Table of Contents
What are authentication protocols?
In today's digital age, we rely on technology for many aspects of our daily lives. Therefore, protecting our identities (and those of our customers) is more important than ever. One of the fundamental tools used to ensure online security are authentication protocols. These protocols serve as gatekeepers, verifying our identities and allowing us access to protected information and services.
This guide will explore the protocols used to authenticate online identities and discuss how to choose the right one for your application.
What are authentication protocols?
Authentication protocols define how claimants (users trying to access a digital service) and verifiers (the entities authenticating them) communicate. Essentially, these protocols involve a message exchange that verifies the validity of the authentication service and verifies that the claimant possesses the appropriate token to authenticate their identity.
The information users provide to verify their identity is known as the authentication method. Some examples include passwords, one-time passwords (OTP), and passwordless authentication methods like magic links and biometrics.
Authentication protocols are the standards by which verifiers make sense of these methods and can operate in several ways.
How authentication protocols work
During an authentication process, like when a user logs in to a digital service, they must prove their identity to the verifier. Authentication protocols dictate the type of information needed for the authenticating service to verify the user and how it’s delivered.
Imagine being asked for identification to receive a delivery in a foreign country. You hand the courier your license, but they don’t understand its formatting or language and cannot make sense of its information to confirm your identity.
In the digital world, authentication protocols ensure that the recipient (user) and courier (verifier) always speak the same language to avoid situations like this. And like actual languages, different authentication protocols have their own rules. However, there are some standard techniques that most of them use, including:
Encryption involves scrambling data so that only parties with access to a special key can understand it. Encryption is crucial during authentication as it helps prevent sensitive information from being leaked or stolen. Authentication protocols provide tools that make it possible to encrypt and make sense of data sent between claimants and verifiers.
Hashing uses algorithms for shortening strings of data into more manageable sizes. Like encryption, only parties privy to the algorithm can make sense of a hashed data string. Thus, hashing provides similar protection when used as a basis for authentication protocols.
Digital signatures are encrypted authentication stamps that prove information from a specific sender hasn’t been altered. In authentication protocols, they’re used to confirm that it’s genuinely the claimant trying to access a service rather than an online attacker.
Generally, most systems will use one or more of these techniques to make sense of authentication requests. However, the exact methods used to verify users’ identities vary between authentication protocols.
Common authentication protocols
There are many authentication protocols to choose from when developing login systems for your app. Each comes with different features, advantages, and disadvantages. Let’s explore some of the most popular authentication protocols.
Kerberos
Kerberos is a widely-used and well-established network authentication protocol that has had many iterations in its over 20-year history. It uses secret-key cryptography to encrypt and store credentials, then decrypts and verifies them when issuing ticket-granting tickets (TGTs) from a key distribution center (KDC).
This encryption method is highly secure, meaning senders and recipients can safely deliver messages to one another even if the privacy of their network connection is questionable.
The main drawback of secret-key cryptography is the need to distribute the key to users, as malicious actors could also gain access. However, once a claimant has the key, it becomes extremely difficult for online attackers to decrypt information sent using Kerberos protocols.
Kerberos can support numerous authentication methods, such as passwords and Single Sign-On (SSO). Plus, it can integrate seamlessly into many popular platforms, including Windows OS, Amazon Warehouse Services, and iOS.
Challenge-Response
Challenge-Response refers to a class of authentication protocols in which the verifier provides the claimant a challenge (e.g., a query). The claimant must then respond correctly (e.g., the right answer).
While minds may jump straight to “What was the name of your first pet?” and other common security questions, that’s not quite how Challenge-Response works. These protocols most commonly function by generating a code, securely sending it to the user, and then requiring them to enter it on a server or platform. Hence, authentication methods such as OTPs commonly rely on Challenge-Response protocols.
While ever-changing passwords provide extra protection from individuals trying to intercept data, this protocol’s consistent re-authentication process can lead to poor user experience (UX).
OAuth / OpenID Connect
OAuth, short for “Open Authorization,” is not intended for authentication. Rather, it’s a framework that allows users to share their private resources with another application without divulging their personal identity information.
OpenID Connect (OIDC) is an open standard that overlays OAuth for authentication purposes.
To achieve authentication, OIDC employs an ID token that includes relevant details about the user and their authentication status. Additionally, OIDC enhances the standardization of scopes and claims, making it easier for different systems to communicate with each other.
This improved interoperability facilitates the sharing of user authentication states and profile information among different systems reliably.
Security Assertion Markup Language (SAML)
SAML is an authentication protocol that employs Extensible Markup Language (XML) to standardize the exchange of identity information. In SAML-based protocols, there are three main players:
The user
The Identity Provider (IdP), usually a third-party service that specializes in authentication
The Service Provider (SP), which is the platform the user is trying to access
When the user attempts to log in to the SP, it creates a SAML request that redirects them to the IdP’s page. Next, the IdP verifies the user’s credentials, generates a SAML response noting the request’s legitimacy, and sends it back to the SP. Then, if the SP confirms the response's digital signature is genuine, the user is granted access.
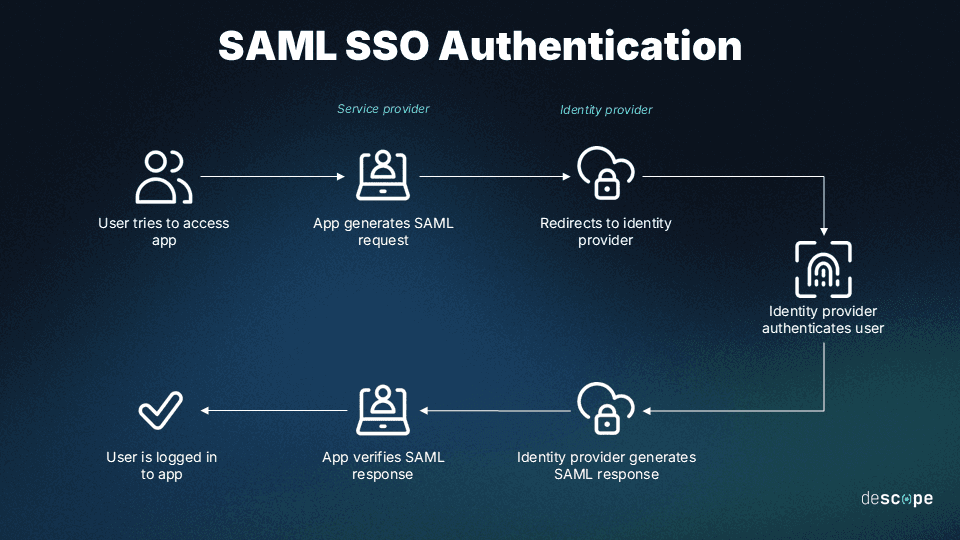
SAML takes the burden of authentication off SPs, instead leaving the task up to professional services. Such specialists reduce the risk of breaches, enabling developers to work on other tasks.
SAML is most often used to power SSO authentication. SAML SSO allows users to employ a single secure login to access a company’s digital services. While this results in a convenient UX, SSO has shortcomings, such as identity thieves being able to access all of a user’s accounts with one set of credentials.
FIDO2 / WebAuthn
FIDO2 is an open standard that allows users to log in to applications on desktop and mobile environments without passwords. FIDO authentication (developed by the Fast IDentity Online Alliance) employs registered devices or FIDO2 security keys to verify users’ identities, replacing traditional password-based methods.
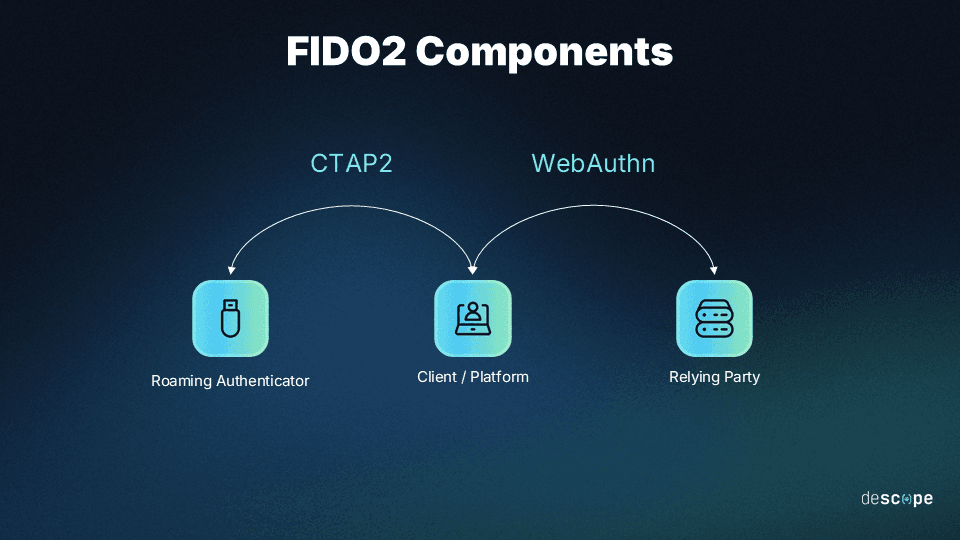
FIDO2 comprises two components:
The Web Authentication API (WebAuthn), which permits applications to authenticate users through possession-based and biometric authentication.
The Client to Authenticator Protocol (CTAP), which facilitates communication between the client and a roaming authenticator, like a hardware security key or smartphone.
In 2019, the World Wide Web Consortium (W3C) declared WebAuthn the official web standard for password-free logins. Around 95% of global user devices support this authentication standard.
Time-Based One-Time Password (TOTP)
TOTP refers to a time-based one-time password or passcode, which grants users single-use access to an application. An algorithm utilizes a shared secret and the present time as inputs to generate a TOTP code.
TOTP is implementable through both hardware and software tokens. A hardware TOTP token is typically a physical device or security key with a screen displaying the current code. On the other hand, a software TOTP token comes in the form of an authenticator application installed on a mobile device (such as Authy or Google Authenticator) that presents the current code on the phone screen.
Unlike passwords, which remain fixed and can be stolen with ease, TOTP codes change at predefined intervals (usually between 30 to 90 seconds) and are incredibly difficult for attackers to compromise. This attribute makes TOTP authentication an effective second factor in two-factor authentication (2FA) or multi-factor authentication (MFA) procedures.

Choosing an authentication protocol
There are several factors to keep in mind when choosing an authentication protocol for your app. These include:
Security levels – Authentication security should be a priority for any app, since user information getting stolen can have far-reaching ramifications for the business.
Integration – If you already have a build or a set idea of what your app will look like, consider an authentication protocol you can easily integrate into your current structure.
Scalability – Ensure that whatever protocol you pick can handle more users as your platform grows in popularity.
Authentication method – Ultimately, authentication protocols are used to power authentication methods. Therefore, selecting one compatible with the login experience you want to provide your users is essential.
While each developer’s situation is unique, some protocols are better suited for specific use cases. To help guide your decision, consider these basic guidelines:
Consider SAML if you are building a business app for enterprises and looking to add SSO.
Consider WebAuthn for consumer apps and mobile-first apps since fingerprint and facial recognition is native to most devices. It’s already been adopted by users to unlock their devices, leading to increased familiarity.
Analyze your users’ preferred identifiers to choose the appropriate authentication method and, in turn, authentication protocol. For instance, if your users provide phone numbers, consider OTP, TOTP, or SMS magic links. If your users provide email IDs, consider email OTP or magic links.
Consider social logins (OAuth) from reputed IdPs such as Google and GitHub to prioritize quick user registrations while getting validated information.
Whichever authentication protocol you choose, consider using it as part of a multi-factor authentication method (MFA) to give your app a secure UX that utilizes the most popular and effective technologies.
Remove auth protocol complexity with Descope
With a better understanding of authentication protocols, you’re better equipped to choose the right one for your app. However, poring over these protocols and ensuring you implement them correctly without potential vulnerabilities is still tricky.
Descope’s drag-and-drop authentication platform abstracts away the complexity of authentication protocols to help developers easily add secure, frictionless login to their apps. Descope supports a wide range of authentication protocols (SAML, OAuth / OIDC, TOTP, WebAuthn) for consumer and business apps.
Sign up for Descope today and “descope” authentication protocols from your daily work.






