Table of Contents
What is IDaaS?
The threat actors who infiltrated AT&T’s cloud platform in 2023 didn’t need sophisticated tools—just stolen credentials. One purloined password cost the telecom a $370,000 ransom, spawned multiple class-action lawsuits, and sparked a congressional investigation.
AT&T isn’t alone, though; the Verizon 2024 DBIR revealed that 77% of web app breaches were driven by credential theft, reminding us that identity sits in the crosshairs of every would-be cybercriminal. Yet, managing identity infrastructure is rarely at the top of anyone’s “to do” list. Simply put, most organizations don’t want to spend precious resources on DIY identity when a third party can do it better.
Enter Identity as a Service (IDaaS), an identity and access management (IAM) model that has revolutionized how businesses protect sensitive data and operations. This guide explores what IDaaS is, why it matters for keeping your users secure, and how to select the right provider to shield your organization from today’s identity-targeting threats.
Main points
Cloud-based identity management eliminates the headaches of in-house security infrastructure while reducing costs and technical overhead.
Modern IDaaS platforms provide advanced authentication methods, fine-grained authorization options, and the flexibility to customize user journeys with minimal coding.
The right IDaaS provider delivers both enhanced security and improved user experience (UX), letting your team focus on your core business.
What is IDaaS?
IDaaS is a cloud-based subscription model that outsources a wide range of IAM processes to specialized third-party providers. Instead of building and maintaining complex systems in-house, organizations can utilize ready-made identity services that can include authentication, authorization, user provisioning, single sign-on (SSO), and much more.
Think of IDaaS like a security service that sends guards to watch over your property. Rather than hiring, training, and managing your own security team, you contract with specialists who handle it for you. You get the benefits of a safer environment, but without needing any expertise—and potentially at a much lower cost.
The main function of IDaaS is managing the identity lifecycle from end to end. That includes creating (or removing) user accounts, enforcing access policies, providing secure authentication using various methods, and maintaining clear visibility into all identity-related activities (a.k.a. audit trails). IDaaS takes the pressure off of companies that don’t specialize in identity security, allowing them to focus on their core business instead.
Here’s an example of IDaaS in action: when a new customer creates an account with your business, the IDaaS remembers their info and authenticates them. It keeps track of what login method they used, and it can even provide self- service tools for changing their security settings. Meanwhile, the devs at your company stay focused on refining and innovating your main offering rather than spending cycles on authentication.
Traditional identity management vs. IDaaS
When we say “traditional identity management,” we’re referring to the approach that came before IDaaS: built in-house, typically on-premises, and completely self-reliant. The concept of IAM isn’t at odds with IDaaS, though the two are often mistaken as opposites. IDaaS overlaps with all the capabilities of typical IAM (and more).
Traditional identity management and IDaaS represent two fundamentally different approaches to tackling the same problem: securing and managing user identities. Each philosophy differs significantly in implementation, resource requirements, and flexibility.
Traditional Identity Management | IDaaS | |
|---|---|---|
Deployment resources | Requires dedicated hardware (servers) and personnel (IT/developers), specialized expertise in identity security, and significant time for planning, testing, and implementation | Minimal internal resources needed; provider handles vast majority of implementation with pre-configured solutions |
Initial investment | High expenses for hardware, software license (if not using open source), and cost of dedicated staff | Low upfront cost; typically follows a subscription model with predictable monthly or yearly costs |
Ongoing maintenance | Internal team responsible for patching, upgrades, scaling and troubleshooting; requires continuous monitoring for performance degradation or failures | Provider handles infrastructure maintenance, automatic updates, and scaling; minimal internal overhead |
Security updates | Organization must stay current on security threats and implement patches; potential for gaps during update cycles, risk of zero-day vulnerabilities | Provider implements security updates rapidly across all customers; dedicated security teams monitor for new vulnerabilities and react quickly |
Adoption of new standards | Organization must research, plan, test, and deploy new identity standards; requires additional investment | Provider integrates new standards and authentication methods as part of the service; customers gain immediate access to the latest innovation |
Liability and compliance | Organization bears full responsibility for security gaps, breaches, and compliance failures | Shared responsibility model; provider typically assumes liability for infrastructure security, though customer retains ultimate responsibility for data |
Customization and flexibility | Maximum flexibility to tailor solution to exact organizational parameters; with enough resources and work, can be extremely robust | Typically offers configuration options within pre-built frameworks; flexibility varies between providers |
Scalability | Requires rigorous planning and potential hardware/software upgrades to accommodate growth | Easily scales with business through subscription adjustments; provider handles infrastructure scaling as part of service |
Integrations and connectors | Organization must develop and maintain integrations with new and legacy applications and services | Varies; some providers offer diverse and extensive connector ecosystems, while others are more restrictive with out-of-the-box integrations |
For many organizations, the decision between traditional identity management and IDaaS represents a trade-off between control and convenience. While homegrown solutions offer maximum customization potential, they demand significant internal knowledge and ongoing resource investment. IDaaS solutions sacrifice some degree of customization in exchange for faster and cheaper deployment, lower operational overhead, and the ability to leverage a dedicated security team’s expertise.
IDaaS vs. IAM
When discussing identity concepts, it’s important to know when terms refer to opposing ideas—and when they’re actually closely related. People often think IDaaS and IAM are competing alternatives, but they simply aren’t:
IDaaS is a delivery model.
IAM is a broader concept that can be accomplished through IDaaS.
IAM refers to the frameworks, policies, and technologies that manage digital identities throughout an organization. It’s closely associated with internal or workforce identity management, which means people generally think it applies more to employees. But that doesn’t mean IAM is always “just for the workforce.”
CIAM (Customer Identity and Access Management) is a form of IAM focused entirely on customers, whomever they might be. That could include other businesses (B2B CIAM), end users (B2C CIAM), partners (partner CIAM), or contractors. CIAM is still technically IAM, but it’s so specialized that IDaaS providers often offer one but not the other. Choosing between IAM and CIAM is another discussion entirely, and you learn more their differences in our blog, IAM vs. CIAM Explained.
IDaaS, in contrast, is specifically a delivery model for IAM (or CIAM) capabilities through subscription services. If IAM is what you need to accomplish, IDaaS is one way to get there. This relationship is similar to how Customer Relationship Management (CRM) as a concept is distinguished from CRM solutions. You wouldn’t say “CRM vs. Salesforce” because Salesforce is a way to implement CRM.
What does IDaaS typically offer?
Robust IDaaS usually provides a comprehensive foundation for managing every aspect of identity across your organization. While the specific features can vary between providers, leading IDaaS vendors aim to cover the entire end user lifecycle. Here are the core components that make up a solid IDaaS solution:
Visual workflow builders for custom user journeys
These are visual workflow editors that allow both engineers and non-developers to build and manage the entire auth journey without writing a single line of code.
Drag & drop interfaces like Descope Flows enable organizations to:
Design customized authentication flows for different user types or scenarios
Build branded, user-facing screens and experiences
A/B test different flows to optimize conversions or achieve a specific goal
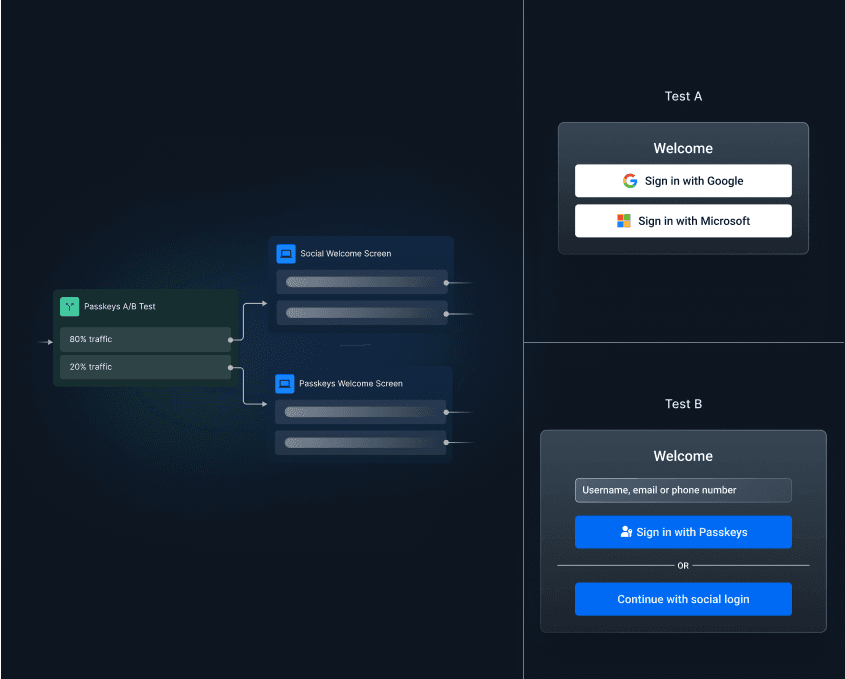
Modify authentication workflows without redeploying applications or touching code
Implement complex conditional logic for adaptive authentication based on risk factors
Comprehensive, modern authentication methods
Modern IDaaS supports a wide range of authentication options to balance security and UX (user experience):
Passwordless authentication: Options like magic and enchanted links, passkeys (biometrics), and one-time passwords (OTPs).
Traditional credentials: Passwords can be reinforced with stronger policies without adding complexity, such as by integrating a blacklist via Have I Been Pwned.
Social login: Options like “Log in with Google” or dozens of other identity providers prevent password fatigue while quickly onboarding new users.
Multi-factor authentication (MFA): An added security layer that adds another “factor” (like an OTP) to logging in, often used in conjunction with passwords.
Adaptive authentication: An upgraded form of MFA that only kicks in when a login looks risky, like if the location or device is new.
SSO: An authentication method that allows a user to log in to several different services using only one set of credentials.
Access control and policy enforcement
Beyond authentication, IDaaS solutions provide sophisticated authorization and access management controls:
Fine-grained access control (FGA), which covers a wide range of authorization modalities
Role-based access control (RBAC), a form of FGA based on a user’s assigned role
Relationship-based access control (ReBAC), another FGA variation that provides options for complex organizational structures

Attribute-based access control (ABAC), an FGA implementation that offers more dynamic, context-aware authorization
Unified policy definition, management, and enforcement across different environments and applications
Multi-tenancy management
Modern IDaaS platforms provide extensive multi-tenancy options for B2B applications and enterprise clients:
Tenant-specific configurations and branding
Tenant provisioning and lifecycle management
Self-service configuration options, such as self-service SSO
Hierarchical tenant structures for more complex organizational structures
Tenant isolation to satisfy regulatory requirements and create clear boundaries
User lifecycle management
IDaaS solutions streamline the entire user lifecycle, from onboarding to offboarding:
Automated user provisioning across multiple systems and applications
Self-service registration and account creation
User profile management, including security preferences
Account deactivation and deletion
Automated offboarding workflows to remove access when users delete or abandon accounts
Integration with other systems for customer (CRM) or employee (HR tools) lifecycle management
Analytics, visualization, and reporting
Insights into the authentication experience can help companies optimize their flows for better conversion, improve login success rates, and even reduce attrition. From a technical perspective, it can highlight potential hiccups in the auth process, enabling teams to make better decisions about where to focus their efforts.
Real-time monitoring of authentication attempts and failures across different methods
User activity tracking and session management
Anonymous user tracking before account creation

Usage analytics and adoption rates
Dashboards for reporting and sharing authentication metrics
Integration capabilities and ecosystem
IDaaS solutions typically offer a range of out-of-the-box integrations, though the scope and size of these libraries vary significantly. Subsequently, many IDaaS vendors include extensive SKDs, APIs, and relevant documentation to help their customers extend access to any system they wish. Third-party connectors provide an easy way to link new or existing systems with an IDaaS provider:
Prebuilt connectors for popular business applications
API access for custom integration development
Webhook support for event-driven architecture
SDK availability for multiple programming languages

The pros to using IDaaS
Earlier, we talked about the differences between traditional identity management and IDaaS. We’ve established that IDaaS sacrifices some flexibility in favor of greater affordability and simplicity. Now, let’s examine how IDaaS delivers tangible benefits in specific contexts and through real-world results:
Rapid time-to-market for digital products and services
IDaaS dramatically reduces the development time for identity-related functions, allowing organizations to launch new products and services faster. By eliminating the need to build authentication systems from scratch, product teams can focus on core business operations instead of security infrastructure.
Enhanced customer acquisition and retention
Modern consumers crave a “white-glove” experience, but few companies are equipped to cater to their ever-evolving tastes. Modern IDaaS can improve conversion rates with the latest auth methods and flow configurations, eliminating unnecessary friction that leads to drop-offs. Better auth is simply good for business.
Stronger regulatory compliance posture
IDaaS providers typically maintain up-to-date compliance with regulations like GDPR, CCPA, and industry standards such as SOC2 and PCI DSS 4.0. This allows companies to enter regulated markets more easily while reducing compliance overhead (and the risk of being fined).
Predictable identity expenses at scale
Cloud-based IDaaS converts unpredictable costs into expenditures you can count on. While a DIY approach may offer greater flexibility, it also comes with the risk of unexpected forces that can tug at your purse strings. IDaaS solutions let you grow without the unknown variable of identity costs looming.
Organizational focus on core competencies
By outsourcing identity management, your developers can focus their specialized talents on the reason they joined your organization: innovating and refining the core product or service. Spending cycles on troubleshooting auth draws focus away from differentiation. IDaaS does identity, and it lets you do you.
Simplified, unified access for diverse user groups
IDaaS solutions excel at handling diverse user populations, from customers and partners to businesses with various roles. Cohesive access control, combining authorization processes in one central management platform, solves one of the biggest challenges homegrown auth creates.
Key things to look for in an IDaaS solution
When evaluating IDaaS providers, consider these key criteria based on your organization’s priorities:

Evaluation Criteria | Priority | What to Look For | Why It Matters |
|---|---|---|---|
Security capabilities | Critical | • Multiple modern authentication methods
• Adaptive MFA
• Uses latest security standards
• Audit logging
• Bot detection | The very foundation of any identity solution. Inadequate security undermines the entire purpose of IDaaS, exposing your organization to account takeover and data breaches. |
Integration ecosystem | Critical | • Support for standard protocols (OIDC, SAML)
• Diverse connectors for your existing systems
• API and SDK availability
• Webhook support
• Migration tools | Even highly secure solutions fail if they can’t integrate with your tech stack. Integration capabilities determine whether the solution is a good fit for your specific scenario without costly development. |
Customization & UX depth | High | • Visual workflow editors
• Custom styling and branding
• Progressive profiling, anonymous user tracking
• Adaptive auth journeys based on context | Auth experiences directly impact conversions and retention. The ability to customize flows without sacrificing security is a game-changer for organizations that want both strong protection and universal accessibility. |
Developer & admin experience | High | • Intuitive management tools
• Detailed analytics and reporting
• Low/no-code environment
• Zero coding needed to make changes once deployed | Day-to-day admin shouldn’t be a hassle. The less time devs spend micromanaging your IDaaS solution, the more time they have to refine the core product. |
Scalability & performance | Medium-high | • Data regionality & global distribution options
• Guaranteed uptime via SLAs (99.9% or 99.99%)
• Proven performance metrics and speed | A large user base calls for a modern approach to identity, That means minimal downtime or degradation. Performance issues impact user experience and should be dealt with quickly. |
Support & community | Medium | • Response time commitments
• Multiple support channels
• Documentation quality
• Active dev community
• Excellent error handling | Even leading tech needs strong support. How helpful a provider’s support ecosystem can determine whether your implementation will be a quick success—or a grueling slog. |
Futureproofing | Medium | • Innovation track record
• Partnership network
• Roadmap transparency
• Adoption of new standards | Identity is built on shifting sands, which is why a solid IDaaS provider will be at the forefront of innovation. Your solution should demonstrate the ability to evolve with the times. |
Cost structure | Variable | • Transparent pricing
• Predictable scaling costs
• No hidden costs (support, professional services)
• ROI compared to competitors | Cost shouldn’t be the primary factors for security solutions, but understanding the TCO (total cost of ownership) is essential for budgeting and comparing alternatives. |
Descope: No-hassle IDaaS for your business
IAM does not have to be complicated (or expensive). IDaaS is a great solution for businesses of all sizes to manage user identity and access for their customers, employees, and other external users, all while reducing operational complexities and costs.
Descope is a comprehensive IDaaS that offers intuitive workflows, comprehensive support, and a wide array of features designed to meet the IAM challenges of today and tomorrow. Over 400 organizations use Descope to improve user onboarding and conversion, enhance protection with adaptive MFA, and get a 360-degree view of their customer journey across apps.
Sign up for a Free Forever account with Descope to subscribe to our CIAM platform. Have questions about our platform? Book time with our auth experts.







