Table of Contents
What is MFA?
In an era defined by escalating digital threats, the significance of robust security measures cannot be overstated. Enter multi-factor authentication (MFA), a formidable defense mechanism that strings together multiple authentication methods.
Multi-factor authentication adoption has grown over the years. The security benefits are clear: Adding MFA can block over 99.9% of account compromise attacks. In addition, MFA has been found to stop 96% of bulk phishing attempts and three out of four targeted attacks.
But what is MFA and how does it work? Let’s find out.
What is MFA?
Multi-factor authentication (MFA) is a security system enforced at login, requiring the user to provide at least one additional proof of identity besides a password to be granted access to the service. For example, a user
The purpose of MFA is to create a layered defense and make it more difficult for bad actors to gain unauthorized access. So even if one factor is compromised, they still have at least one more barrier to breach.
MFA vs 2FA: What’s the difference?
MFA is often referred to as two-factor authentication or 2FA. 2FA is an authentication process where the user must present two different forms of identity proof before they are allowed to access a service. For example, logging into an account using a password and then verifying the identity with a one-time passcode sent to the user’s phone is 2FA
2FA is essentially a subset of multi-factor authentication. While 2FA requires exactly two authentication factors, MFA uses two or more factors depending on the sensitivity of the resource being accessed, the risk profile of the user, and so on.
Benefits of MFA
MFA isn't just about adding a couple of extra authentication steps; it's a powerful shield that brings an array of benefits to the table.
Improved security
MFA adds a crucial layer of defense against password-related attacks, such as credential stuffing or phishing, and brute force attacks. So even in the unfortunate event of a data breach, where passwords are exposed, MFA mitigates the risk. Stolen passwords alone become insufficient for unauthorized access, as the attacker would require the additional authentication factors to take over victim accounts.
Read more: Phishing-Resistant MFA Explained
Enhanced user experience (when done right)
When implemented thoughtfully, MFA can strike a balance between security and user convenience. With various authentication methods available in the market today, app developers can choose options that suit their end users’ preferences while maintaining a high level of security.
Using methods such as passkeys / biometrics for MFA is very convenient for end users since it only involves a swipe of a finger or a quick face scan. At the same time, these methods are some of the strongest available from a security perspective.
Using risk-based MFA is another way to balance security and UX. Frequent and low-risk users can log in to apps with single-factor authentication, with the additional factor only being requested when the system deems the login attempt to be suspicious or fraudulent. This approach does not tax legitimate users with MFA upon every login while also ensuring that security controls are present at the right time when needed.
Regulatory compliance
Many data protection regulations, such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA), emphasize the importance of robust security measures. Implementing MFA aligns with these regulations and helps you meet their security requirements.
Additionally, certain industries like finance and healthcare have specific compliance mandates. For instance, the Payment Card Industry Data Security Standard (PCI DSS) requires strong authentication mechanisms. MFA assists in fulfilling these industry-specific compliance obligations too.
How MFA works
As mentioned before, MFA works by asking the users for two or more verification factors to prove their identity when logging into a system. The process starts with the account registration:
Registration: The user creates an account and sets up additional verification methods beyond the username-password combination.
Login attempt: The user enters their username (or other identifying information) and password as the first layer of authentication. The system checks the first factor, and if correct, the process moves to the next step.
Additional authentication factors prompt: Depending on the level of security required, the user will be prompted to provide one or more additional authentication factors, usually a one-time code received via SMS or authenticator app, and a fingerprint or facial scan.
Access granted: The system checks this additional information to ensure it matches the expected input. If it is correct, the system authenticates the user and they’re granted access. If the second factor is incorrect or missing, access is denied.

This orchestrated user verification sequence ensures that even if an attacker obtains one factor, they cannot proceed without the second or third. Thus, MFA acts as a sophisticated gatekeeper, effectively mitigating the risk of breaches that exploit single-factor vulnerabilities.
Types of MFA factors
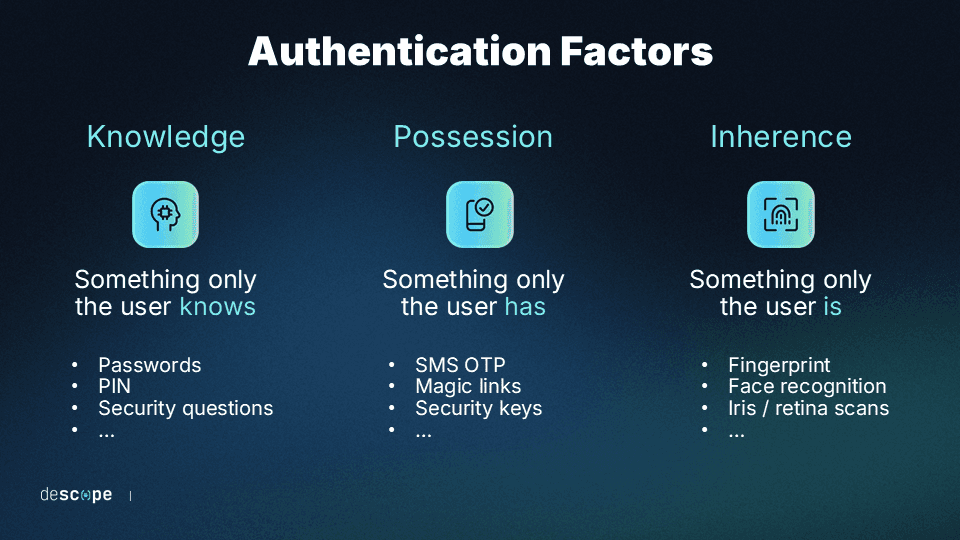
There are three generally accepted types of authentication factors used in MFA:
Knowledge: Something only the user knows.
Possession: Something only the user has.
Inherence: Something only the user is.
Knowledge
The knowledge factor refers to a piece of information known only by the user trying to gain access. The most common example is a username and password combination. Other examples include security questions like “What is your mother’s maiden name?”, PIN codes, and Social Security numbers.
Knowledge-based authentication (KBA), especially when used on its own, is prone to compromise.
Attackers can gather answers to security questions by researching potential victims on social media or employing social engineering techniques. An infamous example that showed the shortcomings of KBA was when Sarah Palin’s email account was hacked. Attackers found the answers to the account’s password recovery questions (birthday, ZIP code, etc.) after basic online research.
Possession
The possession factor refers to a device, physical token, or online account only possessed by the user trying to gain access. Common examples include SMS authentication and TOTP apps (where the mobile device is what the user has), email OTPs and magic links (where the email account is what the user possesses), and physical security keys like YubiKey.
Combining knowledge and possession factors is the most common MFA flow in use today. Even if attackers know a user’s password (the first factor), they would also need to possess the user’s mobile device or email account to gain full access to the user’s account. Not impossible, but much more unlikely than if the user was only using passwords and nothing else.
Inherence
The inherence factor refers to immutable biological traits that can identify only the user trying to gain access. Common examples include Apple Face ID and Touch ID, Windows Hello, retina scans, and other forms of biometric authentication.
Inherence is a powerful authentication factor, particularly when paired with specifications like WebAuthn. These forms of authentication are often used in phishing-resistant MFA.
Also read: What Is MFA Bypass and How to Prevent It
Other MFA factors
In addition to the three main authentication factors listed above, organizations and developers often use context-based factors, like:
Location: Location-based MFA considers where the user is attempting to log in from. This might include capturing the user’s IP address or geolocation. If a login attempt is made from an unusual location, the system might trigger an additional authentication step.
Time: This factor takes into account when the user attempts to log in and how it differs from their usual patterns.
These factors are usually employed in high-security settings or when applications need to evaluate risk before approving sensitive user actions (e.g., accessing customer data or wiring money).
Subsets of multi-factor authentication
MFA has different subsets that focus on adjusting the authentication process based on various factors and risk levels. Two of them are step-up authentication and adaptive authentication – advanced techniques that aim to provide a balance between security and user experience. Here's a closer look:
Step-up authentication
Step-up authentication, also known as route-based or “just-in-time” authentication, is a subset of MFA. It’s where users are asked for an additional authentication factor before being allowed to access sensitive data or perform high-risk actions. Step-up authentication is an effective way to reduce user friction during sign-up and initial adoption without sacrificing security.
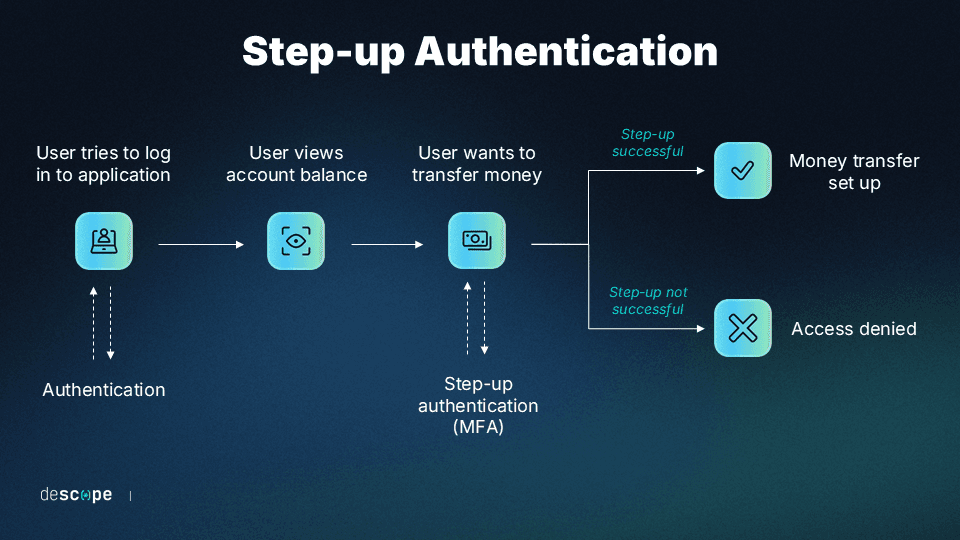
Rather than front-loading all authentication to the login stage, step-up authentication allows users to access certain resources with one set of credentials while protecting other resources behind additional sets of credentials.
For example, a banking service that logs users in with a password might allow users to check their account balance, deposit checks, and perform other low-risk actions without requiring more credentials. But when users want to move money around or make wire transactions, the app can prompt them for additional credentials by sending an OTP to their phone or email account.
Adaptive authentication
Adaptive authentication is another subset of MFA where additional authentication factors are automatically triggered according to a user’s risk levels. Adaptive authentication is also known as adaptive MFA, risk-based MFA, or risk-based authentication.
While step-up authentication is usually static and based on predefined flows, adaptive authentication is dynamic. It can prompt a user based on a risk score that includes a variety of behavioral and contextual signals. These user behaviors might include:
Where the user is
What time the user is trying to log in (and whether it’s different from the baseline)
What device is being used (and whether it’s different from the usual device)
Whether the user is on an encrypted or unencrypted network
For example, let’s consider a user that regularly logs in to an application from their laptop at home but then goes on an international trip. When the user tries logging in to the same application from an Internet café abroad, they’ll be prompted in real time for additional credentials because too many behavioral signals have changed from the baseline.
MFA in a snap with Descope
Adding MFA to an existing app is a non-trivial exercise and can take your development team weeks (if not months) of effort. Descope helps developers easily add MFA to their authentication flows with drag-and-drop workflows, SDKs, and APIs.
By utilizing third-party connectors such as Google reCAPTCHA Enterprise and Traceable in Descope authentication flows, developers can also add intelligent risk-based MFA that checks user risk scores and presents additional auth factors only when the risk passes a specific threshold.
If you are looking to simplify and uplevel your MFA implementation, sign up for a Free Forever account with Descope and follow us on LinkedIn for more updates. Have questions about our platform? Book time with our auth experts.





