Table of Contents
How does authentication work?
In 2022, identity theft-related data breaches compromised the personal information of over 400 million individuals in the United States. Many of these attacks can be attributed to gaps in user authentication, which place sensitive data security at risk.
Authentication is the process of verifying the identity of a user or device attempting to access a particular application or system. The goal of authentication is to ensure that the user or device is who they claim to be and to prevent unauthorized access.
Authentication typically involves the use of one or more authentication factors, such as a password, a smart card, a fingerprint, or a device such as a phone/laptop. The user or device attempting to access the application must provide the correct authentication factors to prove their identity and be granted access.
Authentication is a critical component of information security and is used in a wide range of applications, from logging in to a computer or website, to accessing a secure facility, to making financial transactions. By requiring users to authenticate, organizations can help protect against data breaches, fraud, and other types of cyber attacks.
Authentication vs authorization
While authentication provides access to digital environments by verifying the validity of users’ access credentials, authorization distinguishes between the levels of access these credentials provide.
For instance, companies typically require employees to log in to their accounts using some form of authentication. Once logged in, these employees have predefined privileges that authorize them to access certain environments but not others.
Learn more: Authentication vs Authorization
User authentication vs machine authentication
Authentication applies to both users and the devices they use.
As the name suggests, user authentication requires users to provide access credentials. Similarly, machine authentication prompts devices to prove their identity to access the application.
Machine authentication is required if a network’s security is configured to authenticate new devices before granting them access. Machine-to-machine communications may also be required when two backend services need to interact. One way to achieve this is with the client credentials grant flow in the OAuth framework.
How does authentication work?
Authentication manages access to digital environments by requiring users or devices to prove their unique identities before gaining access. And for user authentication to be effective, unique identifiers must be present to distinguish one user from another.
For instance, password-based authentication requires users to input a unique combination of characters into an access control gateway (e.g., a login screen) before accessing a digital environment.
Although passwords are widely used forms of authentication, they are susceptible to broken authentication risks, which cybercriminals can exploit.
Unlike the password-based option, passwordless authentication is more effective, even when using the same principle of validating user identity based on unique identifiers. Rather than using knowledge factors (something the user knows), passwordless authentication uses a combination of possession factors (something the user has) and inherence factors (something the user is).
Passwords and other knowledge factors (like security questions) are weak authentication factors because the attacker just has to “know” the same thing the user does in order to impersonate them and take over their account. This type of compromise is much less likely for possession factors (e.g. stealing someone’s phone or laptop) and inherence factors (e.g. trying to spoof someone’s fingerprint).
For all forms of authentication, failure to provide the unique identifiers required to validate user identity will prevent users from accessing systems, networks, or applications.
Types of authentication
Now that we’ve explored what authentication is and how it works, let’s dive into the various types of authentication your business can leverage.
Password-based authentication
Password-based authentication is a method of verifying a user's identity by requiring them to enter the password associated with their account.
To authenticate with the system, the user enters their username and password, which are then compared to the stored values in the system's database. If the username and password match, the user is granted access.
Although this is the most common type of authentication due to its simplicity and convenience, it is also probably the least secure. Passwords can be easily forgotten, stolen, or guessed, especially if the password is weak or reused across multiple systems.
Token-based authentication
Token-based authentication is a method of verifying a user's identity by requiring them to present a token that is associated with their account. The token is a physical device or a digital file that contains a unique identifier, such as a smart card, USB key, or a software token.
Token-based authentication provides an extra layer of security compared to password-based authentication, as the physical token is harder to steal or replicate than a password. They are often used in situations where strong authentication is necessary, such as accessing sensitive data or performing financial transactions.
However, although tokens are a reliable method of authentication, they are more expensive and less convenient. They can be lost, stolen, or damaged, so users must take appropriate measures to safeguard them.
Certificate-based authentication
This method verifies the user’s or machine’s identity by using digital certificates. A digital certificate is an electronic document typically issued by a trusted third-party authority. They contain the user's digital identity, a public key, and the digital signature of the certification authority.
As digital certificates are difficult to forge or steal, certificate-based authentication is considered to be highly secure. Usually, it’s used in enterprise environments dealing with sensitive data. However, it is more complex to set up and manage than other authentication methods, so it’s not the most convenient method for wide use.
Multi-factor authentication (MFA)
MFA requires users to verify their identities using one or more factors (which may or may not include a password) at the time of login. Two-factor authentication (2FA) is the most common version of MFA, with only two identification factors needed.
With rapidly growing application security risks, more businesses are starting to rely on MFA to secure their applications against cybersecurity threats.
Passwordless authentication
Passwordless authentication refers to a range of authentication methods used to verify a user's identity without the need for passwords. Instead, passwordless authentication uses a combination of possession and inherence factors, such as:
Magic links – A URL sent via text message or email containing a token that allows the user to log in without requiring a password when they click on it.
One-time passwords (OTP) – Unique, dynamically generated codes with numbers and/or letters that grant one-time access to the user.
Authenticator apps – An authenticator app is a software application installed on the user’s device that generates time-based one-time passwords (TOTP).
Biometrics– A physical trait unique to the user, such as fingerprints, voice, face, etc.
By removing passwords, passwordless authentication reduces the risk of unauthorized access, making it superior to other methods. Additionally, it’s more convenient for users, as they no longer need to remember complex passwords.
Passwordless authentication is used in a variety of applications, including online banking, e-commerce, and enterprise environments. As technology continues to advance, passwordless authentication is likely to become more widespread as a secure and convenient alternative to traditional passwords.
What are authentication factors?
Authentication factors are the identifiers used to verify a user or device attempting to access a system or application. These factors can be broadly categorized into three main types:
Something the user knows, such as passwords, access codes or PINs
Something the user has, like their mobile device or email account
Something the user is, for example, voice or fingerprints
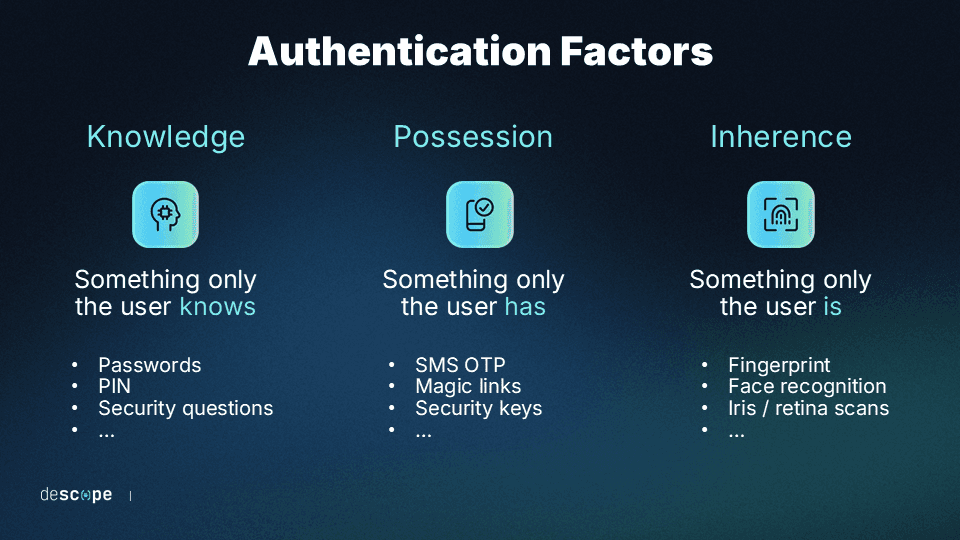
These factors can be used for password-based or passwordless authentication.
As a best practice, app developers should identify the most secure and robust authentication factors, depending on industry use and application.
Password-based authentication can be strengthened using unique keys, as in the case of 2FA or MFA. However, passwordless authentication is much stronger because it uses a combination of unique keys or physical features to secure applications.
Importance of authentication
Authentication is critical to securing users’ sensitive data, whether it’s stored on networks, applications or systems. According to Verizon’s 2022 Data Breach Investigation Report, over 50% of data breaches were a result of stolen access credentials.
This means authentication was likely broken in these scenarios, placing users’ data at risk for attacks like credential stuffing and account takeover.
Implementing authentication helps mitigate these risks and helps businesses secure their data in the long term. In most instances, application security depends on the robustness of identity and access management, which likely reflects the rigor of authentication controls.
Higher-level authentication, such as the passwordless one, reduces the cybersecurity risks typically associated with relying on password-based security.
And with more users demanding secure solutions that will safeguard their data, businesses must step up to ensure they secure the applications they provide customers.
Seamless and frictionless authentication is also critical for a positive user experience on any application or website. Clunky authentication processes can lead to subpar onboarding, user churn, and cart abandonment. It’s important for app developers to strike the right balance between security and convenience in their authentication flows and user journeys.
Easy and secure authentication for your app
For businesses looking to develop high-end, secure applications, passwordless authentication is the go-to solution. Descope helps developers easily add a range of passwordless authentication methods to their apps with no-code workflows, freeing up their time to focus on other core areas.
Sign up for Descope and drag and drop your auth.






