Table of Contents
What is two-factor authentication?
Two-factor authentication (2FA) is a popular authentication system that improves on traditional password-based logins by requiring a second authentication factor. This additional factor increases account security without burdening the end user—a significant reason millions use 2FA worldwide.
Presently, two-factor authentication configurations are so deeply ingrained in people’s professional and personal lives that changes to it can cause major security concerns. For example, when X (formerly Twitter) discontinued the use of SMS-based 2FA for non-paying users in early 2023, experts predicted their cyberattack volume would increase.
With its importance in mind, let’s break down what 2FA is, how it works, and what to consider when implementing such systems in your next app or software project.
What is two-factor authentication?
So what is 2FA? Authentication flows that only require only one set of credentials, especially knowledge-based factors like passwords, are highly susceptible to cyberattacks. Deploying 2FA counteracts this security risk by creating a login process that requires two credentials, or authentication factors, for access.
There are differences in when and how the secondary credentials are requested. For example, the specific credentials needed may vary based on account sensitivity, as in the case of “step-up” authentication. But, in all cases, two-factor authentication adds an extra layer of security to the login process, asking users to provide a second authentication factor after they’ve provided the first one.

This is why one of the more common alternate names for 2FA configurations is “two-step verification” (2SV). Regardless, whatever name an organization gives to such a deployment, it’s 2FA if two credentials are required for login.
2FA vs MFA: What’s the difference?
Another term closely related to 2FA is multi-factor authentication (MFA). While these names are often used interchangeably, some distinctions exist between them. The primary difference is that two-factor authentication specifically refers to a system where two factors are used – not three, four, or any other number.
MFA, by contrast, encompasses any auth method in which more than one is used.
For example, an MFA deployment might require users to provide their username and password, verify their identity through a secondary device, and then answer a security question. But in a 2FA deployment, only two of those three exchanges would be necessary.
Despite this distinction, there are also many ways in which 2FA and MFA can be considered the same. Technically speaking, 2FA is a subset of MFA. Many MFA deployments utilize two factors, making them 2FA in practice (just not in name).
How 2FA works in practice
While different methods and styles are used for two-factor authentication, almost all operate similarly. Before any attempted login, users must establish a set of secure credentials. This typically starts with a username and password, although passwordless methods such as magic links, social logins, and OTPs are gaining adoption every day. From there, users choose a secondary factor, such as a device they own, their biometrics, or a security question—more on this below.
Once the credentials are in place, users attempt a login with their primary authentication factor. Once accepted, they are prompted to verify their identity through their chosen secondary factor. A message may be sent to a secondary device or account, or they may be prompted to provide a biometric scan. Once the secondary factor is accepted, access is granted.
One caveat in how this system works is when and how secondary factors are required. In a step-up system, a secondary factor might not be requested at login but when the user attempts specific account actions, like accessing sensitive files.
Types of factors used in 2FA
Another common variation between 2FA systems is in the specific kinds of factors used. Most 2FA and MFA systems utilize authentication factors that fall into one of three distinct categories:
Knowledge-based: These factors are secrets known only to the user, such as unique passwords or passcodes. Other common examples are user-selected security questions.
Possession-based: These are checks against secondary devices or accounts the user owns. The best-known examples are codes sent via SMS text message, email, or messaging services such as WhatsApp.
Inherence-based: These are factors that are specific to the user’s biological traits. Often, they involve biometric scans utilizing a device’s capabilities for face scans or fingertip imaging.
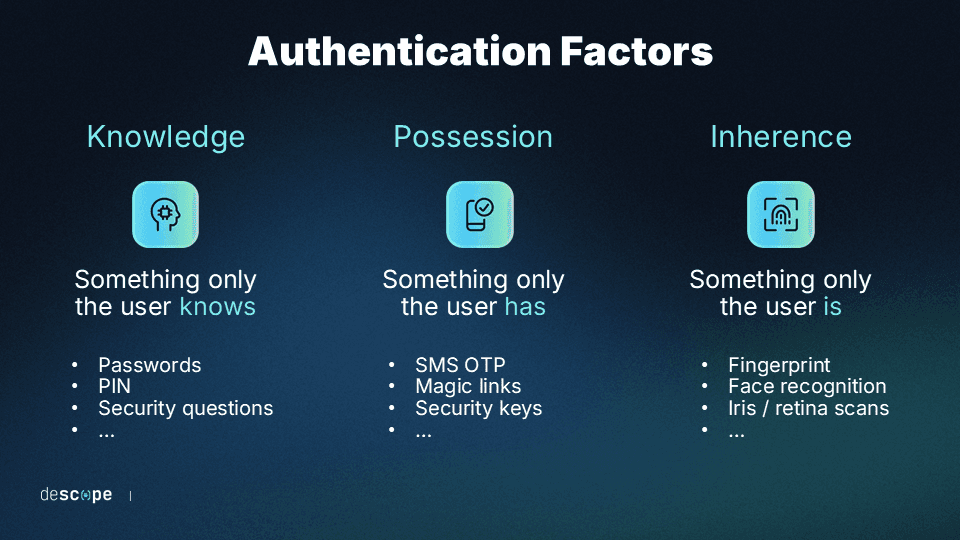
In some 2FA configurations, two of the same kinds of factors are used. For example, a password and a security question are two knowledge-based factors. However, most experts recommend using two different kinds of factors—for example, magic links and biometrics —for 2FA.
Common 2FA methods
Aside from the specific credentials required, two-factor authentication systems differ in how they are requested and provided. Some of the most commonly used methods for 2FA include:
One-time passwords (OTP) sent via SMS or other means to the individual
Time-based one-time passwords (TOTP) synced via an authenticator app
Push notifications via a secondary app or platform on a user’s device
Retinal and face scans, administered through a device’s front-facing camera
Fingerprint scans utilizing built-in technology on the user’s device
Security keys, including interface with a physical reader or hardware token
In some systems, end users must use a specific method. For example, enterprise 2FA deployments often require employees to verify themselves using a particular app platform. In other cases, users can choose the platform that works best for them.
The specific needs and means of a user base are the most important considerations when designing or implementing a 2FA solution. The methods need to be accessible for your app’s intended users to be effective.
Benefits and drawbacks of 2FA
The most significant benefit of two-factor authentication (and the reason behind its popularity) is its positive impact on account security. Google has long been a proponent of 2FA for this reason, having found in a 2019 study that 2FA alone can prevent up to 100% of automated bot attacks.
This was among the reasons Google decided to auto-enroll over 150 million active users into a 2FA deployment for their accounts in 2021, leading to a 50% decrease in attacks on 2FA-protected accounts.
And, unlike other auth methods that require a more significant burden on end-users, 2FA is relatively easy for all parties involved. Moreover, all this security comes at a low user-level investment.
That said, two-factor authentication is not necessarily a perfect system. It’s less secure than more robust MFA deployments, like phishing-resistant MFA. It can entail relatively high resource costs on the enterprise side for managing SMS or other messaging bandwidth, as well as customer service for account lockouts. But similar and often greater tolls exist in many other auth alternatives.
How to implement 2FA
Just as there are many varieties of 2FA, there are many ways to implement a 2FA configuration in an app, website, or other digital environment. The specifics of the user base, the sensitivity of data being accessed, and the environment all make for different processes.
However, irrespective of these differentiating factors, deploying a two-factor authentication system always requires:
Selecting an appropriate method that meets both security and accessibility needs
Preparing and onboarding users with training on how to set up and use 2FA securely
Securing 2FA infrastructure, such as storage and processing bandwidth for the system
Designing the user interface to encourage adoption without compromising security
Drag-and-drop 2FA with Descope
2FA is the frontline defense against unauthorized access, and it's a security measure that's deeply woven into the fabric of our digital lives. However, it can be cumbersome to build 2FA systems in-house, maintain them in case of issues or vulnerabilities, and modify them with time as the organization’s auth needs change.
Descope can help. Our no-code CIAM platform helps organizations easily add 2FA flows to their app using a visual workflow editor. Admins can choose from any authentication method – including passwordless options like passkeys – for their 2FA implementation.
To further improve UX and security, Descope connects with fraud detection services such as reCAPTCHA and Traceable, enabling organizations to create branching user journeys based on the risk level of the login attempt. This stops advanced account takeover attempts while letting real users through without enforcing 2FA every time.
Sign up for a Free Forever account on Descope and start your 2FA journey today. Have questions about our product? Schedule time with our auth experts.






