Table of Contents
Understanding session management
Session management is a cornerstone of creating secure, interactive, and personalized user experiences within web applications. As users navigate through web pages, making purchases, reading content, or engaging in various activities, their interactions need to be seamlessly connected and maintained. This is challenging given the stateless nature of HTTP – the foundational protocol of the web.
Session management bridges this gap, enabling applications to remember users' actions and preferences from one page to the next, ensuring that their journey on a website feels cohesive and tailored to their needs.
Below, we’ll walk through what session management is, exploring its importance, techniques, and best practices. Learn how to use session management to secure web applications against common threats, all the while enhancing the user experience.
Understanding session management
A session is a finite period of time during which authenticated users are engaging with a system or application. A session starts when the user enters the app / website and lasts until the user logs out or is timed out.
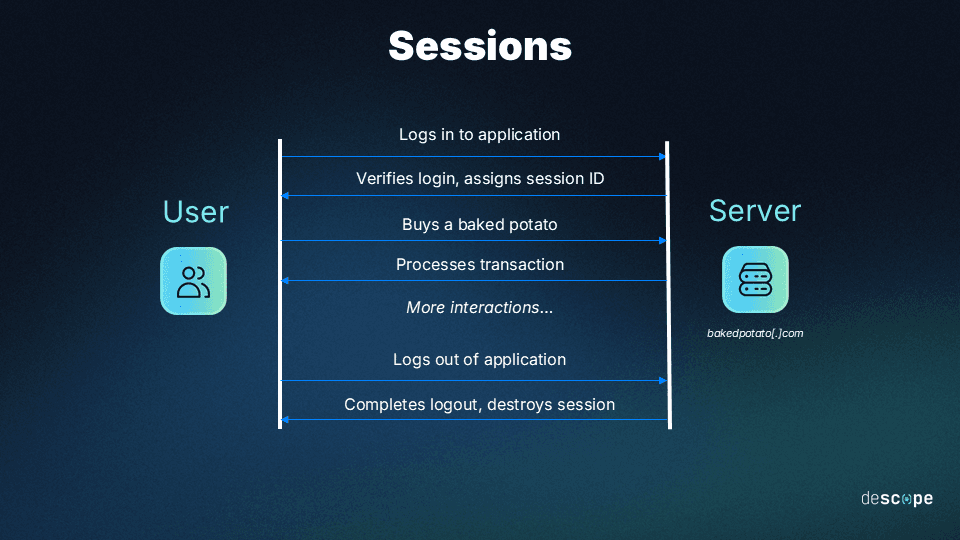
Session management refers to the process of securely handling multiple requests from the same user or client during a single session. It involves creating, maintaining, and terminating sessions, ensuring the security of the data exchanged in these sessions, and efficiently managing session data. Here are the aspects involved:
Creation: Once a user is authenticated, a session is started by generating a unique session identifier (session ID). This session ID is then sent to the client, typically as a cookie or a token, and is used to track subsequent requests from the user.
Session Storage: The server stores the session data, which can include the session ID and any other relevant information about the user's interaction with the web application (ex. user preferences, authentication status, shopping cart items).
Maintenance: With each HTTP request from the user, the session ID is sent to the server. The session ID is used to retrieve the corresponding session data, thereby maintaining the interaction between the user and the application. If any suspicious or anomalous activity is detected, re-authentication may be required.
Termination: Sessions end when users log out or meet other criteria, such as closing their browser or application windows. Sessions may be configured to time out after a certain duration, at which point users are logged out or prompted to re-authenticate.
Effective session management is vital for maintaining the security, performance, and scalability of web applications. It ensures that user data is kept secure during interactions with the application, facilitates a seamless user experience by remembering state information, and mitigates various security risks associated with handling session data.
Session management vulnerabilities
The stakes of session management couldn’t be higher, as specific attacks such as session hijacking and session fixation can lead to cybersecurity breaches.
Session hijacking is a type of man-in-the-middle (MITM) attack in which cybercriminals pose as authenticated users to gain illegitimate access to resources for theft, fraud, extortion, and other illicit ends.
Session fixation is a subset of hijacking in which attackers set session IDs to values they know and can replicate to gain access alongside the user or maintain access after the actual, legitimate access ends.
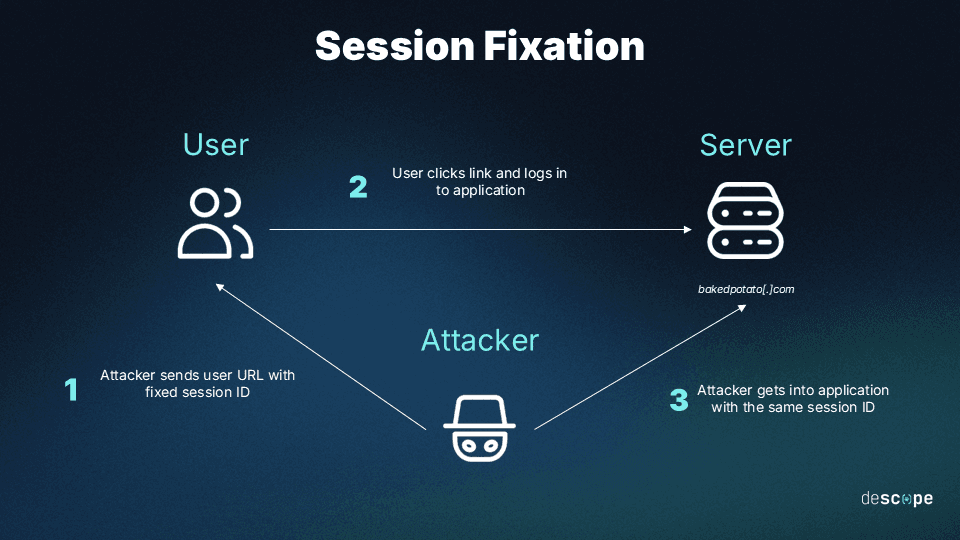
In short, attacks like these lead to account takeover and broken authentication.
Some of the biggest auxiliary threats to watch out for are social engineering, outright credential theft, and weak credentials enabling attackers to guess or crack them. Any of these could lead to cybercriminals engaging in session hijacking or fixation (or a hybrid attack involving both).
Best practices for secure session management
Use secure, random session identifiers: The session ID, which uniquely identifies user sessions, should be generated using a secure, cryptographically strong random number generator.
The Open Worldwide Application Security Project (OWASP) session management cheat sheet highlights the importance of session naming conventions. An overly simple name makes for easy fingerprinting, which can be leveraged for hijacks and other attacks. Likewise, session IDs should be assigned long enough numerical values to prevent brute force attacks leveraging compute to guess (usually shorter) codes. OWASP recommends at least 128 bits.
Implement HTTPS for all sessions: All communication involving session IDs and data should occur over HTTPS, which encrypts the data in transit. This prevents attackers from eavesdropping on the communication and stealing session IDs through MITM attacks. Here are some other tips:
Set reasonable session expiration times based on your application’s requirements.
Implement mechanisms to validate session data regularly, such as automatically checking for expired or invalid session IDs and terminating any red-flag sessions.
Enforce session expiration: Sessions should have a defined timeout period, after which they are automatically terminated. This minimizes the risk of session hijacking by limiting the time an attacker has to exploit an active session. Sessions should also be terminated immediately upon user logout or prolonged inactivity.
On another level, adopters need to make sure that their session management practices satisfy regulatory requirements applicable to them. For example, the Payment Card Industry (PCI) Data Security Standards (DSS) v4.0, which applies to merchants that process credit card payments, mandates auto-termination if a session is inactive for 15 minutes (per Requirement 8.2.8).
Regenerate session IDs after login: Regenerate and issue a new session ID upon every successful user authentication. This practice prevents session fixation attacks, where an attacker could pre-establish a session and trick a victim into authenticating under that session ID.
Session management techniques
There are several ways to do successful session management. Each of these techniques has its own advantages and trade-offs regarding security, scalability, user experience, and the specific requirements of the web application. Often, a combination of these techniques is used to achieve a balance between functionality and security in session management.
Let’s review some of the most common practices:
Cookie-based sessions
Cookies are a common approach to session management across web applications. They are small pieces of data generated by a server that are on the user’s device, typically on the web browser. Cookies track a user’s behavior and can be used to signal to a centralized system that something is off, or they can be configured to force a session to terminate or trigger re-authentication automatically.
Cookies are inherently scalable and easy to implement, as they are already a standard feature across the internet. However, they are limited to web-based use cases and have their own shortcomings. For example, cookie-based systems are more susceptible to cross-site scripting (XSS) attacks and session hijacking than other session management approaches. Plus, they carry some privacy risks and the risk of a downgraded UX if not implemented properly.
Token-based sessions
Another commonly used method are tokens – small, textual pieces of data. This method leverages ID tokens, access tokens, and refresh tokens to initiate and control user access across multiple devices and systems. The client includes this token (typically in JWT format) in the authorization header of HTTP requests to authenticate and manage sessions. Token-based session management is particularly popular in RESTful APIs and Single Page Applications (SPAs), as it supports stateless authentication.
A major benefit of this approach is that time limits and other security features can be built directly into the tokens themselves. And, since the tokens are relatively lightweight, they are scalable alongside any tech stack. They also provide security across a wide variety of hardware, software, and network environments, with few limitations in terms of compatibility.
Token-based authentication is one of the best ways to ensure secure session management.
Other techniques
Other approaches to session management offer similar end results if less flexibility and overall security assurance. One legacy example is URL rewriting, which functions similarly to cookies by appending information about the user’s access session to the URL they’re using to view a given website at a given time and under other particular conditions. Given its simplicity, this is easy to implement. However, it can be bypassed if an attacker hijacks or replicates the session.
Another relatively well-trodden method is using hidden form fields to track and manage user access sessions. These HTML inputs embedded in web pages track information about a user’s behavior and cross-reference it against intelligence or benchmarks to trigger termination or re-authentication, if necessary. The same caveats for cookie-based sessions and URL rewriting apply here.
Other session management considerations
When developing authentication and authorization flows and choosing between comparable options, session management capabilities and flexibility should be a top priority for developers.
Beyond the best practices and approaches detailed above, other considerations include:
Security: To prevent breaches, be sure to choose tools and controls that restrict access to sensitive information and systems that contain or are connected to it.
Scalability: Consider how organizational growth impacts session maintenance, including increased personnel and a bigger, more diverse, and sensitive tech stack.
Performance: Select methods that provide adequate protection and monitoring capabilities with minimum overhead and response times.
Simplicity: Prioritize simplicity to facilitate the initial implementation and ongoing management; an easier system to use will be cheaper long-term.
Privacy: Keep user privacy concerns top of mind, as access sessions need to protect both sensitive data and the users who could access it or be impacted by a data breach.
Efficient session management with Descope
Achieving a delicate balance between security and usability is no small feat and requires a comprehensive understanding of the underlying mechanisms and potential vulnerabilities.
For developers and companies looking to streamline the integration of advanced session management into their applications, Descope offers a simple solution. With a drag-and-drop interface and a host of SDKs, Descope simplifies the complexity of implementing secure and efficient session management within your authentication and authorization flows.
Sign up for a Free Forever account with Descope to streamline and secure your session management. Have questions about our platform? Book time with our auth experts.





