Table of Contents
What is adaptive authentication?
Identity leaders and practitioners are continually seeking ways to enhance online security. New authentication methods such as passwordless authentication and multi-factor authentication (2FA / MFA) have gained adoption over the years and helped mitigate the risks posed by password-based authentication.
However, organizations are still searching for a better balance between security and user experience. For example, as early as 2017, the vast majority of basic 2FA adopters were receiving complaints from users.
Enter adaptive authentication, which was already seen as a better alternative to standard MFA a few years ago and has only grown in popularity since then. Adaptive authentication enables strong security tailored to a user's account details, while offering more flexibility for logging in according to their preferences.
What is adaptive authentication?
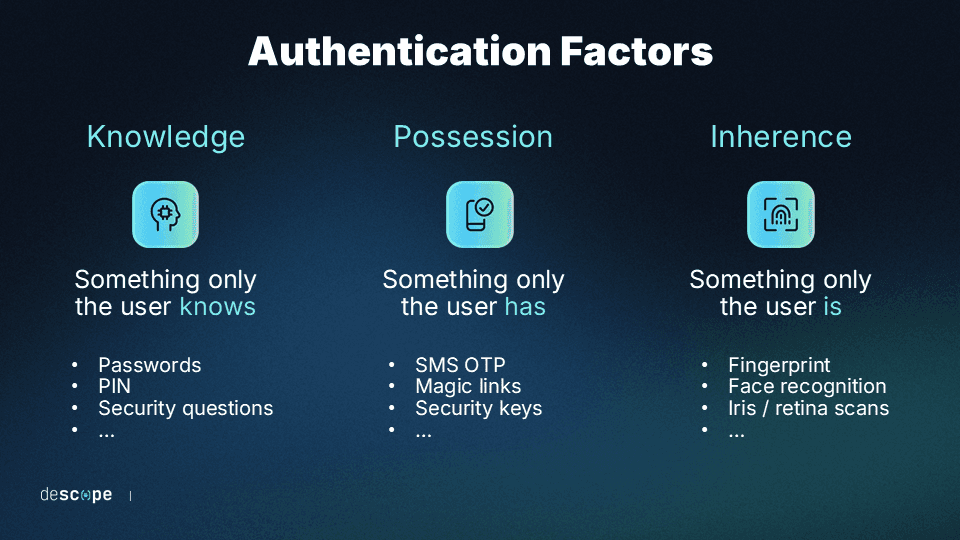
Adaptive authentication, also known as “risk-based authentication” or “risk-based MFA,” is a dynamic form of MFA. Traditional MFA approaches require at least two authenticating factors by default at login. This usually includes at least:
One knowledge factor (like a password)
One possession factor (like a secondary code or device)
One inherence or biometric factor (like a fingerprint or iris scan)
This is a static requirement in traditional MFA, meaning the same set is always required. But in adaptive authentication, the number and type of factors needed depends on the risk present during the login.
Some elements that determine whether and which additional credentials are needed are the hardware and software used. For example, users who log in from a new device or an unknown network may be asked for additional credentials.
Other factors involve the login attempt's context, like the time or the user’s location.
Adaptive auth is closely related to step-up authentication, where additional authentication measures are taken after login, depending on the user’s actions. The most significant difference is that adaptive auth front-loads the security assurance, factoring risks from the login attempt rather than post-login actions.
How does adaptive authentication work?
Adaptive auth works much like any other MFA system, with an added step to qualify which credentials are needed or if additional credentials are needed at all.
From the user experience side, logging in through adaptive authentication looks like this:
Users attempt to log in to their accounts in an app or website as they would normally
If the login attempt is deemed risky, they’ll be prompted for additional credentials
Upon entering the additional credentials, they’ll have access to their account
Other step-up authentication may be triggered, depending on their actions
Depending on the website, app, or program interface, the user may be prompted that a risk analysis is occurring. If conditions are normal, login could be seamless.
On the development side, processes that go into an adaptive auth workflow include:
Collecting user behavioral data and contextual information to form a baseline
Assessing risk levels based on user behavior baselines and anomalous conditions
Customizing specific authentication requirements based on the risk assessment
Automating the real-time decision of which factors are required to streamline login
It should be noted that every implementation of adaptive auth will work slightly differently. For example, apps with disparate access restrictions for different users might utilize other criteria depending on each account’s privileges. Those with access to the most sensitive data might require a biometric alongside a password and secondary account. In contrast, those with less sensitivity might require two knowledge factors, like a password and a security question.
Examples of adaptive auth in the wild
Here are some potential uses of adaptive auth in real-world scenarios:
Example 1: ECommerce protection
If you’re shopping online and log in to your preferred shopping app, adaptive authentication can notice you're on your usual device and network. Hence, it only asks for your password. If you add a pricey item to your cart, it senses the change and prompts for a fingerprint scan or phone code. Once verified, your purchase is secured, thanks to adaptive auth's watchful eye.
Note: The above is also an example of step-up authentication.
Example 2: Corporate network access
Logging in to your work network is usually password-only from your regular computer. But when you're on a new device in a different place, adaptive authentication steps in. It sends a mobile notification for your approval, ensuring safe access to company data even on the go.
Example 3: Social media security
Logging in to social media is usually a password-only affair on your device. But adaptive authentication steps in when you use a public computer in a new place. It sends an email code for extra verification, adding a layer of security to your account. Adaptive authentication keeps your online presence safe, no matter where you log in from.
Benefits and drawbacks of adaptive authentication
Adaptive authentication has notable benefits and some drawbacks to consider.
Benefits of adaptive authentication
Strong MFA when necessary: Similar to how MFA adds security layers over passwords, adaptive authentication further reinforces MFA by incorporating risk-based elements. While MFA is more secure than most traditional password-based solutions, it's still susceptible to attacks, such as SIM swapping, channel hijacking, and MFA bypass.
Improved user experience: Adaptive authentication addresses user experience concerns. It allows easy access for users under normal, lower-risk conditions with just one set of credentials.
Alignment with zero trust: Adaptive authentication aligns well with zero-trust architecture (ZTA) principles.
Drawbacks of adaptive authentication
New technology challenges: Being relatively new, adaptive authentication might not always work as intended when integrated into older technology systems.
Complexity: Adaptive authentication is more complex than static methods. It could require more resources for implementation and management, from employee understanding to account management.
While adaptive authentication offers various benefits, you must manage its challenges effectively for the best results. The best way to ensure the benefits outweigh the drawbacks is by streamlining your adaptive authentication flows with a platform like Descope.
No-code adaptive authentication with Descope
Adaptive authentication aims to blend safety and ease of use. Adjusting to real-time risks keeps your online world protected and hassle-free. However, building adaptive authentication in-house or stitching together various risk identification systems can be complex.
Descope helps organizations easily add adaptive authentication to their user journey flows with a no-code editor. Conditional steps can be added to auth flows that check the user’s risk levels and enable MFA only when the risk scores are high.

Apart from natively supporting user risk scores, Descope also integrates with third-party risk identification tools such as Google reCAPTCHA Enterprise and Traceable to enforce adaptive authentication based on external risk scores.
Sign up for a Free Forever account with Descope to “descope” authentication from your daily work. Interested to learn more about how we do adaptive authentication with third-party connectors? Book time with our auth experts.






