Table of Contents
1. Growing adoption across diverse userbases
In digital security, the shift away from traditional passwords is unmistakable. With Google steering away from passwords, both B2B and B2C businesses are seeking new authentication solutions that blend accessibility, security, and user satisfaction.
At the forefront of this transformation is biometric authentication— fast gaining mindshare from end users across the globe.
Imagine logging in to your applications with just a glance at the phone camera or a swipe of the finger. Imagining this shouldn’t be tough, since many users unlock their phones and other computing devices through these methods already!
Let’s uncover three of the core benefits that are making biometric authentication a go-to option for many application builders.
1. Growing adoption across diverse userbases
A 2022 study reveals that a majority of Americans incorporate biometric auth in their daily lives. Accessibility is a key factor, with 68% using it to unlock personal devices and 51% to log in to apps.
Looking more closely at the data, 40% said they use face recognition to access at least one app per day. However, the adoption for younger users (aged 18-34) is 75%. This suggests that the share of users who depend on biometric authentication in their daily lives will increase over time.
Crucially, biometric auth can cater to both customer and workforce authentication. While customers prefer biometrics for the fast and seamless user experience it provides, workforce use cases stem from the strong security inherent in this technology. Let’s cover more on the security aspects in the next section.
2. Strengthened security and privacy
One of the reasons biometrics is growing in popularity is its inherent security advantages. It offers more privacy and security assurance by default than many other authentication and access management systems.
Consider the logistics of account compromise in more traditional auth methods compared to a baseline fingerprint auth or facial recognition auth deployment. Cybercriminals can gain illegitimate access to an account by guessing or cracking knowledge factors like passwords or security questions. This remains the case even if more than one factor is required, as in baseline multi-factor authentication (MFA).
However, if access to the user’s account requires confirmation of their identity via face scan, the attacker’s options for access are severely limited. Additionally, adding biometric factors to MFA deployments is one of the best ways to strengthen them. Advanced systems like phishing-resistant MFA often make use of fingerprint, facial, or retinal scans.
When it comes to privacy, conventional user concerns about biometrics are unfounded. People often think that their biometric data is shared with apps or other parties when they use these methods for authentication. However, biometrics based on technologies such as WebAuthn and passkeys take a very privacy-friendly approach.
Users’ biometric data is only stored locally on their devices and never shared with any other party.
Using biometrics unlocks a private key on the users’ device, which is then matched with a public key on the server of the app they are trying to access.
Beyond personal use, biometric auth serves a wide variety of use cases because it offers a level of security that sensitive organizations require. Along with the individual privacy assurances noted above, it also helps protect organizations from data breaches due to cybercrime, mismanaged credentials, and broken authentication.
3. Unparalleled user experience
Another primary reason biometric auth is so widespread is the UX factor. Biometric auth is among the easiest methods for end users to acclimate to, largely because it’s already used on their personal devices.
Biometric authentication enhances the overall user experience by offering unparalleled convenience. Users no longer need to remember complex passwords, resulting in a smoother, more efficient authentication process.
Character requirements and mandated password updates often complicate password memorization, while biometric auth requires little to no mental load. This, in turn, leads to a better UX, which comes with its own set of benefits:
Better UX results in faster user onboarding, which in turn powers retention.
Employees who spend fewer mental resources on logging in are better prepared to be productive workers.
IT departments that spend less time helping employees or end users troubleshoot have more bandwidth for other tasks.
Bringing things full circle, these same UX factors that make logging in easier for users make illegitimate access harder for would-be attackers. Not having passwords or other credentials to remember means there are no knowledge-based credentials to steal.
In an environment where over 86% of web-based cyberattacks involve stolen credentials, taking that option off the table for attackers—while simultaneously making it easier for users to log in—is a win-win.
Other biometric auth considerations
One potential obstacle to biometric authentication comes from users’ inability or unwillingness to use their biometric identifiers. For this reason, users may require training on properly using biometric scanners to ensure ease of adoption.
If users are concerned about the collection and potential uses of their biometric data and reluctant to provide a scan, raising awareness about the privacy-first nature of FIDO-based biometrics is important.
Beyond individual users’ concerns, the sum total of their rights concerning personal data collection is the subject of many privacy regulations, like the Biometric Information Privacy Act (BIPA). Be sure to seek out a biometric auth solution that meets your users’ expectations and your compliance needs. As mentioned earlier, FIDO authentication turns this potential weakness into a point of strength.
Another concern is that not all devices have the same capacities for biometric auth. Some utilize face or retinal scans, while others use fingerprint authentication instead. However, most devices released within the past half-decade accommodate some form of biometric auth. A flexible solution allows you to keep your login secure regardless of which devices end users have.
The best approach is a dynamic system with alternative and fallback options alongside biometric authentication.
No / low code biometrics for your app with Descope
Biometric auth unlocks a more intuitive, secure, and user-friendly digital experience. Seamless adoption, strengthened security, top-notch privacy, and enhanced user experience position biometric authentication as a cornerstone of how people will access apps online in the months and years to come.
However, building biometric authentication functionality in-house can be complex and time-consuming, requiring developers to learn and implement protocols such as FIDO2 and WebAuthn as well as maintain these systems once implemented.
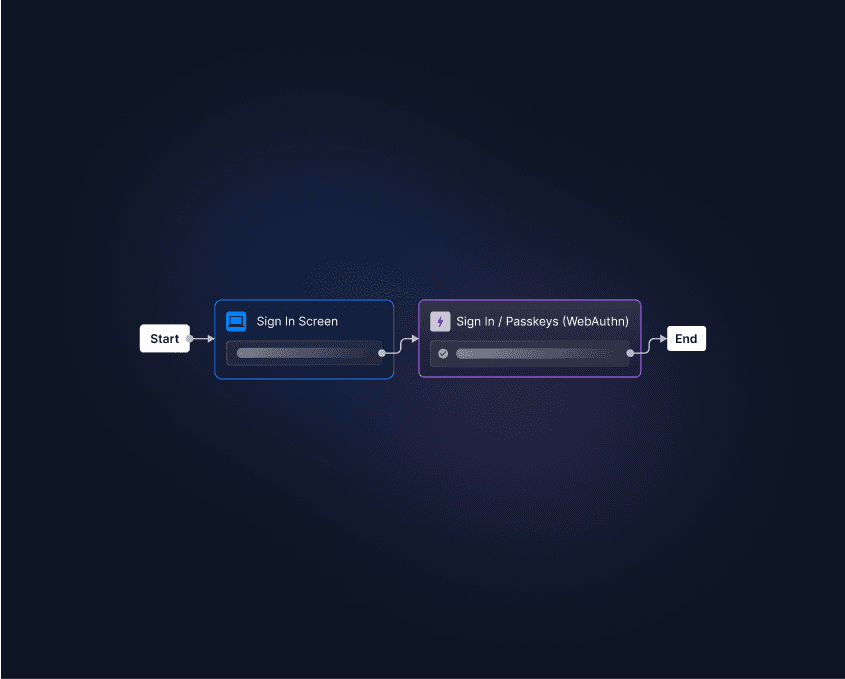
Descope can help. Our no / low code CIAM solution helps organizations easily add passkeys to their apps using drag-and-drop workflows and a few lines of code. Support for passkeys autofill, multi-device credentials, and fallback options mean that Descope customers can deploy mature, enterprise-ready biometric auth in a matter of days and weeks instead of months and years.
Sign up for a Free Forever account to get started with Descope. Have questions about our platform? Book time with our auth experts.