Table of Contents
About Google reCAPTCHA Enterprise
Protecting against bot attacks and account takeover attempts are a challenge for organizations of all sizes. Bots accounted for around half of all Internet traffic in 2022 according to Imperva, pointing to their continued prevalence and success. Account takeover also continues to rise and tangibly affect business – research from Sift found that around half of respondents would stop using a site or app entirely if they suffered an ATO attack.
Descope’s connector with Google reCAPTCHA Enterprise enables developers to add deep, contextual user risk data to their authentication and user journey flows. Organizations using the connector can mitigate bot traffic and credential stuffing, stop account takeover attempts, and add MFA for risky users.
About Google reCAPTCHA Enterprise
reCAPTCHA Enterprise protects apps and websites from fraudulent activity, spam, and abuse without causing friction for real users. The service employs advanced machine learning algorithms to analyze user behavior and assess risk levels in real time. The added functionality of reCAPTCHA Enterprise account defender also helps protect against subtle, site-specific abuse.
reCAPTCHA Enterprise is based on the reCAPTCHA technology, which has helped defend more than 5 million sites over the past decade.
Connector overview
The Descope connector with reCAPTCHA Enterprise enables developers to:
Ingest granular user risk scores from reCAPTCHA Enterprise into Descope authentication and user journey flows.
Annotate and send updated user risk scores back to reCAPTCHA Enterprise to better train global and site-specific models to learn with time.
Create branching user journey paths in Descope authentication flows based on the severity of the risk scores provided by reCAPTCHA Enterprise.
Ingest account defender data from reCAPTCHA Enterprise to help identify and respond to site-specific abuse.
Orchestrate user journeys in a no-code workflow combining reCAPTCHA Enterprise data alongside data from other risk protection tools such as Traceable and Amazon Rekognition.

Use case: Bot protection
Attackers bombarding login and signup pages with spam, bots, and credential stuffing attacks can significantly impact user experience as well as business results. With Descope Flows, developers can use risk scores provided by reCAPTCHA Enterprise to block high-risk logins and show them a separate message that their account may be compromised.
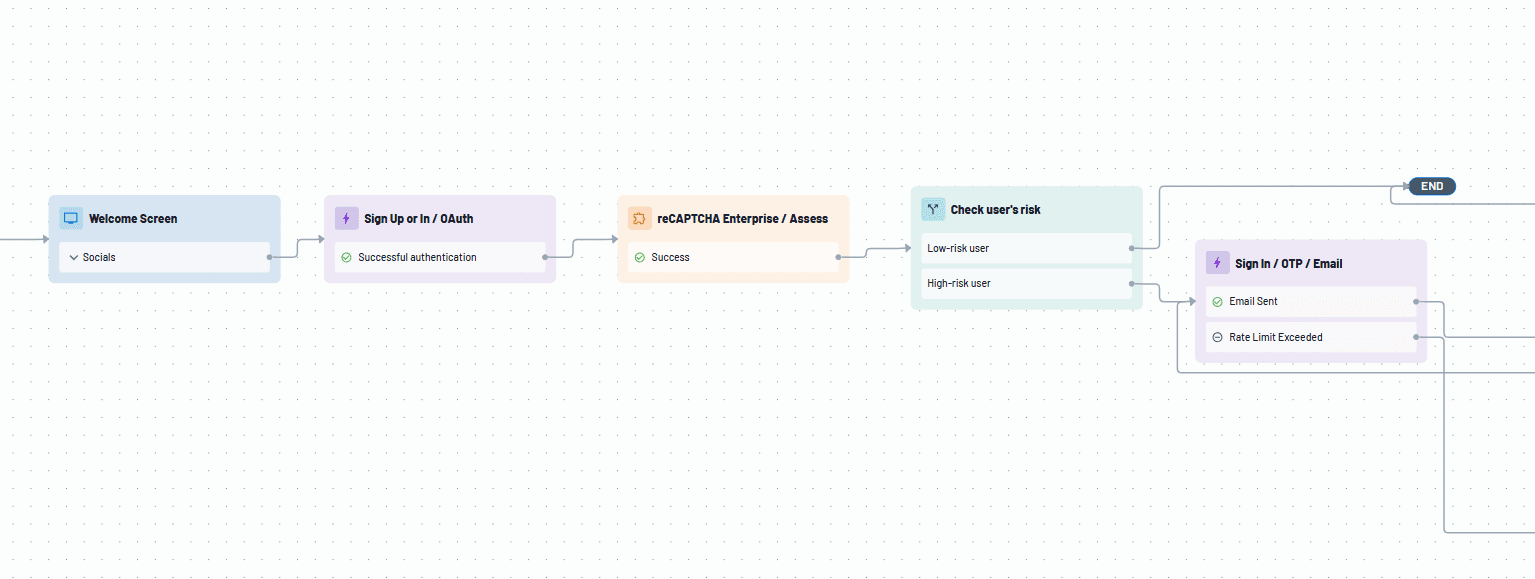
The Flow below defines an authentication process where logins with a high risk score are shown a “blocked” message during signup. Users with medium / low risk scores are funneled into a standard login flow using password and SMS OTP.

The screens below show the signup experience with reCAPTCHA embedded:

Use case: Risk-based MFA for returning users
Enforcing MFA during every login attempt often leads to undue user friction, negatively affecting adoption and retention. Using Descope and reCAPTCHA Enterprise, developers can employ a more nuanced risk-based MFA approach that asks for a second factor only if the login is considered suspicious or fraudulent. This approach enforces the right security control at the right time without affecting the experience of frequent, legitimate end users.
The Flow below defines a process where user risk provided by reCAPTCHA Enterprise is checked during sign-in and an OTP second factor is requested for medium to high risk login attempts. After successful authentication, the “Annotate” action is run to share data back with reCAPTCHA Enterprise and further refine its learning models.
The screenshot below shows the "Annotate" action in use:

Conclusion
This connector combines the advanced machine learning capabilities of reCAPTCHA Enterprise with the drag-and-drop authentication and user journeys of Descope to help developers easily add identity fraud prevention controls to their login flow.
If you haven’t yet started your Descope journey, sign up for a Free Forever account and set up your own reCAPTCHA Enterprise connector. To explore other connectors, visit our integrations page.






