Table of Contents
Why do JWTs remain valid after logout?
JSON Web Tokens (JWTs) have become the standard for modern authentication and authorization, and with good reason—they’re efficient, scalable, and staggeringly simple. But security teams often raise a legitimate question about their lifespan after a session: “What happens to a JWT after a user logs out?”
The simple answer is that the token stays valid until it expires. At first blush, this behavior might appear to be a vulnerability, but it’s actually due to the stateless design that makes JWTs so useful. So, before raising the alarm, let’s take a moment to understand why this is a well-considered design choice rather than a hidden flaw.
If you're grappling with a pen test citing JWT invalidation, or if you’re concerned about the security implications of stateless tokens, this guide will show you why this design decision is deliberate—and how the real-world risks are both manageable and worth the trade-off.
Why do JWTs remain valid after logout?
JWTs are stateless—meaning they're completely self-contained. To illustrate this point, think of a server issuing a JWT as a venue giving out backstage passes for a concert. The pass itself (or JWT) contains all the information needed to verify the holder's identity and permissions. The venue (or server) doesn't keep a record of active backstage passes; it just knows how to check if one is genuine and unexpired when someone presents it.
When a JWT is issued, it includes a payload (e.g., user information and permissions) and an expiration time (exp claim). The server doesn't need to store the token or maintain session state. Instead, it simply verifies the token using a signing key whenever it is presented. Take a look at what a JWT template looks like in our docs.
This is fundamentally different from traditional session management, which requires servers to track every active user session in a database or memory. This creates several problems:
Every authentication check requires a database lookup
Session data must be synchronized across multiple servers
More users means more session storage and slower lookups
Server crashes can wipe out session data
Scaling becomes increasingly complex and expensive
Stateless design is what makes JWTs so scalable for modern web applications. Your authentication service can handle millions of users without maintaining session state across multiple servers. There's no need to synchronize session data across a cluster or check a central database for every request.
Since JWTs do not inherently involve server-side storage, there's no native way to invalidate a token before its expiration. After a user logs out, any issued access token is still cryptographically valid, which is the root of this perceived vulnerability.
Why isn’t this a security flaw?
When security teams first encounter JWT behavior after logout, their concern is understandable: "If a token is stolen, the attacker could still use it even after the user logs out." But this superficial view misses some crucial context about both the nature of token theft and how modern authentication actually works.
In reality, if an attacker manages to steal a JWT, the damage is already limited by design:
Limited time exposure: JWTs are typically configured with a short expiration time (e.g., 5-15 minutes for access tokens). This limits the window in which a token can be misused after a logout event.
Token scope: Access tokens are often scoped to specific resources and permissions, reducing the impact of compromise.
Threat model: In most cases, the biggest risk is token theft. If an attacker can steal a token, they can impersonate the user until it expires. This risk exists whether or not the user logs out.
In short, while this behavior may seem risky at first, it's not inherently insecure. Instead, it's a trade-off between performance and control. Statelessness allows systems to scale more easily because servers don't need to store or synchronize session data. Developers can accept this compromise because the risks are effectively mitigated with modern techniques.
Think about it this way: if an attacker has managed to steal a user's token, they've already breached more significant barriers. The real security focus should be on preventing token theft in the first place through proper storage, transport, and handling—areas where JWTs excel with their built-in validation and signing mechanisms.
Managing JWT logout in production
Building an effective JWT security strategy requires multiple layers of protection working together. While we can't invalidate tokens before expiration without compromising the benefits of being stateless, we can implement several practical safeguards that maintain both security and performance:
1. Start with short-lived access tokens
The simplest and most effective mitigation is time. Configure access tokens to expire in 5-15 minutes. Even if stolen, a token's usefulness is inherently limited, and regular refreshes create natural security boundaries.
2. Implement proper refresh token handling
Instead of long-lived access tokens, use short-lived access tokens alongside refresh tokens. Refresh tokens are typically stored securely (e.g., in HttpOnly cookies) and checked against server-side storage, making them revocable upon logout.
This approach gives you the best of both worlds:
Short-lived access tokens for performance
Revocable refresh tokens for security control
Immediate refresh token invalidation on logout
3. Secure your token storage
The biggest risk isn't the token's lifetime—it's token theft. Prevent token theft by ensuring tokens are securely stored on the client.
Store JWTs in
HttpOnlycookies to prevent XSS attacksUse secure storage mechanisms (e.g., Keychain or Secure Enclave) for mobile apps
Never store tokens in
localStorageorsessionStoragewhere they're exposed to JavaScript
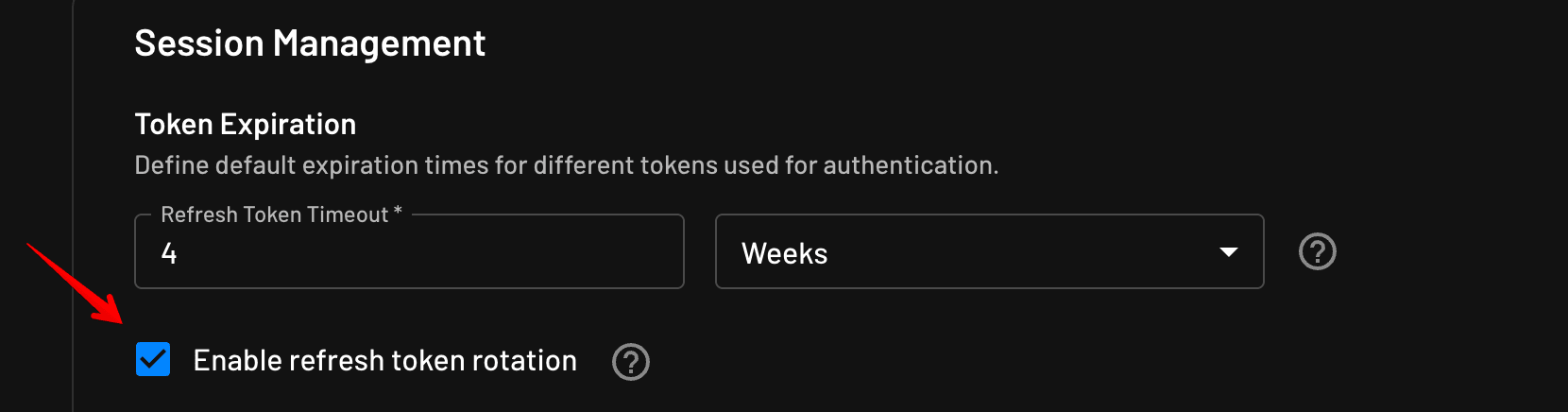
4. Enable token rotation
Require clients to exchange refresh tokens for new ones with each use. Each refresh token can only be used once, and using it automatically invalidates any previous refresh tokens. This limits the lifetime of any compromised refresh tokens and helps contain potential breaches.
5. Backend validation for sensitive actions
Don't rely solely on token validation for sensitive operations. Instead, use backend session validation:
Add server-side session checks for password changes and financial transactions
Require secondary authentication for credential updates
Validate the user's current session status
Balancing security and scalability
JWTs are not a one-size-fits-all solution, but their scalability and simplicity make them a strong choice for many applications. The logout challenge highlights the trade-offs inherent in stateless authentication. Developers and security practitioners need to weigh this balance based on their specific use case.
When statelessness is acceptable
Applications with low-risk user actions and short-lived tokens can safely rely on JWTs without a server-side blacklist. This includes scenarios where:
User actions have minimal security impact (e.g., a read-only API for public data or a news website)
Session hijacking wouldn't compromise sensitive data
The application needs to scale up considerably while retaining high performance
When to introduce statefulness
Applications handling sensitive data can maintain a server-side blacklist for access tokens. This means keeping a database of tokens that should no longer be considered valid, even if they haven't expired yet. Each time a token is presented, the server must check this blacklist before processing the request—effectively turning our stateless JWT back into a stateful session.
While this approach gives you the power to truly invalidate tokens on logout, it comes with a significant performance penalty. Every token validation now requires a database lookup, and the blacklist needs to be maintained, cleaned up, and synched.
The performance hit can be justified for use cases where:
User actions have high security impact
Private data could be compromised (e.g., healthcare)
Financial transactions are involved (e.g., payment processing, trading)
Scale or performance are secondary concerns
Logout-critical workflows are in use (e.g., account deactivation)
Why this trade-off makes design sense
The key to understanding JWT security is recognizing that no system is completely risk-free. The "logout problem" is not a failure of JWTs but a reflection of the inherent trade-offs in authentication design. By combining short-lived tokens, secure storage, and server-side checks for critical actions, developers can effectively mitigate the risks while enjoying the benefits of stateless authentication:
Limited exposure window: Even compromised tokens expire quickly
Constrained permissions: Tokens are scoped to specific resources
Layered security: Critical operations require additional verification
Performance at scale: No session lookups for routine operations
These mitigations reduce the potential impact of valid tokens remaining after logout, aligning security practices with real-world requirements for performance and usability.
Understanding the trade-offs in JWT design
The stateless design of JWTs requires thoughtful implementation to handle logout effectively. While the trade-offs might seem risky at first glance, they enable the performance and scalability that modern applications require. The key is implementing appropriate mitigations based on your security needs.
For most applications, a combination of short-lived tokens, secure storage practices, and additional verification for sensitive operations provides an effective balance. When stricter security is required, techniques like token blacklisting are available—though they come with their own complexity and performance costs.
Understanding these trade-offs enables informed decisions about session management in your applications. Rather than viewing JWT behavior after logout as a vulnerability, treat it as a design choice that requires appropriate controls.
Thanks for reading this blog! To keep up with the latest auth news and developer tools, subscribe to our blog or follow us on LinkedIn and Bluesky.