Table of Contents
What is an access token?
Understanding the difference between access and ID tokens is fundamental to building secure and efficient applications. While both token types stem from protocols such as OAuth 2.0 and OpenID Connect (OIDC), they serve distinct purposes in authentication and authorization.
This blog explores the nuances of access vs.ID tokens, offering insight into their unique roles and use cases.
What is an access token?
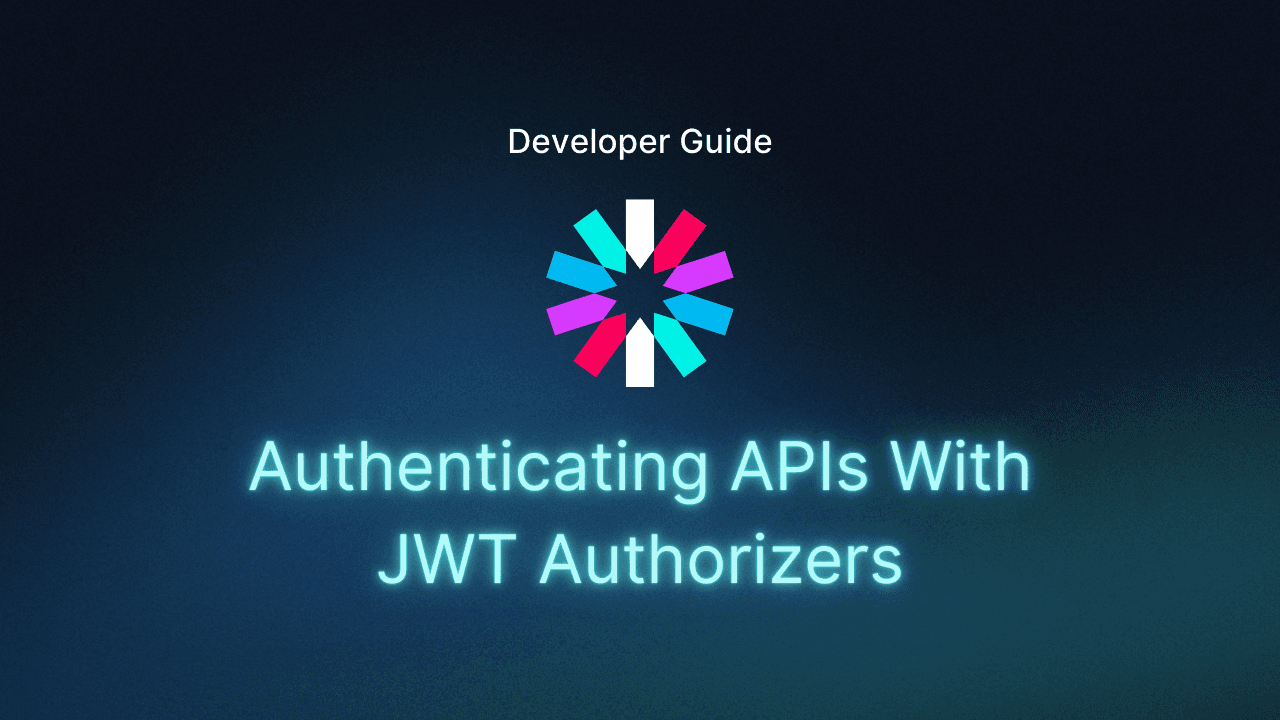
Access tokens are artifacts that enable swift, secure authorization to digital environments by generating an electronic key that contains users’ rights and permissions. This facilitates login and access management by allowing the user to move seamlessly through apps and programs without inputting their credentials repeatedly, all while keeping them and the system secure.
Access tokens typically use the JSON Web Token (JWT) and contain the following fields:
Authentication methods reference (
amr): How the token was createdExpiration time (
exp): When the token will expireIssued at (
iat): When the token was createdIssuer (
iss): Who or what issued the tokenSubject (
sub): Who the token is for/about
In terms of expiration, access tokens typically have configurable lifespans, but their default settings are often in the range of one to two hours. Microsoft access tokens, for example, are assigned random lifespans by default, ranging from 60 to 90 minutes and averaging 75 minutes.
What is an ID token?
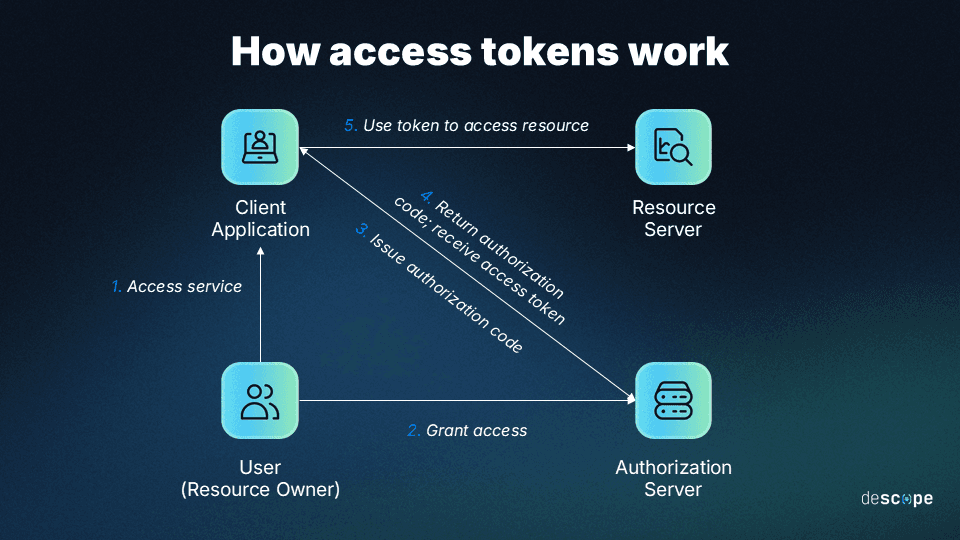
ID tokens are also digital artifacts that facilitate auth management, but they are primarily used for the authentication part of the process. As with access tokens, these are generated upon login and allow users to authenticate seamlessly rather than by re-entering credentials.
But, rather than confirming that a user has the right or ability to access a given piece of information, these tokens are used to confirm that a user is, in fact, who they claim to be.
A typical ID token has many of the same fields as an access token, with iss, sub, exp, and iat being used in both. However, it also usually includes information about the audience for the token (aud) and user information such as their name and email. Here is the typical order:
iss(a URL from which the token was generated)sub(a string of characters representing the user)aud(the programs intended to receive the token)exp(a Unix timestamp for when the token will expire)iat(a Unix timestamp for when the token was issued)name(the name of the user in question)email(the email address of that user)
Lifespan-wise, ID tokens usually last the length of an access session, being generated upon login and terminating at logout. This means that they can sometimes last longer than access tokens, even when an access token and ID token are generated at the same time.
ID tokens vs. access tokens at a glance
Access and ID tokens are one of the most effective approaches to secure authorization and authentication, respectively, and they’re often used together. However, there are important differences between them and cases where developers should choose one over the other.
Here’s how the two types of tokens stack up across the most important categories:
Access Tokens | ID Tokens | |
|---|---|---|
Purpose | Granting or confirming a user’s access (authorization) | Verifying a user’s identity (authentication) |
Scope | Permissions and scopes of user access rights | User information and claims about their identity |
Use case | Sent between APIs to facilitate data access | Confirming identity within a client application |
Lifespan | Configurable but typically between 60 and 90 minutes | Typically coextensive with a user’s access session |
File format | JWT or proprietary to an application (opaque) | JWT with standardized contents (see above) |
The biggest difference between the two tokens is their purpose. Access tokens facilitate access, whereas ID tokens facilitate identification.
Access tokens vs. ID tokens vs. refresh tokens
In addition to access and ID tokens, there are also refresh tokens that many auth systems create to further facilitate authentication and authorization. Refresh tokens are typically generated alongside access tokens, and they include information that allows for the access token to be regenerated at a specified time, extending access while maintaining security.
While refresh tokens are primarily used in conjunction with access tokens, all three main types of tokens work together to make token-based authentication one of the best options for any software project. ID tokens allow for seamless user authentication, and access tokens then allow that authenticated user to exercise their access privileges swiftly and easily. Finally, refresh tokens ensure that frictionless access is maintained longer-term, optimizing UX.
Also Read: Understanding the Differences Between Access and Refresh Tokens
When to use each type of token
Each token’s specific purpose dictates how and when it should be used. Basing auth around access tokens makes the most sense when the primary element that needs to be managed is user access privileges. Using ID tokens makes the most sense when strong authentication is what matters most—or in environments where users need to authenticate repeatedly.
And, on the level of use case and interface, access tokens are commonly used with Open Authorization (OAuth) 2.0, while both access and ID tokens are often used with OIDC.
In most cases, using access and ID tokens—along with refresh tokens—is the best option for developers, managers, and end users.
Simple token management with Descope
For a live deployment, it's essential to implement extra safeguards like secure communication protocols, cryptographic verification of tokens, and thorough exception management. It's also worth exploring more sophisticated identity management solutions and data storage platforms that align with your particular security needs and growth projections.
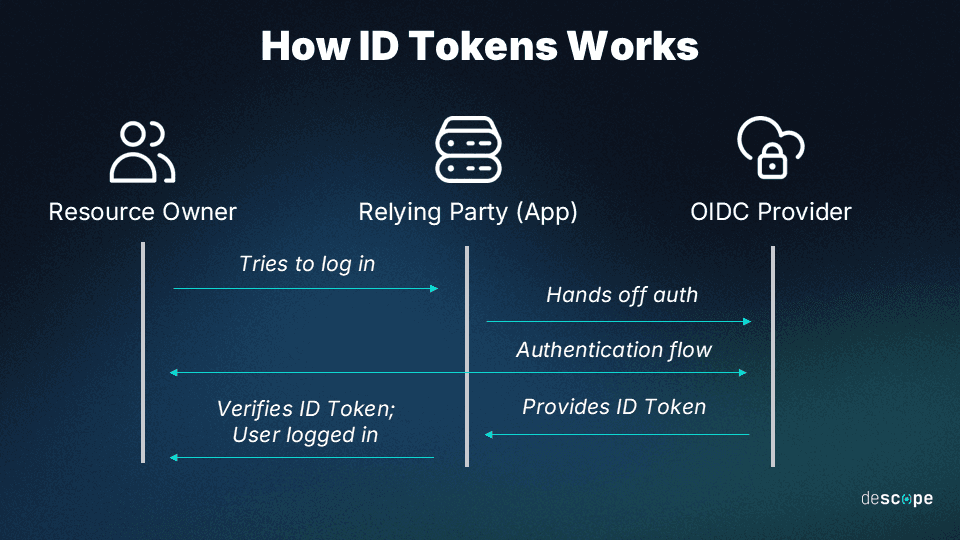
Nevertheless, building such advanced security features from the ground up can be challenging. This is where utilizing a dedicated identity and access management solution like Descope becomes invaluable. For engineers integrating Descope, enabling refresh token rotation is as simple as toggling a single checkbox.
Looking to streamline token management in your application? Descope’s no/low code CIAM platform is designed to help organizations effortlessly incorporate authentication and authorization through intuitive drag & drop workflows.
Sign up for a Free Forever account or schedule a consultation with our experts to get started.