Table of Contents
What is CIAM?
Managing how customers log in, access services, and trust your brand with their data isn’t just a technical necessity—it’s a competitive edge. According to the FIDO Online Barometer Report, 60% of US users give up accessing an app because they forgot their password. You definitely don’t want to lose that many customers—and sales.
Customer Identity and Access Management (CIAM) blends security and convenience, offering features like streamlined logins, data privacy controls, and advanced authentication options. But it’s not without its challenges.
How can businesses balance robust security with a frictionless user experience? Let’s find out!
What is CIAM?
Customer Identity and Access Management (CIAM) is a specialized framework that manages the registration, authentication, and access control of an organization’s external identities. It prioritizes both data security and user experience, catering specifically to stakeholders outside the internal workforce. These external users often include customers, contractors, suppliers, partners and end users not directly employed by the organization.
CIAM tools help organizations provide secure, seamless authentication and user journeys for their customers while reducing the workload for engineering and IT teams. For end users, CIAM typically manifests in familiar processes like signing up, registering, and verifying their identity during logins.
For organizations and developers, however, CIAM involves a variety of user identity-related tasks, including:
Collecting user information: Names, phone numbers, emails, and any relevant documentation.
Secure data storage: Ensuring personal information is kept in a safe repository.
Managing login procedures: Enforcing Multi-Factor Authentication (MFA) or other authentication methods.
Monitoring login activity: Analyzing login attempts against stored credentials to prevent unauthorized access.
Controlling user access: Determining which features or services are available to different users.
Delegating management: Allowing users to handle certain aspects of their identity, like password resets or privacy settings.
The capabilities of different CIAM platforms vary, but they’re often at least partly the solution for an app’s security, user management, and authentication needs. While some CIAM solutions provide on-premise support, most are Identity-as-a-Service (IDaaS) platforms hosted on the cloud.
CIAM vs. Identity and Access Management (IAM)
Much like CIAM, Identity and Access Management (IAM) is a set of tools that verifies identities and controls access to digital platforms. Both solutions perform similar functions, including:
Protecting sensitive information: Ensuring only authorized users have access.
Verifying identities: Matching user credentials against stored records.
Managing access levels: Granting permissions based on a user’s role or authorization level.
Despite these overlapping functions, a few key distinctions exist between CIAM and IAM. Simply put, IAM solutions are primarily used for employees and internal stakeholders, whereas CIAM is designed for customers and external stakeholders.
| CIAM | IAM |
|---|---|---|
Users | CIAM is generally used to manage an organization’s customer base and other external stakeholders. | IAM solutions control access permissions for employees, contractors, and other internal stakeholders. |
Priorities | CIAM solutions balance security with UX to appeal to a larger audience that can choose which systems they use. | IAM solutions generally aren’t public-facing; they prioritize security over functionality, intuitiveness and user experience (UX). |
Use Cases | Popular CIAM use cases include customer authentication, customer SSO, and adaptive MFA. | Popular IAM use cases include employee SSO and user provisioning in HR systems. |
Gartner Buyers Guide for CIAM
Learn common CIAM use cases and recommended evaluation criteria.
Get copy
How does CIAM work?
Robust CIAM solutions are highly adaptable, designed to meet an app’s specific needs and developers' preferences. They offer a wide range of tools for security, identity verification, and authentication, including:
Customer registration and profile creation
Support for a variety of authentication protocols and methods
Self-service account management
Fine-grained access management and authorization
Data access governance
Directory services
Federated authentication and single sign-on (SSO)
Preference and consent management
The specific CIAM capabilities an app employs will depend on its purpose and design. For example, ridesharing platforms may use CIAM to:
Simplify user and driver registration by verifying identification or sending a code to their mobile number.
Securely store sensitive user data in a trusted Identity Provider (IdP) database.
Enforce security measures like risk-based MFA, trusted device checks, and session timeouts.
Control user access to features, enabling tiered subscription services.
Analyze customer behavior to optimize the onboarding and login experience.
Allow users to manage their accounts, including updating phone numbers or passwords.
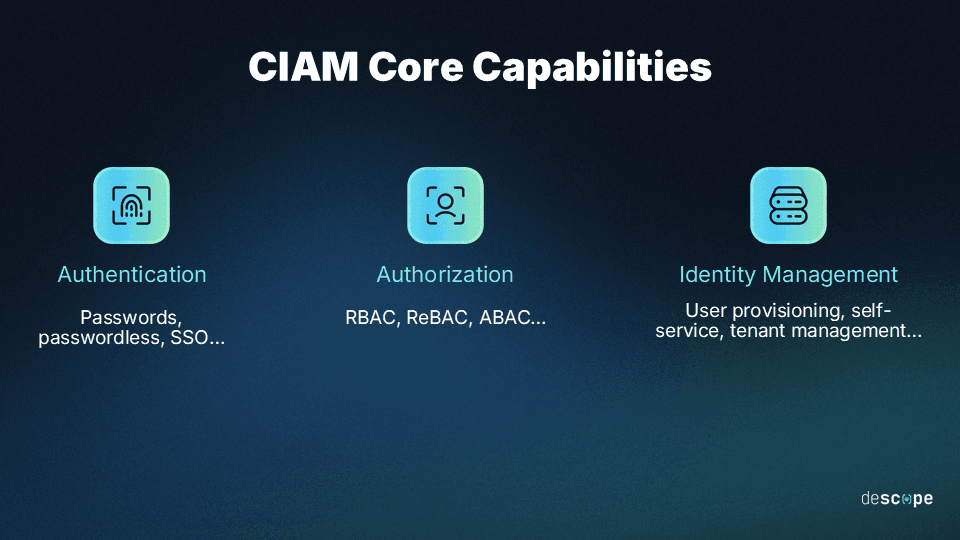
While the functions of CIAM solutions are varied and adaptable, they all work to facilitate three central capabilities:
Authentication: Validates users’ login attempts by checking their credentials against those stored in the CIAM solution’s database.
Authorization: Grants users the appropriate level of platform access based on the permissions assigned to their accounts.
Identity Management: Encompasses a variety of capabilities, such as user provisioning (e.g., SCIM), tenant management, token and session management, and delegated administration.
Business benefits of CIAM
As companies increasingly prioritize customer experience and security, CIAM solutions are becoming a key component of external authentication systems. In fact, the CIAM market is projected to grow by 15.3% by 2026. According to Gartner, organizations adopting passwordless CIAM will see a significant reduction in customer churn, with numbers dropping by more than 50%.
The growing adoption of CIAM can be attributed to the wide range of benefits it offers businesses, including:
Improved user adoption and conversion. CIAM tools enable personalized, frictionless experiences with features like progressive profiling, consent and preference management, self-service admin, and passwordless login. These capabilities help organizations engage customers more effectively, increasing both user acquisition and retention.
Enhanced protection against identity attacks. CIAM solutions offer advanced security features, including adaptive authentication, secure session management, bot protection, and biometric authentication. These measures work together to mitigate the risks of account takeover, credential stuffing, and other identity-based attacks, providing customers with a higher level of trust.
Increased engineering productivity and focus. By outsourcing identity management to a trusted CIAM provider, businesses can significantly reduce the workload for engineering teams. This shift allows developers to focus on more critical areas, as CIAM solutions handle session management, credential storage, password resets, and the implementation of MFA.
B2B enterprise readiness. CIAM platforms offer vital features like SAML and OIDC SSO, federated authentication, tenant management, and user provisioning. These capabilities allow B2B companies to scale and expand their offerings, enabling them to move upmarket and serve enterprise customers more effectively.
Common use cases of CIAM
CIAM solutions serve a wide range of industries and business needs. By centralizing and securing user authentication, CIAM allows organizations to offer seamless, personalized experiences while maintaining high levels of security. Below are some of the most common use cases for CIAM:
Ecommerce and retail
In retail, CIAM solutions play a critical role in streamlining the customer experience. By supporting multiple authentication methods, CIAM offers a fast, frictionless checkout process. This helps reduce cart abandonment rates and increases customer satisfaction. Last but not least, CIAM facilitates personalized recommendations based on user data, improving customer retention and driving repeat purchases.
Read more: Authentication in Ecommerce: Best Methods & CIAM Tips
Online banking and financial services
Security is paramount in the financial sector, and CIAM solutions help safeguard sensitive customer information while providing seamless access to banking services. Through MFA and identity verification processes, CIAM helps prevent fraud and account takeover while also enabling organizations to stay compliant with regulations that mandate strong MFA (e.g. the NYDFS Cybersecurity Regulation). Additionally, CIAM’s support for SSO and federated authentication makes it possible for customers to access different financial tools and accounts with minimal hassle.
Read more: Customer IAM in Banking: Considerations & Best Practices
Healthcare
In healthcare, CIAM helps secure patient data while enabling convenient access to medical records, appointment scheduling, and telehealth services. With strict compliance requirements like HIPAA in the U.S., CIAM solutions ensure that only authorized individuals can access sensitive information. Self-service options also empower patients to update their profiles and manage their preferences, reducing administrative burdens for healthcare providers.
Travel and hospitality
Travel platforms and hospitality businesses use CIAM to create personalized user experiences by leveraging data like travel preferences, booking history, and loyalty program details. CIAM supports seamless logins across different devices and applications, whether booking flights, managing reservations, or earning loyalty points. It also enables customer segmentation, allowing businesses to offer tailored promotions and services that increase engagement and conversion rates.
B2B platforms and SaaS
B2B platforms and SaaS businesses use CIAM to manage user access across multiple organizations. It helps implement secure, scalable access controls with features like RBAC and federated identity management. CIAM simplifies onboarding for enterprise clients by allowing customization of user roles, access permissions, and integrations with other enterprise systems.
Read more: A Primer on B2B Authentication With Descope
Government and public services
Government agencies and public service organizations use CIAM to provide citizens with secure, convenient access to government services, such as tax filing, social security, and health benefits. CIAM ensures that sensitive information is protected through robust identity verification processes, including passwordless authentication. The ability to offer SSO across multiple services also enhances user convenience, reducing friction and improving engagement with digital government platforms.
How to choose the right CIAM solution
Choosing the right CIAM solution for your app requires careful evaluation to ensure it meets both your current and future identity management needs. Here are the key criteria to help you evaluate potential CIAM providers.
Breadth and depth of auth method support
As your organization grows, your identity needs will evolve too. CIAM providers that support a wide range of authentication methods and implementation approaches are best placed to adapt to the changing identity landscape. Look for providers that offer:
Support for popular authentication methods like passkeys, magic links, OTPs, social login, authenticator apps, and passwords.
Compatibility with standard, interoperable protocols like SAML, OpenID Connect, WebAuthn, and FedCM.
Support for different authorization models (RBAC, ReBAC, ABAC).
Seamless integration with various apps (custom, off-the-shelf, etc.).
Low-code customizability
Customer authentication is rarely one-size-fits-all. A good CIAM solution will allow you to easily modify user journeys and authentication flows to meet your app's specific needs. Key features to look for include:
Customizable user journeys, preferably via an intuitive, low-code visual interface.
Flexible user models with custom attributes and granular access control.
The ability to A/B test and measure login flows and user journeys to optimize the experience.
Easy customization of user-facing screens and the ability to implement progressive profiling.
Extensible ecosystem
Customer identity impacts nearly every aspect of your business. A preferred CIAM solution will provide a robust and scalable system of integrations with third-party services to keep customer identity synchronized across all tools and departments. You should look for::
Integrations with existing tools in the fraud prevention, identity verification, CRM, and CDP space.
A flexible integration framework that supports adding more tools as your needs grow.
The ability to add custom and in-house integrations (e.g., HTTP, SMTP, audit logs).
Low-effort integration processes, allowing for easy setup, testing, and swapping tools when needed.
Reliability, security, and support
Problems with customer signup or login can directly lead to lost business. Security breaches involving customer data have dire consequences. To ensure reliability, security, and ongoing support, evaluate the following factors:
Historical availability, SLA performance, and response times.
Session and token management best practices (rotation, reuse detection).
The largest customer the CIAM solution serves, which can indicated scalability.
Implementation flexibility for developers with multiple abstraction layers (UI, SDK, API).
Key certifications like SOC 2 Type 2 and ISO 27001 to ensure industry-standard security practices.
Availability of active and passive support, as well as assistance with migration to new systems.
Customer reviews and ratings on trusted platforms like G2 Crowd to gauge overall satisfaction and performance.
Hassle-free CIAM solutions with Descope
CIAM solutions are a powerful way to manage identities, authenticate users and protect apps against data breaches. They offer a wide variety of features, from customer authentication to self-service onboarding, to provide a frictionless and secure user experience.
If you are evaluating CIAM solutions for your organization, Descope can help. Our drag & drop CIAM platform helps hundreds of organizations improve user onboarding, protect accounts against account takeover, and unify identities across customer-facing apps – all without writing code.
Sign up for a Free Forever Descope account to get started! If you have questions, book a demo with our auth experts.





