Table of Contents
About Traceable
APIs are making up an increasing portion of traffic on the Internet year over year. More than 50% of all HTTP requests handled by Cloudflare are attributed to APIs. APIs play an integral role in providing dynamic, personalized user experiences and serve as the plumbing to carry data across disparate systems. It’s not surprising therefore that cybercriminals now look to exploit API vulnerabilities and perform fraudulent activities at every opportunity.
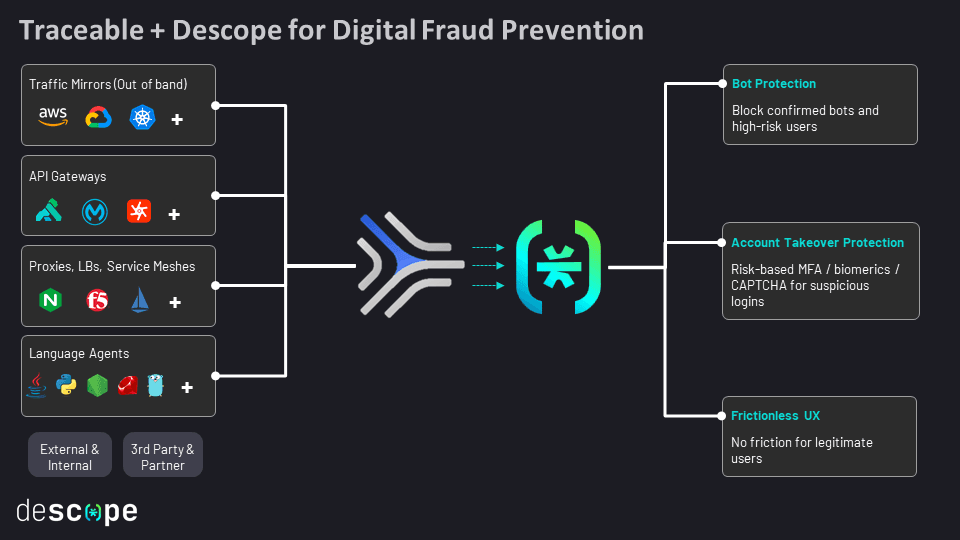
Descope’s connector with Traceable enables developers to add deep, contextual user behavioral data to their authentication and user journey flows. Organizations using the connector can detect and prevent digital fraud, institute MFA flows for suspicious login sessions, and confidently mitigate bot threats.
About Traceable
Traceable is a leading API security company that helps cloud-first, API-driven companies minimize business risk and maximize the value that APIs can provide to their customers. Traceable’s Digital Fraud Prevention protects businesses against fraudulent activities across APIs and digital interfaces.
The platform is powered by capabilities such as:
Advanced graph machine learning technologies that extract hidden correlations across different dimensions to provide a holistic view of “fraud rings”.
API-based user behavior profiling that creates a unique “fingerprint” identifier encompassing each user’s individual habits and patterns.
Proactive anomaly detection that enables organizations to mitigate threats before they cause damage.
Connector overview
The Descope connector with Traceable enables developers to:
Ingest granular user risk scores from Traceable into Descope authentication and user journey flows.
Create branching user journey paths in Descope authentication flows based on the severity of the risk scores provided by Traceable.
Implement response actions such as blocking high-risk logins, enabling biometrics, multi-factor authentication, or presenting a CAPTCHA.
Orchestrate user journeys in a no-code workflow combining Traceable data alongside data from other risk protection tools such as Google reCAPTCHA Enterprise and Amazon Rekognition.
Use case: Blocking high-risk logins
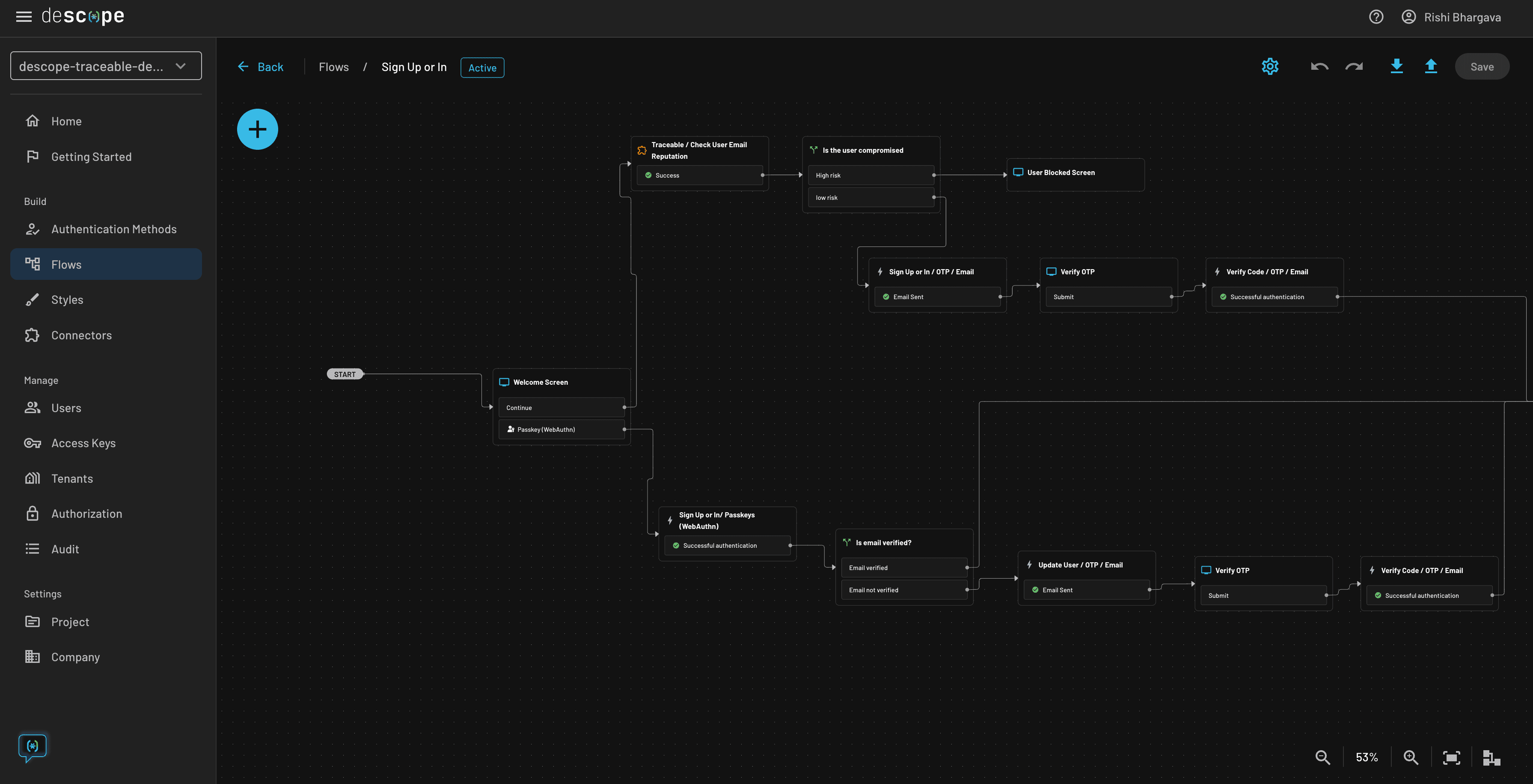
Attackers bombarding login and signup pages with spam, bots, and DDoS attacks can significantly impact user experience as well as business results. With Descope Flows, developers can use risk scores provided by Traceable to block high-risk logins and show them a separate message that their account may be compromised.
The Flow below highlights this process:
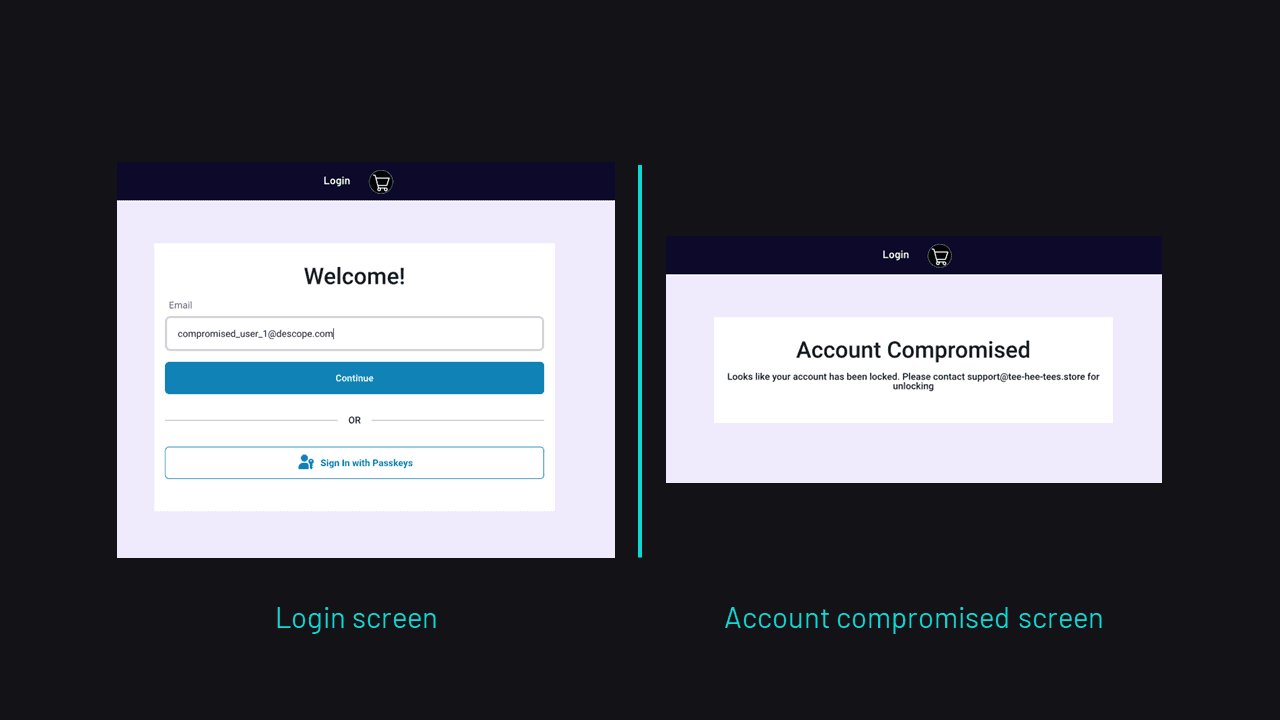
The screens below show the message a high-risk user receives:
Use case: Risk-based MFA
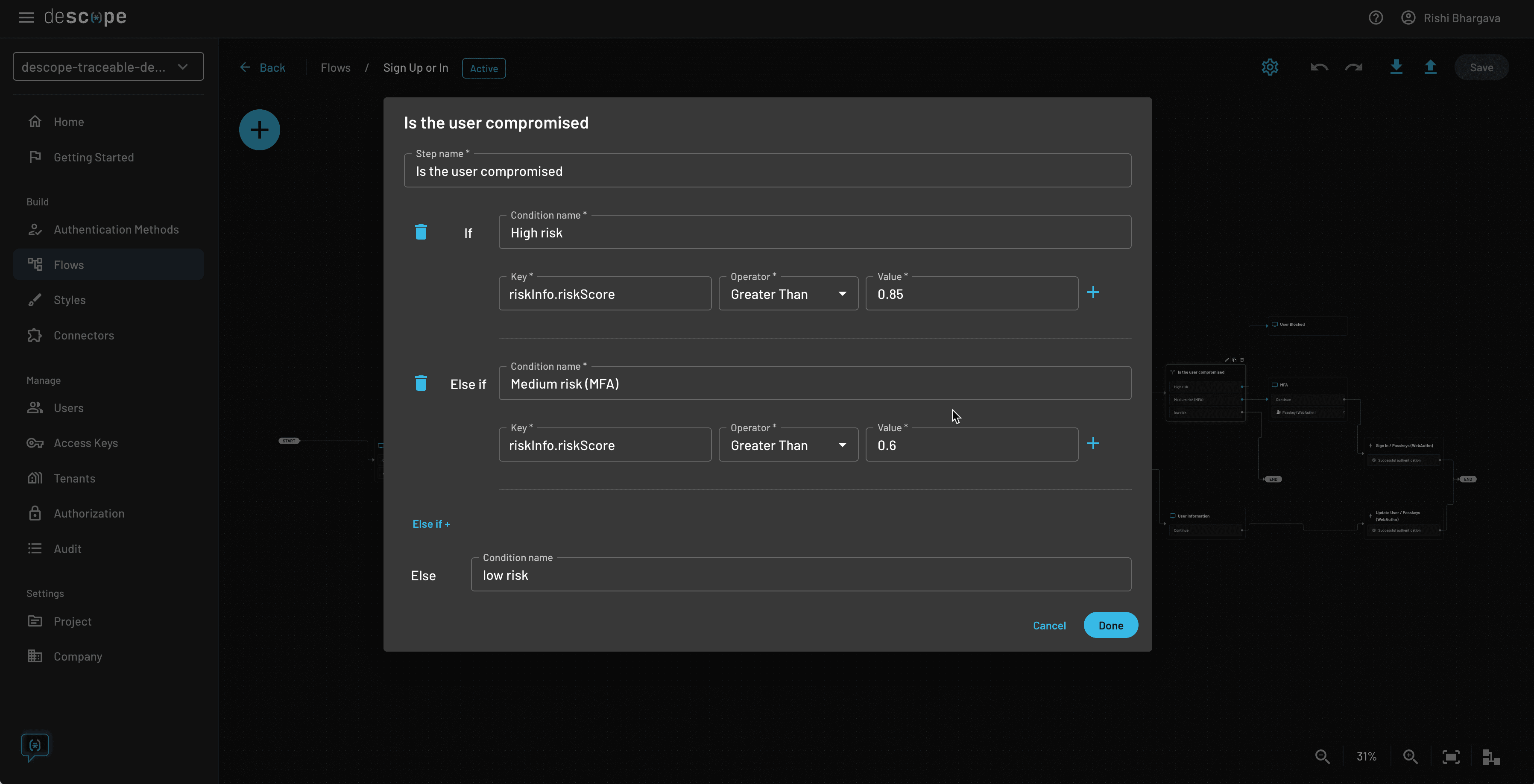
Developers can perform a variety of response actions in their Descope authentication flows based on the user risk score ingested from Traceable. For example, risk scores for returning user logins could be used to block users that are high-risk (as shown in the previous use case) and adding a biometrics-based MFA process for users that are medium-risk.
The Flow screenshot below highlights conditional step and different user paths:
The login screen below shows an end user with a medium-risk score experiencing risk-based MFA:

Conclusion
This connector combines the advanced, AI-driven behavioral intelligence of Traceable with the drag-and-drop authentication and user journeys of Descope to help developers easily add identity fraud prevention controls to their login flow.
If you haven’t yet started your Descope journey, sign up for a Free Forever account and set up your own Traceable connector. To explore other connectors, visit our integrations page.





