Table of Contents
What is federated authentication?
Businesses are constantly looking for ways to improve the security and login experience of their apps, websites, and other user interfaces. By now, most people are familiar with processes that leverage one account to log in to different environments. But what often goes unnoticed by users and adopters alike is the underlying technology that allows for this streamlined approach.
Enter federated authentication, an innovative approach that not only enhances security but also streamlines the user experience. Federated authentication is generally what empowers seamless login to many different digital environments through one account with a trusted platform. It’s a one-size-fits-all solution.
What is federated authentication?
Federated authentication (fed auth) and federated identity management (FIM) are closely related concepts, often used interchangeably. Both involve using a single set of credentials to access multiple online accounts and services.
Federated authentication specifically refers to the process of using one authentication event to gain access to multiple systems or services across different domains. It's like having a master key that works for various locks.
By leveraging the trust networks between these entities (called federations), developers reduce the burden of password and credential management on end users.
One of the best-known and widely used examples of fed auth is when users log in to websites or apps using their personal or professional Gmail credentials. That streamlined process relies on the trust between the app or website (i.e., Netflix) and its federated partner (Google).
FIM is a broader term that encompasses the management of user identities and their permissions across different systems and organizations. It includes elements of authentication, authorization, and trust relationships between entities.
Federated auth vs. SSO: What’s the difference?
Like fed auth and FIM, fed auth and single sign-on (SSO) are often used interchangeably as they are similar. Namely, both allow users to access content across multiple platforms through one login.
But there are essential differences between federated authentication and SSO in terms of how that happens:
Federated authentication offers users access to multiple websites, apps, and systems across lines, like their company’s tech stacks or other closely-associated pieces of software that traditionally work together. Imagine you have a bunch of doors to different rooms. Federated authentication is like having a master key that opens all those doors with just one touch. You use this key once, and it works for all the entries.
SSO is more about granting access to these closed groups of software. SSO is like a VIP pass to a specific party. It lets you in to a group of related places or systems with just one set of credentials.
To that end, SSO is typically tied to enterprise environments, whereas FIM is widely applicable.
While FIM and fed auth are often considered a kind of SSO, the relationship works the other way around: SSO should be regarded as a more limited subset or application of FIM technology.
How federated authentication works
Federated authentication and FIM rely upon relationships of trust between service providers (SPs), websites and apps using fed auth for user accounts, and identity providers (IdPs), such as auth servers.
In practice, fed auth functions similarly to other passwordless auth methods:
Users attempt to log in to their account with the SP
The service provider requests fed auth from an IdP
The IdP authenticates the user’s identity and notifies the SP
The user is granted access to their account on the SP’s platform
To authenticate the user’s identity with the IdP, the user may need to be logged in to their account on the IdP’s platform. Alternatively, attempting to log in to the SP’s platform may trigger an authentication with the IdP.
In either case, the end user only needs to log in to one platform, which grants them access to countless others.
B2B Enterprise Readiness Checklist
Score your tech stack on enterprise readiness pillars - from dev and IT experience to security and architecture.
Download
Common protocols used for federated auth
On a more technical level, how SPs and IdPs communicate to verify users’ identities and authorize access relies on specific protocols. The most commonly used ones in federated authentication are:
Security Assertion Markup Language (SAML): SAML uses Extensible Markup Language (XML) to streamline the communication of identity data between web-based IdPs and SPs.
Open Authorization (OAuth 2.0): OAuth 2.0 is an authorization protocol that uses JSON Web Tokens (JWT) to grant access without requiring a new account.
OpenID Connect (OIDC): OIDC is an identity layer built on top of OAuth2. It authenticates users with JWT with enhanced security via strong encryption and greater applicability across business applications, web-based software, and mobile applications.
In fed auth, these protocols exist in harmony. It’s not a matter of OAuth vs. SAML or OIDC vs. OAuth. Instead, the best fed auth solutions support all of these protocols so that a wide range of customer applications can avail these services.
Read A Guide to User Authentication Methods
Benefits and drawbacks of federated authentication
Federated auth leads to improved user experience, with fewer frustrating login attempts and a lesser overall burden of memorizing account credentials. This translates into smooth, efficient identity and account management at scale with greater security and lower general expenses.
The biggest benefit of federated auth is bringing SSO-like functionality to a broader variety of apps, websites, and digital environments, rather than the select group SSO enables. For example, fed auth can allow a single login to link Apple, Google, and Microsoft accounts.
Federated authentication also enables apps to have two identity providers, with the federated IdP providing some functionality that the primary IdP might lack. For example, Descope can be used as a federated IdP with Auth0 to add passkeys functionality to existing Auth0 logins.
And, unlike many SSO solutions, fed auth does not involve designing costly bespoke software.
However, like SSO, fed auth systems feature a single point of failure. If a user’s account with the identity provider is compromised, risks may spread within the federated software ecosystem. However, prudent implementation and vigilant management can effectively mitigate these challenges. Moreover, IdPs are often experts in identity security: it’s a better choice for application developers to hand off these security responsibilities to third-party experts rather than building and maintaining them in-house.
Who is federated authentication best for?
As noted above, fed auth is similar to SSO concerning its functionality but has fewer limitations regarding its applicability. Here are the contexts in which federated auth is commonly used:
Multiple identity providers
Federated auth is very useful when applications need to unify identities across multiple identity providers. Say an app already uses IdP 1 but wants to add IdP 2 for some use cases, or say an app wants to use IdP 1 for the first authentication factor but IdP 2 for MFA flows. In any of these cases, federated authentication ensures that:
Both IdPs fulfill their intended roles
User accounts are securely merged whenever required
The primary IdP doesn’t need to be changed even when a second IdP is added
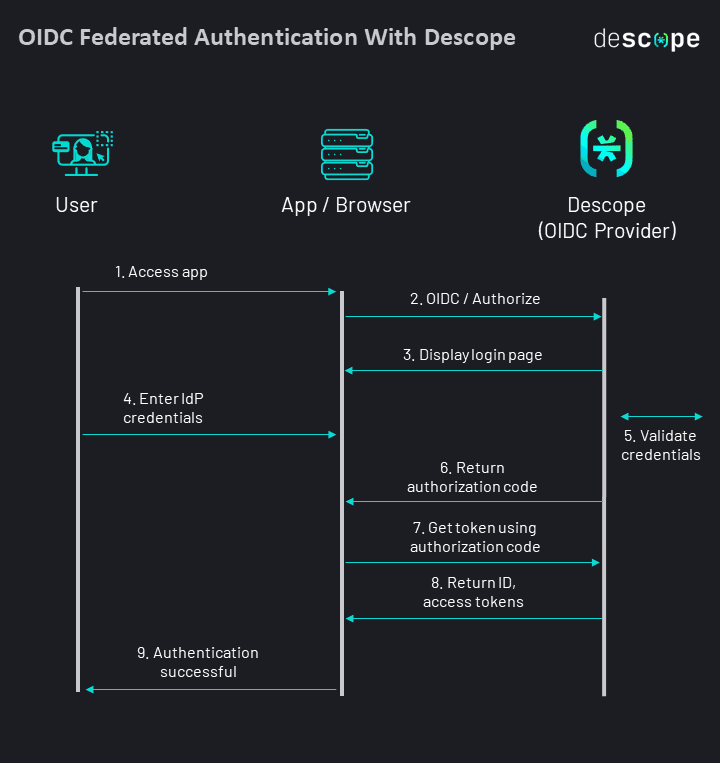
The figure below shows a simplified view of OIDC federated authentication:
Multi-service environments
Fed auth can be used in environments in which organizations have multiple services, applications, or websites that require user authentication coming from a single, unified source. For instance, a university with separate systems for email, online courses, and library access could enable students and faculty to use their university credentials to access all these services seamlessly.
Collaborative environments
Fed auth can be used when multiple departments or entire organizations need to share resources across a suite of applications or websites. Consider a creative agency working on a project involving designers, writers, and marketers. Fed auth enables each team member to use their respective accounts to access project management tools, design software, and content platforms, ensuring smooth collaboration without the hassle of managing multiple logins.
Cloud-based services
Federated authentication can be effective when organizations rely upon cloud-based applications or services from various providers and need to streamline login to cloud environments. For example, consider a startup that relies on various cloud-based services like customer relationship management (CRM), project management, and file storage. Employees can use their company credentials to log in to these services, eliminating the need for separate logins for each platform. This simplifies user management and enhances security by maintaining centralized control over access.
Enterprise mobility and BYOD environments
Environments in which staff use multiple devices, including personal devices, and need reliable, secure access from them are good candidates for federated auth. For example, consider a corporation where employees use their personal smartphones and laptops for work-related tasks. In a Bring Your Own Device (BYOD) environment, fed auth allows employees to access company resources and applications from their own devices securely. They can use their company credentials to log in, ensuring a balance between convenience and security.
Ultimately, any environment anticipating needing to authenticate users across many accounts and contexts seamlessly and securely should consider federated auth.
No-code federated authentication with Descope
Descope supports OIDC federated authentication for a wide variety of use cases.
Want to add passkey authentication to your existing logins with Amazon Cognito, Auth0, or Firebase?
Want to add SSO to your Retool apps?
Want to integrate authentication with server-side rendering (SSR) frameworks such as Next.js, Nuxt.js, and SvelteKit?
All of the above (and more) can be easily implemented by using Descope as a federated OIDC provider. Sign up for a Free Forever account on Descope and start your federated authentication journey today. Got questions? Join AuthTown, our open user community for developers to learn more about authentication.





