Table of Contents
What is an OTP?
Safe, user-friendly user authentication has become increasingly important for organizations of all sizes. While password-based authentication has long been a standard method, evolving threats and user friction have led to the consideration of alternative options. One notable solution that has gained prominence is one-time passwords (OTPs).
This guide answers questions like what is an OTP, how does it work, and more.
What is an OTP?
An OTP—also known as a one-time PIN or one-time authorization code (OTAC)—is a unique, dynamically generated code that can only be used once to verify the user’s identity when attempting to log into their account. For increased security, OTPs expire after a short period and can’t be reused even if intercepted.
Unlike traditional passwords, OTPs aren’t static and change every time a user attempts to log in.
Thanks to their high security and ease of use, OTPs are often used as a secondary factor in a multi-factor authentication (MFA) flow.
Types of OTPs
There are two primary types of OTPs, each offering unique advantages and use cases: Time-based OTP (TOTP) and HMAC-based OTP (HOTP). Understanding the differences between these types will help you choose the most suitable option for your authentication needs.
Before going into the specifics of HOTP and TOTP, it’s important to understand how OTP generation algorithms generally work. Two inputs are used to generate OTP codes:
A seed. This static secret key is shared between the token and the server. It is created when a new account is established on the authentication server.
A moving factor. This is a component that changes every time a new OTP is requested. The main difference between HOTP and TOTP is how the moving factor is generated.
HOTP
The “H” in HOTP stands for Hash-Based Message Authentication Code (HMAC). The Initiative for Open Authentication (OATH) first documented and published it as RFC 4226 in 2005.
In HOTP, the moving factor is a counter incremented every time a new OTP is requested.
This counter is stored on both the token and the server. The counter on the token increments by one when a new OTP is requested. And the counter on the server increments by one when an OTP is successfully validated.

HOTP is user-friendly since it doesn’t increment until the user requests a new OTP, making it suitable for scenarios where time synchronization might be challenging. This means the user has ample time to enter the OTP. However, this also makes HOTP more susceptible to brute-force attacks.
TOTP
Published as RFC 6238 by the Internet Engineering Task Force (IETF) in 2011, TOTP's moving factor is based on time rather than incremental counters. The OTP changes after a specified period, called a timestep, usually between 30 to 90 seconds.
TOTP is generally more secure than HOTP and tough to crack with brute force attacks. However, the user has to input the passcode before it refreshes, which comes with the possibility of time drift. To remedy this, the authenticating server must make it easy for users to input a new OTP if the previous one expires.
Understand the difference better: TOTP vs HOTP: A Complete Breakdown

Common OTP delivery methods
Here are the most popular OTP delivery methods in use today:
SMS
Email
Messaging apps
Hardware keys
Authenticator apps
SMS
SMS authentication lets users log in by entering an OTP sent to their registered phone number via text message. It verifies users with a possession-based factor (their mobile phone).

Sending OTP via SMS is convenient for users because it doesn’t require them to learn new behaviors or get new hardware. However, it is vulnerable to SIM swapping and man-in-the-middle (MITM) attacks, where adversaries can intercept text messages and gain fraudulent account access.
Although SMS authentication is still widely used, it has been met with security objections. In 2016, NIST proposed deprecating SMS as an out-of-band second authentication factor.
Email OTP works like SMS authentication, except the users get the OTP sent to their email address instead of their phone number. Similarly, it verifies users with a possession-based factor (their email account).
Almost everyone has an email account and accesses it regularly, making email OTP very convenient. However, the security of email OTP is linked to the safety of the email account. If attackers gain access to a victim’s email account after phishing or credential stuffing, they can use email OTPs to cause further damage.
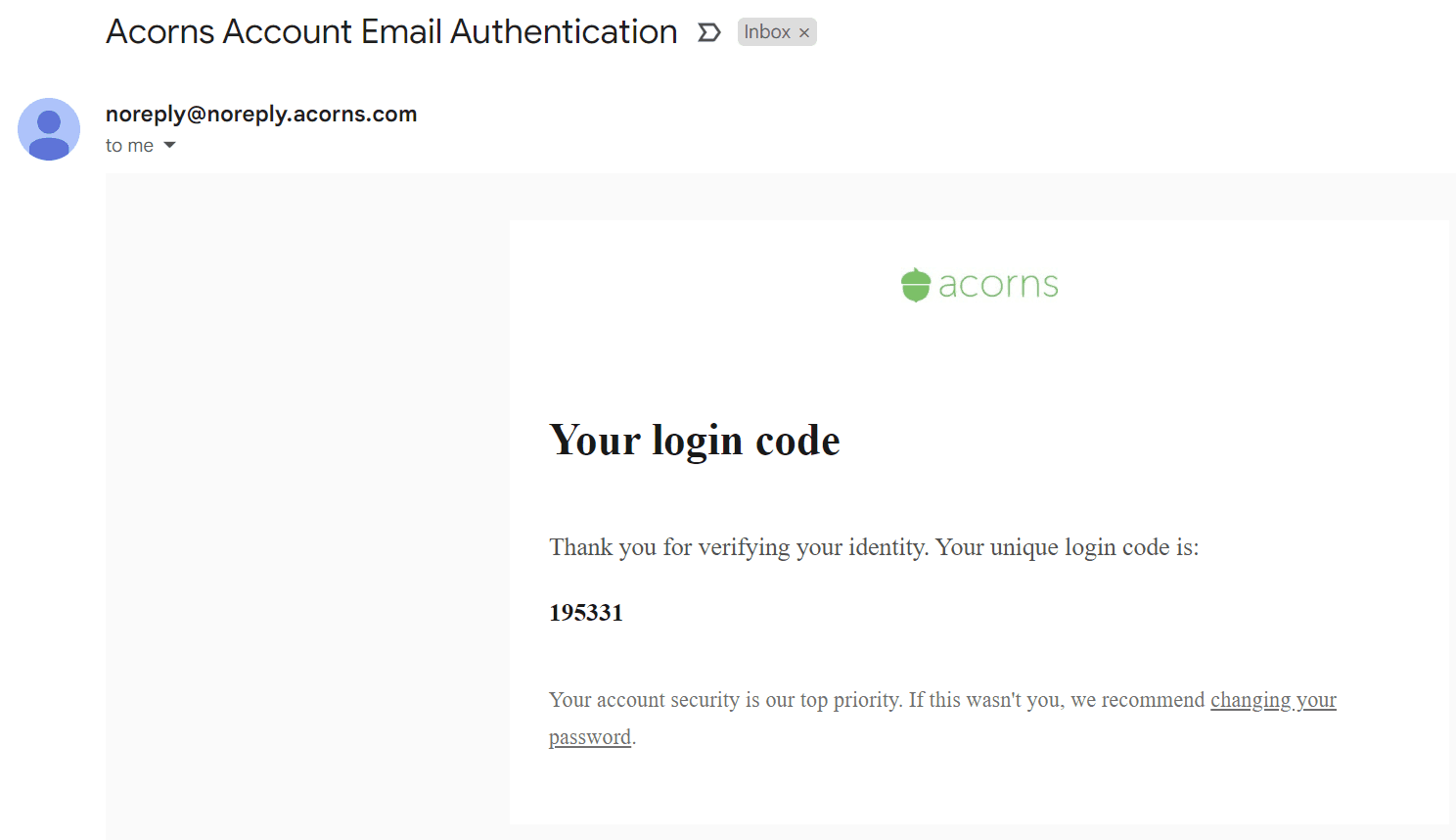
WhatsApp and other messaging apps
Over the past few years, services have begun using messaging apps such as WeChat and WhatsApp for OTP authentication. Choosing whether to send OTPs over SMS, email, or other messaging apps is often a function of two things:
Which method users are most comfortable with
Which method has the most reliable delivery rates

WhatsApp and similar messaging apps offer several advantages:
Enhanced security: With end-to-end encryption, WhatsApp provides robust security against MITM attacks, keeping OTPs secure.
Broader accessibility: Unlike SMS, messaging apps like WhatsApp operate over both cellular networks and Wi-Fi. This dual capability provides accessibility even during international travel without additional roaming charges.
Cost-effectiveness: Messaging apps can reduce costs associated with traditional SMS services, which is particularly advantageous for businesses seeking to scale their user authentication strategy without significant expense.
Learn more: Introducing nOTP: Single-Click WhatsApp Authentication
Hardware keys
In enterprise settings, OTP authentication is sometimes driven by dedicated hardware such as key fobs, smart cards, and Yubikeys. These devices generate OTPs based on a cryptographic key stored on the server. The server and the hardware device synchronize based on the shared secret key and independently generate the same OTP to validate the user’s login attempt.
Cybercriminals would need physical access to the hardware key before doing any damage, which is very unlikely. This makes hardware keys a very secure form of OTP authentication. A U2F security key reduces the attack surface since the OTP never leaves the token.
However, hardware keys impose restrictions on users since they must always carry the key on their person. Hence, this method is usually employed in workforce settings, particularly in sensitive industries such as government and finance.
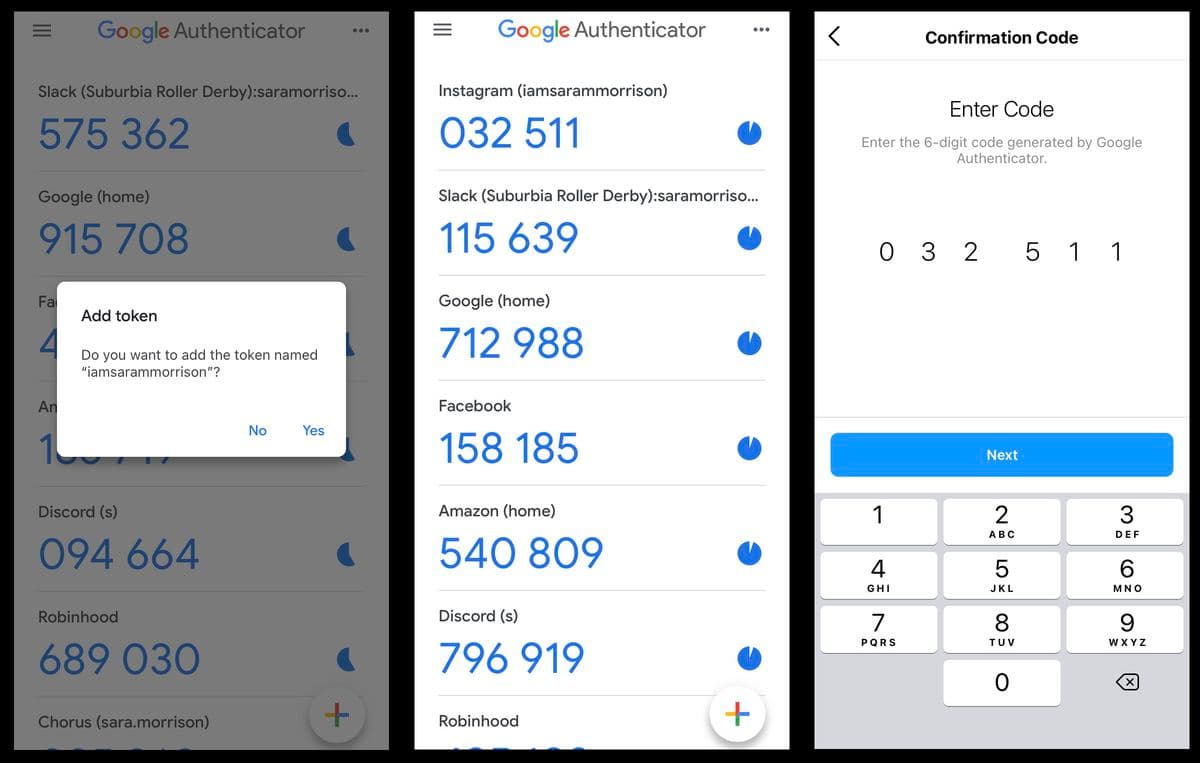
Authenticator apps
Software tokens can also perform OTP generation. Unlike hard tokens and security keys, these are not separate physical entities that users must possess. Instead, they are built into authenticator applications like Google Authenticator, Microsoft Authenticator, and Authy.
Mobile authenticators can be used for both enterprise and consumer contexts. These apps also do not depend on internet access or wireless carriers, making them usable in various scenarios. Authenticator apps that support biometric authentication add a strong second factor and protect users even if their device gets stolen.
Authenticator software uses the TOTP algorithm to perform time-based OTP generation and validation.
Benefits of using OTPs
OTPs are a vital component of the larger MFA market, which is projected to grow to $40 billion by 2030. OTP adoption will continue growing because it benefits both organizations and end users.
Safer than just using passwords
OTPs are meant for one-time use, which makes them resistant to replay attacks where the attacker intercepts and records data (like a static password) to use later. Using OTPs as a second factor reduces the risk if and when user passwords get stolen.
Protection against replay attacks: OTPs are valid for a single use, so they cannot be reused even if intercepted.
Limited validity: TOTPs expire quickly, reducing the window for misuse.
Dynamically generated: Unlike static passwords, OTPs change with each use, making them harder to guess or hack.
Primed for wide adoption
OTPs can be easily integrated into an authentication flow. Users like OTPs because they don’t need to be remembered and usually don’t require new hardware. Users are already familiar with common OTP delivery methods and don't need to learn new behaviors to use them.
User-friendly: Most people are familiar with receiving OTPs
No complex setup: Most delivery methods require no additional software or hardware from users.
Perfect to level up security measures
In addition to logging in, OTPs can be used as a factor in risk-based authentication. For example, a user can be asked for an OTP before they complete a high-value transaction on a banking app. Risk-based MFA gives users enhanced security without impacting their overall experience.
Drawbacks of using OTPs
There is no authentication silver bullet, and that includes OTPs. Here are some risks to keep in mind while using OTPs:
Depends on delivery rates: OTPs sent to users using SMS, email, and other messaging apps depend on reliable delivery. Missed messages, delayed texts, and email OTPs going to spam folders can lead to a poor user experience and drop-off.
Uses shared secrets: The seeds used in OTP generation are shared secrets, which is never an ideal security practice. Shared secrets make the server an attractive target for attackers. If they steal the secrets, they can generate passcodes to fraudulently access user accounts.
Susceptible to some attacks: As covered earlier, OTPs can be phished regardless of the delivery method. SMS authentication is prone to SIM swapping and MITM attacks. Email OTP depends on the security of the email account. Even TOTPs from authenticator apps can be stolen by motivated attackers in phishing and social engineering attacks.
Read more: Phishing-Resistant MFA Explained
Use cases of OTP across different industries
OTP authentication is widely adopted and used across the public as well as private sector to enhance security and provide a good user experience. Here are some of the top industries that commonly utilize OTP authentication:
Finance and banking: The finance and banking industry relies on OTPs to secure online banking transactions, money transfers, and account access. OTP helps prevent unauthorized access and financial fraud. Learn more about customer identity and access management in banking.
Healthcare: Healthcare organizations use OTP authentication to secure patient records, comply with HIPAA regulations, and ensure that only authorized personnel can access sensitive medical information.
E-commerce: Online retailers use OTP authentication to secure user accounts and transactions, particularly for high-value purchases. This helps protect customer data and prevent fraudulent activities. Learn more about ecommerce authentication.
Government: Government agencies use OTP authentication to secure online portals and citizen services, such as tax filing, voting systems, and access to government databases. This enhances data protection and prevents unauthorized access to sensitive information.
Technology and IT services: Many technology companies and IT service providers implement OTP authentication to secure access to their platforms, databases, and cloud-based services. This helps protect valuable data and intellectual property.
Telecommunications: Telecommunication companies use OTP authentication to secure customer accounts and protect sensitive information, such as call records, billing details, and account settings.
Easily add OTPs to your authentication flows with Descope
Adding OTP authentication to your app while taking care of all the security nuances can be time-consuming for developers who are also busy building core app functionalities. Descope helps developers easily add OTP authentication to their apps with no-code workflows, SDKs, and APIs. All via your preferred delivery method.
Descope as an OTP authentication provider allows you to drag-and-drop secure authentication flows and onboard users quicker than ever.
Sign up for a Free Forever account or book time with our auth experts for a demo.







