Table of Contents
MCP 101
Hello Descopers! We’re delighted to share our MCP Auth SDKs and APIs with you today to secure how remote MCP servers govern access for MCP clients and AI agents. Developers using the MCP Auth SDKs and APIs can easily add compliant, OAuth-based authorization to their MCP servers and deploy them seamlessly with a variety of platforms like Fly.io, Vercel, and Cloudflare Workers.
Our MCP Auth SDKs and APIs are available for every developer to use, including on our Free Forever tier. Sign up, view the docs, and explore our sample app to get started.

For more on the What, Why, and How of building production-ready MCP servers, keep on reading!
MCP 101
The Model Context Protocol (MCP), developed by Anthropic, standardizes the way LLMs (i.e. clients) interact with external tools or databases (i.e. servers) without developers spending time on understanding each tool’s API or managing custom integrations. MCP servers can run locally or remotely, enabling applications to provide scalable, straightforward access to AI agents.
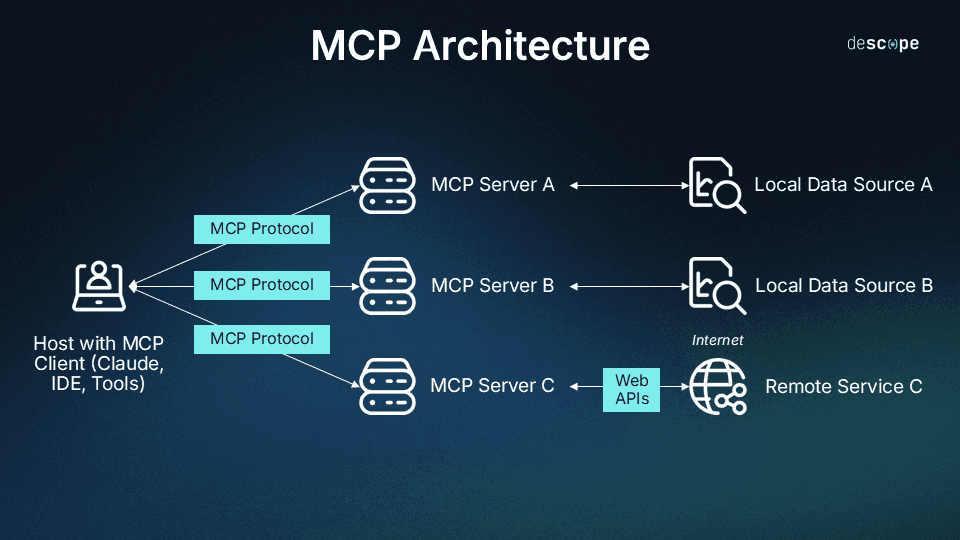
The speed with which the industry has converged on MCP as a preferred standard for AI system connectivity is heartening to see. With 1000s of MCP servers already live, enterprises like OpenAI, Microsoft, and Figma adopting the standard, and a robust, fast-moving roadmap, MCP has the potential to greatly accelerate AI adoption without sapping developer time.
Speaking of sapping developer time…
The MCP authorization rabbit hole
Developers building remote MCP servers run into a number of authentication and authorization related challenges:
Implementing and maintaining OAuth. While MCP recommends implementing OAuth 2.1 with PKCE, that’s much easier said than done. OAuth is a complex standard with several nuances that, if not taken care of, can lead to vulnerabilities and compromise. In addition, the MCP specification is constantly evolving, and even now there are serious discussions of already adopting new standards like Protected Resource Metadata (PRM) and other OAuth grant types.
Registering clients dynamically. While the typical OAuth 2.0 client registration process is manual, agentic systems can scale only if clients and servers can securely communicate without human interaction. This requires supporting Dynamic Client Registration (DCR) and Authorization Server Metadata (ASM), both supported by OAuth but leading to a lot of open questions and extra sprints for developers.
Governing fine-grained access. Just becoming OAuth-compliant doesn’t solve all authorization challenges. Developers need to think about defining tightly scoped access control for MCP clients, providing visibility to end users and IT admins to give consent in B2C or B2B settings, and adding mechanisms to revoke consent when the need arises.
Many of the building blocks are already present to make MCP deployments production-ready, but putting the building blocks together–and keeping them upright–shouldn’t end up being a Herculean effort for most developers.
That’s where the Descope MCP Auth SDKs and APIs come in.
Descope MCP Auth SDKs and APIs
The Descope MCP Auth SDKs help developers easily add OAuth-based authorization to their remote MCP servers. By protecting MCP servers with OAuth and abstracting away the complexity of authorization code flows, PKCE, client registration, and consent management, our SDKs give developers everything they need to build enterprise-grade MCP servers in three lines of code.
import { descopeMcpAuthRouter, descopeMcpBearerAuth } from "@descope/mcp-express";
app.use(descopeMcpAuthRouter());
app.use(["/mcp"], descopeMcpBearerAuth());The Descope MCP Auth SDKs and APIs help developers:
Secure remote MCP servers with OAuth 2.0 / 2.1 Authorization Code Flow
Define granular user, tenant, and permission scopes for what the AI agent / API can access via OAuth scopes
Programmatically create clients with Dynamic Client Registration and Authorization Server Metadata
Create and display consent screens to users and IT admins to ensure data privacy and least-privilege access
Easily manage all granted consents, view associated user identity information, and revoke access when needed
Check out the SDK README, a tutorial with Fly.io, and the sample app to try out the SDK for yourself. Our SDK is available in Express.js right now, with more planned in the coming weeks! Rest assured, we’ll keep up to date with changes to the MCP authorization specification to help you easily implement and keep up with best practices.
The video below shows the SDK in action with an example auth-protected remote MCP server that connects to the National Weather Service API for real-time weather updates.
Securing MCP servers with Inbound + Outbound Apps
In addition to using Descope’s MCP Auth SDKs, developers can build on Descope Inbound Apps and Outbound Apps APIs directly to support MCP authorization compliance and integrate external OAuth providers.
Our solutions are transport agnostic, so whether using Server-Sent Events (SSE) or Streamable HTTP, Descope has you covered. Our Descope AI monorepo shows how developers can directly integrate with Descope OAuth APIs in whatever framework they prefer to support ASM, DCR, Authorization Code Flow and more.
Descope + MCP use cases
Protecting MCP servers with OAuth providers
Developers can protect their MCP servers with enterprise-grade OAuth flows—supporting PKCE, dynamic client registration (DCR), authorization server metadata (ASM), consent management, and more. They can define MCP-specific scopes (e.g. models.invoke, context.read), configure token lifetimes, and restrict permissions to certain models, all while ensuring only MCP clients with the proper tokens can interact with the remote MCP server.
Connecting MCP clients with multiple MCP servers
Real-world MCP clients often interact with multiple MCP servers, with each server exposing its own API and requiring unique OAuth tokens. This creates a new challenge for developers: securely storing, managing, and rotating these tens (or hundreds) of server tokens.
Using Descope MCP Auth SDKs with Outbound Apps simplify this challenge by providing developers with a unified token manager across all MCP servers. Since each MCP server is ultimately an OAuth provider, Outbound Apps can handle consent, token exchange, storage, and renewal for each one.
Connecting MCP servers to OAuth providers
There are scenarios where MCP servers need to simultaneously act as an OAuth identity provider as well as a client (for example, when the server has to protect access to its own resources while accessing third-party services like Google or GitHub). By providing an integrated offering that builds in OAuth client capabilities to the OAuth provider flows, Descope helps MCP servers issue their own access tokens and manage third-party provider tokens to access user or tenant-specific resources.
Helping bring MCP to the masses
MCP has all the makings of a foundational protocol for the agentic age. Descope engineers are actively making open-source contributions to the TypeScript SDK, improving its documentation, and enhancing standardization efforts. But for MCP to truly gain mass adoption, AI developers need tools and enablement to abstract away the complexity of infrastructure-level flows like authentication and authorization so they can spend more time on core AI initiatives without making accidental security errors.
The Descope MCP Auth SDKs and APIs closes the authorization rabbit hole for developers building remote MCP servers while ensuring enterprise-grade security. Sign up for Descope to start securing remote MCP servers today and keep up with our AI launches. Have questions? Book a demo with our auth experts to learn more.