify a user’s identity during the login process. These links are typically emailed to the users but can also be sent via SMS or other messaging platforms like WhatsApp. All the user needs to do is click or tap the link to authenticate and log into the account they’re trying to access.
If implemented correctly, magic link authentication greatly improves the user experience, reduces churn due to forgotten passwords, and increases app conversions. Users find magic links familiar because they have already interacted with similar (although much unhappier) flows whenever they reset their password.
They also work similarly to one-time passwords (OTP), except they are links instead of numeric PINs.
How magic link authentication works
Magic links work by embedding a token within the link's URL that is unique and time-limited. This token is associated with the user's account and is verified by the server when the link is accessed. Once the server confirms the token is valid and has not expired, the user is authenticated.
Here is what users see when they go through magic link authentication:
The user enters their email address in the app login page.
The user gets an email with a link.
Once the user clicks the link, they are logged in.
The simplicity of the steps above is probably how the “magic” moniker arose. But to make the magic happen, a few other things are happening under the hood. Here’s how magic links work in some more detail:
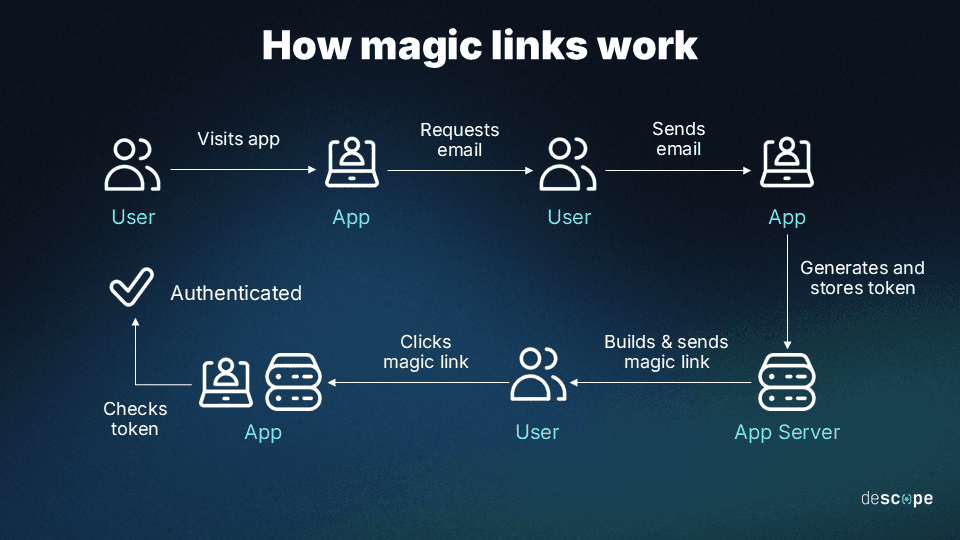
The user enters their email address in the application login page.
The email address is checked against the database to check if a registered user is trying to log in.
The application generates a token and embeds it in a magic link. The token is also stored for later validation.
The application sends the user an email with the link. Additional parameters can be added to the link, such as expiry time and session limits.
When the user clicks the link, the application checks the token.
The user is logged in.
If the steps above sound familiar, it’s because something very similar happens during password reset flows. While password reset links send users to a page to create a new password, magic links grant users one-time account access.
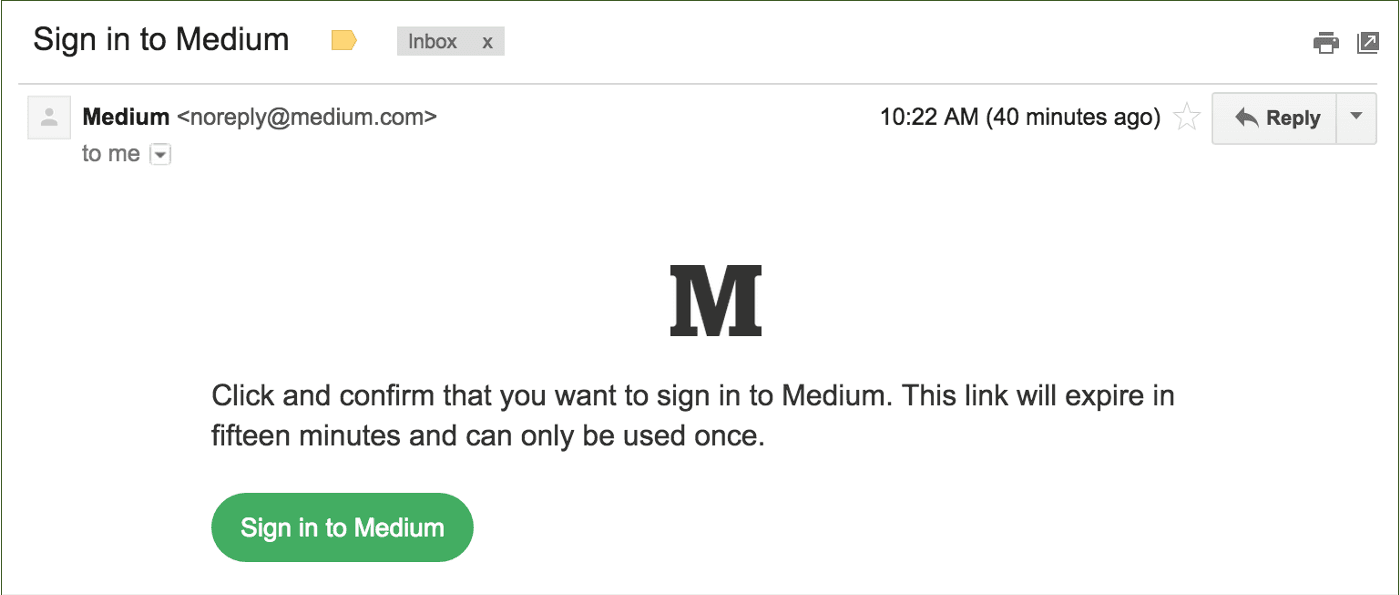
In recent years, magic link authentication has been adopted by many applications, including prominent examples like Medium and Slack.
Common uses of magic links
From seamless logins to secure payments and account delegation, here’s how organizations use magic links these days.
Password reset
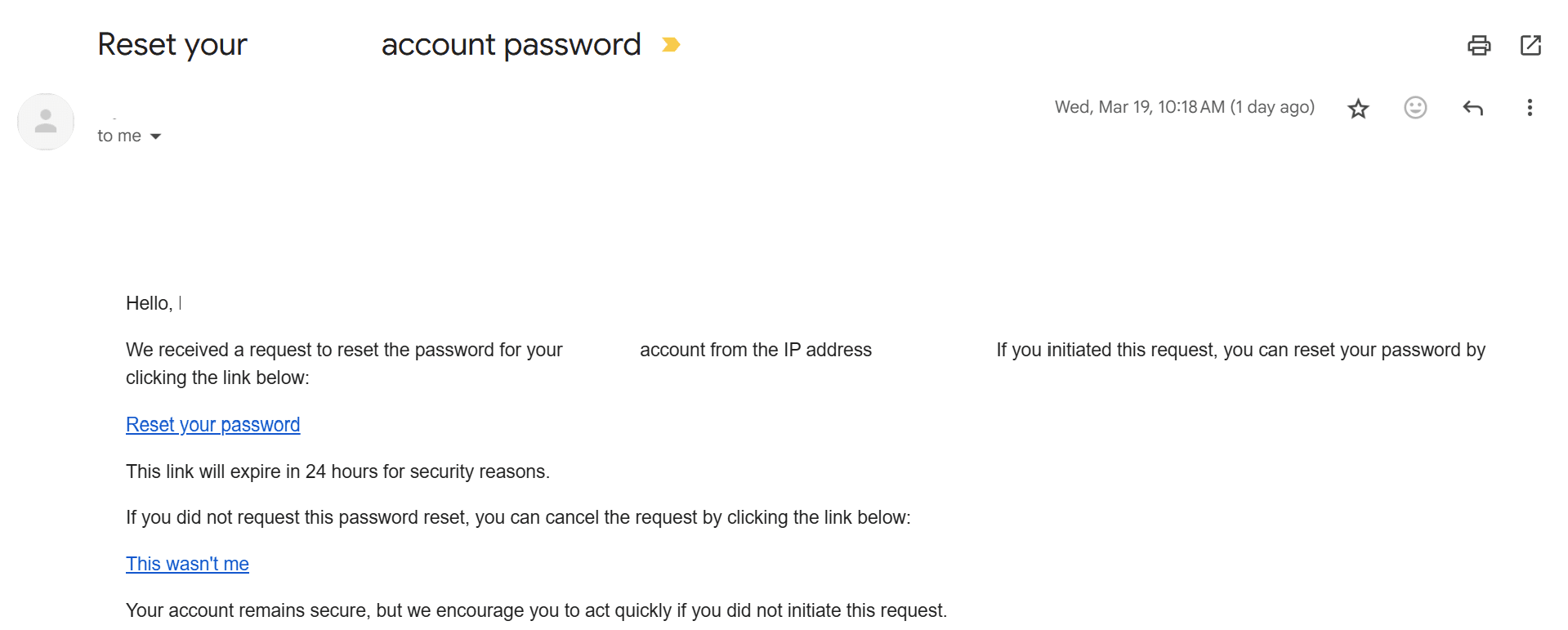
Password reset remains one of the most common use cases for magic links. Instead of relying on security questions or manually entering old passwords, users receive a unique link that directs them to a secure page to set a new password. This method bolsters security by eliminating knowledge-based authentication, which is often vulnerable to social engineering attacks.
One-time access
Magic links provide a seamless way to grant single-use access to resources such as shared documents, gated content, or virtual events. Once the user clicks the link, it expires, preventing unauthorized reuse. This approach simplifies authentication while reducing the risks associated with traditional credentials.
Automatic session renewal
To maintain long user sessions without requiring frequent logins, applications can generate and send magic links when a session is about to expire. Instead of forcing users to re-enter credentials, they can simply click the link to continue their session securely. This improves the user experience, especially for productivity tools, financial platforms, and media streaming services.
Read more: What Is Session Management & Tips to Do It Securely
Account delegation
Users can delegate limited access to their accounts without sharing credentials. By generating a magic link, they can grant temporary access to another person or service with predefined permissions and an expiration time. For example, embedded links can be used to allow one person to approve an action being conducted by another person. Other scenarios include:
Business accounts: Allowing assistants or team members to access specific resources.
Vacation scenarios: Letting someone manage an account in the user’s absence.
Customer support: Temporarily granting a representative access to troubleshoot issues.
Guest and temporary access
Organizations often need to provide short-term access to external collaborators, such as consultants or contractors. Magic links eliminate the need for creating and managing temporary credentials. Instead, a guest receives a time-limited magic link to access a resource, ensuring a secure and frictionless experience.
Group orders for shopping or delivery apps
Picture a delivery app where a group of people are all ordering together. Before the purchase goes through, the account owner has to click a magic link to place the order after everyone has put in their selections—or, the link can be triggered when the order amount crosses a particular threshold. This effectively gates the purchase behind an additional layer of confirmation.
Device authorization
For security-sensitive applications, magic links serve as an efficient way to verify new devices. Instead of requiring users to manually enter credentials or one-time passwords (OTPs), they can authenticate a new device by clicking a secure magic link sent to their registered email or phone. This is particularly useful for:
Cloud services: Simplifying multi-device access.
Banking and fintech: Reducing login friction while maintaining security.
Reducing cart abandonment
Abandoned shopping carts can be a significant issue for ecommerce companies, with research showing that nearly 70% of online shopping carts are abandoned before the purchase is completed.
Ecommerce brands use magic links to recover lost sales by sending personalized emails to users with abandoned carts. Instead of requiring a login, the email contains a magic link that:
Automatically logs the user in.
Directs them to their saved cart.
Applies a promo code instantly if included in the link.
Streamlines checkout with fewer steps.
This reduces friction and increases conversion rates, making it a powerful tool for online retailers.
Read more: Authentication in Ecommerce: Best Methods & CIAM Tips
Benefits of using magic links
Magic links make the lives of users, developers, and product owners easier.
Simplicity for Users | Users only need to access their email and click on a link, no need to remember passwords. |
Enhanced Security | Dynamically generated with a short expiration window, reducing the opportunity for attacks. |
Reduced Password Fatigue | Eliminates the need for users to remember multiple passwords, reducing password fatigue. |
Decreased Risk of Phishing | Direct communication via email reduces susceptibility to phishing compared to traditional passwords. |
Lower Password Reset Requests | Significant reduction in password reset requests, lowering support workload. |
Improved User Experience | Streamlines the login process, enhancing overall satisfaction. |
Reduced Development Complexity | May require less infrastructure and development effort than secure password systems. |
Cutting Down on Password-Related Vulnerabilities | Mitigates risks associated with weak or reused passwords. |
End users
Fast and seamless login experience. Users just need to enter their email address to log in to the application. There are also no hardware dependencies to use magic links, unlike some forms of possession-based and biometric authentication. Here, the email account is the “something only you have” for users.
Avoiding password pain: Users avoid the challenges and bad behaviors driven by passwords. There's no need for them to generate, memorize, or keep track of another password. This means they can avoid the cumbersome process of resetting their password — a common frustration when they inevitably forget it. Additionally, by not reusing passwords, they decrease the risk of their accounts being compromised in the event that a password is exposed due to a data breach in another application.
Developers and IT teams
Easy deployment: Since magic links follow a similar flow to password resets, implementing them usually only takes some minor code adjustments. Frameworks like Rails have also started including this functionality out of the box, further simplifying deployment.
Fewer support tickets: Support and help desk teams will no longer have to deal with the large volume of password-related support tickets. Magic links will also help reduce failed login alerts for the security team, especially false positives.
Reduced attack surface: With magic links, applications can free up infrastructure otherwise dedicated to encrypting, managing, and storing passwords. This also reduces the attack surface by making databases less attractive targets for adversaries.
Product and business owners
Reduce user churn: The login process is usually fraught with user friction, leading to churn and lost revenue. Magic links remove friction and can actually make the login experience an enjoyable one, increasing the likelihood of repeat user visits.
Increase conversions: Magic link authentication can help marketing and growth teams by reducing the number of abandoned cart transactions due to forgotten passwords. They can also be embedded in marketing emails and text messages, making them useful for sending reminders, discounts, and product updates.
Drawbacks of magic links
While magic links solve a lot of existing problems with password-based authentication, they bring some risks of their own.
Only as secure as the user’s email address: In theory, the user should be the only person with access to their email account. However, email accounts continue to be prime targets for phishing and credential stuffing attacks. An attacker who gains access to a victim's email account can use magic links to access other applications fraudulently.
Less admin oversight: Admins don’t have any visibility into the email account of the user. Thus, they cannot be sure if other people can also access the user’s email. If the user’s device is lost or stolen, bad actors can get access to their email and magic links.
Depends on the email service: Applications using magic links work with an email delivery service and are dependent on the reliability and performance of that service. Missed emails – or emails that go to spam folders – cause a bad user experience and can lead to drop-off.
Susceptible to some attacks: Although magic links remove many password-related woes, they also come with a few chinks in their armor. They are vulnerable to man-in-the-middle (MITM) attacks if users are on an unencrypted network, since attackers can steal the token and gain fraudulent access. As mentioned earlier, magic links can also be phished “by proxy”, since access to the email account can be phished.
When to use magic links
While magic link authentication has many use cases, it is not a one-size-fits-all approach. Here are some situations where magic links are a good candidate:
When user login is infrequent: Magic links are usually provided at the beginning of a user session and grant single-use access. This form of authentication is ideal when the user needs to log in only once or infrequently e.g. mobile apps, email accounts, and workforce collaboration apps like Slack.
When user account creation is a priority: Magic links remove friction from the user login process, which is usually a large source of churn. For organizations that are focused on getting as many users into the application as seamlessly as possible, magic links are a good option.
When another form of authentication is also present: As covered earlier, magic links are not immune to security risks if used on their own. However, pairing them with other forms of authentication such as passkeys or OTP reduces the likelihood and impact of these links being phished or compromised. Using magic links in a multi-factor authentication (MFA) flow enhances security while still providing a good user experience.
Read more: A Guide to User Authentication Methods
Magic links with Descope
It’s clear that businesses that adopt magic link authentication can benefit from increased user satisfaction and trust, while also strengthening their security posture.
In case you’re worried that adding, updating, and modifying magic links in your application's authentication flow would be time-consuming and costly – Descope makes it very easy for developers to add and customize magic links with the help of a drag-and-drop workflow editor, SDKs, and APIs.
Sign up for a Free Forever account to include magic links in your authentication flow today. Have questions about magic link implementation with Descope? Book time with our auth experts.






