Table of Contents
What is a YubiKey?
According to the 2024 Verizon Data Breach Investigation Report, 7 out of 10 cybercriminals prefer targeting users over attacking IT infrastructure. This preference isn’t surprising: humans, not firewalls, are susceptible to phishing (social engineering attacks that steal login credentials). While MFA (multi-factor authentication) is widely accepted as phishing-resistant using any combination of factors, leveraging possession-based authentication has emerged as the gold standard today.
Unlike knowledge-based authentication, the possession factor establishes user presence. Thanks to the proliferation of smartphones, virtually everyone can leverage the possession factor for 2FA (two-factor authentication). But for companies and customers who want to improve their possession-based authentication security even further, YubiKeys provide the perfect combination of resilience and convenience.
This article explores how YubiKeys work, how they differ from other authentication methods, and common YubiKey use cases. Lastly, we’ll cover some key benefits to help you determine if they’re right for you.
What is a YubiKey?
A YubiKey is a hardware security device that provides strong authentication when accessing computers, networks, and online services. Yubico developed these small USB or NFC-enabled keys as a physical component in two-factor or multi-factor authentication systems.
Like a door key with ridges that turn physical tumblers, YubiKeys unlock digital assets by performing operations using cryptographic keys. When a user attempts to log in to a supported service, the cryptographic keys stored on the YubiKey prove the user’s identity. Combined with another factor like a password or PIN, YubiKeys provide possession-based 2FA.
YubiKeys support multiple authentication protocols and systems, including:
FIDO2/U2F: Using the WebAuthn API and CTAP protocol, enables passwordless 2FA.
OTP (One-Time Passcode/Password): Generates single-use codes.
Passkeys: A modern standard for passwordless authentication across devices.
Although they’re often regarded as a higher-friction authentication tool, YubiKeys are designed to be fast and user-friendly. They often require little more than a USB connection or a single tap followed by a PIN to authenticate.
While some YubiKeys feature built-in biometric scanners (for fingerprint authentication) and are more delicate, most models are extremely resistant to damage. Non-biometric YubiKeys are also built to be more durable than smartphones, with no moving parts or batteries. YubiKeys are resistant to water, crushing, and other forms of physical harm.
YubiKey vs. passkey vs. authenticator app
To fully understand their place in the authentication ecosystem, it’s helpful to compare YubiKeys with other popular methods. First, let’s discuss their relationship with passkeys, which are a form of cross-device passwordless authentication built atop the FIDO2 protocol.
YubiKey vs. passkey
The most obvious difference between YubiKeys and passkeys is that YubiKeys are physical devices, and passkeys are FIDO2-based credentials. However, YubiKeys and passkeys aren’t mutually exclusive. As Yubico’s FAQ on passkeys phrases it, “They’re the same, and they’re different.”
They're similar because passkeys are built on the same PKI (public-key infrastructure) that YubiKeys used since 2018. YubiKeys can currently store up to 25 different passkeys, though Yubico intends to expand this as the market for passwordless implementation grows.
They’re different because YubiKey passkeys and standard passkeys follow different rules for cross-device duplication. Passkeys on most devices can be copied using the associated cloud account’s credentials. Passkeys on YubiKeys are bound to the device and can’t be copied.
Here’s a breakdown of how YubiKeys and passkeys compare with one another:
YubiKey passkey | Standard passkey | |
|---|---|---|
Storage | Device-bound in the YubiKey’s hardware, making them impossible to copy. | Stored on cloud services and within each associated device’s TPM (Trusted Platform Module), a dedicated component for protecting authentication secrets. |
Portability | Tied to the physical device, supporting possession-based 2FA by requiring the key’s presence. | Can be synced across trusted devices, offering more convenience but potentially increasing the attack surface. |
Security | Designed with hardware-level protection against extraction or duplication. | Rely on the security of the device or cloud service provider. |
YubiKey vs. authenticator app
Both YubiKeys and authenticator apps (Google Authenticator, Authy, etc.) provide two-factor authentication, but they differ in several key ways. Let’s start with hardware security.
While modern smartphones contain dedicated TPMs, that doesn’t make them impervious to malware or remote attacks. Most cybercriminals won’t target an authenticator app, but a phone’s operating system is comparatively easy to infect—especially when unassuming users install risky apps and allow unfettered access, options that simply don’t exist for YubiKeys.
It’s worth noting that most cryptographic operations take place in a Trusted Execution Environment (Android) or Secure Enclave (Apple), a portion of the processor that runs its own operating system. However, an authenticator app’s secrets needn’t be breached to steal an OTP, and the risk of malware is still present. On the other hand, YubiKeys are built to resist attack and live in isolation from other software.
Next is form factor and dependency. The YubiKey is an unpowered, flash drive-sized device dedicated to authentication, and a smartphone is much larger and requires power to function. An authenticator app can add login friction due to its need for electricity, forcing users with dead phones to find a charger and wait.
Last but not least are the OTPs themselves. While authenticator apps and YubiKeys support time-based (TOTP) and counter-based (HOTP) one-time passcodes, their delivery and security features are completely different. YubiKeys produce 44-character OTPs that require minimal user action. The authentication secrets (seeds) a YubiKey uses to generate OTPs are backed by AES-128 encryption, shielding them from direct attack.
Conversely, authenticator apps generate six-digit codes that must be entered manually, allowing a scammer to phish them. The security surrounding underlying authentication secrets can vary, with most relying on a combination of dedicated hardware and operating system-specific key storage.
Below is a breakdown of how YubiKeys and authenticator apps stack up with each other:
YubiKey | Authenticator app (smartphone) | |
|---|---|---|
Security | Isolated from vulnerable operating systems and apps. | Although resilient against direct attack, it exists alongside exploitable software. |
Dependency | Compact, never needs to be updated, and doesn’t require batteries to operate. | Can be bulky, may require software updates, and needs a charged battery. |
Durability | Extremely tough against physical force. Difficult to break or crush, and water-resistant. | Able to withstand minor damage, but still fragile and susceptible to water damage. |
One-Time Passcodes | Produce 44-character OTPs backed by 128-bit encryption, and automatically enter codes when prompted. | Generate six-digit passcodes that require manual user entry. Encryption of OTP seeds varies based on OS and device. |
How YubiKey authentication works
YubiKey authentication leverages the principle of possession-based, two-factor authentication (2FA). It combines something you have (a YubiKey) with something you know (a PIN or password), or in the case of biometric-enabled YubiKeys, something you are (your fingerprint scan).
The YubiKey stores authentication credentials and performs cryptographic operations, never exposing the secret keys. This closed-loop process ensures that even if a user’s password is compromised, an attacker can’t gain access without physical possession of the key and its associated PIN.
Below, we’ve outlined the steps required to authenticate using YubiKeys with passkeys.
Passkey authentication with YubiKey
Passkeys use public-key cryptography or PKI (public-key infrastructure) to provide a phishing-resistant authentication process. Here’s how it works with a YubiKey:
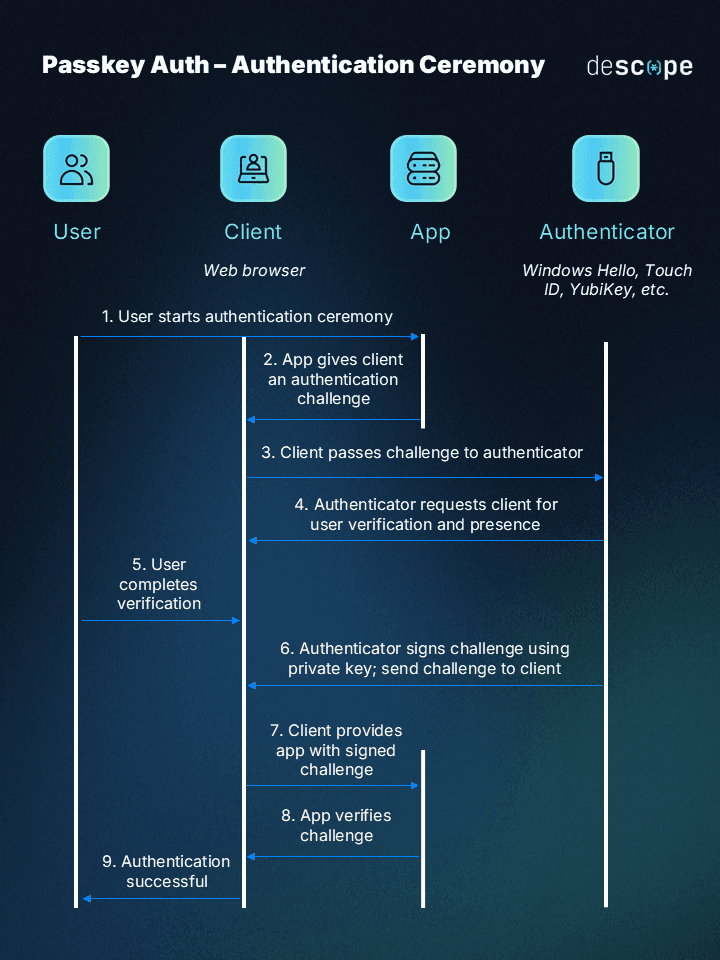
Initiation: The user starts the authentication ceremony by attempting to log in to an app or service that supports passkey authentication.
Challenge creation: The app generates a cryptographic authentication challenge and sends it to the client (the browser or device).
Challenge transmission: The client passes this challenge to the authenticator (in this case, the YubiKey).
Verification request: The YubiKey requests user verification and presence from the client.
PIN entry or biometric scan: When prompted, the user enters their PIN or scans their fingerprint.
Challenge signing: Upon successful verification, the YubiKey (the authenticator) uses its stored private key to sign the challenge. It then sends the signed challenge to the client.
Response submission: The client provides the app with the signed challenge from the YubiKey.
Verification: The service verifies the signed challenge using the corresponding public key associated with the user’s account.
Authentication complete: If the verification is successful, the app confirms the authentication, granting the user access.
OTP authentication with YubiKey
YubiKeys can also authenticate using OTPs (One-Time Passwords/Passcodes), but the process is slightly different. Like all OTPs, YubiKeys generate one-time passcodes based on two elements:
A seed, which is a static secret key shared between the YubiKey and the server.
A moving factor, which can be time-based or counter-based, depending on the OTP type (time-based or counter-based, TOTP or HOTP).
For a more extensive exploration of OTPs check out our guide, OTP Authentication Explained: Definition, Uses & Benefits.
Notably, YubiKey OTPs differ from the standard six-digit codes an authenticator app provides. Instead, they are highly complex, 44-character strings with 128-bit encryption, making them nearly impossible to spoof. Here’s how it works:

Initiation: The user attempts to log in to an app or service that supports YubiKey OTP.
OTP generation: When prompted, the user connects their YubiKey and activates it. In most cases, this is simply touching a sensor on the YubiKey. The YubiKey generates a unique OTP based on the seed and moving factor.
OTP submission: The client (browser or app) sends this OTP to the service.
Verification: The service validates the OTP, either using Yubico’s validation servers or (in the case of an enterprise setup) the organization’s validation server.
Authentication complete: After receiving a successful validation result from Yubico or the private server, the app or service grants the user access.
Common YubiKey use cases
Because YubiKeys support both OTP and passkey authentication, they support use cases across a wide range of industries and activities. Below are just a few examples of how phishing-resistant YubiKeys can uplevel security in various scenarios.
Workforce MFA for remote workers
With remote work becoming increasingly common, organizations can use YubiKeys to ensure secure access to company resources from any location. Remote employees can use YubiKeys for stronger authentication, logging in to corporate networks, cloud services, and sensitive applications. Companies with older, legacy frameworks can opt for OTP-based authentication, while more modern systems can benefit from passkey-enabled passwordless login.
Upgrading individual security
Some individuals prefer YubiKeys when logging in to consumer applications, and offering YubiKey support on your app or service can help satisfy these security-conscious customers. Because one YubiKey supports up to 25 different passkeys, these users can benefit from possession-based security across multiple services without adding another link to their real-world keychain. Even if your app isn’t ready to support passkeys, you can still work with YubiKeys using OTPs.
Government officials and sensitive industries
YubiKeys can be pivotal in high-security scenarios where protecting privileged data is an operational requirement. Government agencies, defense contractors, and critical infrastructure operators use YubiKeys to secure classified information and sensitive systems. In environments where regulatory compliance demands traditional smart card functionality, YubiKeys can double as a digital and physical access device.
YubiKey benefits
While YubiKeys are certainly multi-faceted security devices, we’ve distilled their key benefits into three concise categories: security, user experience, and reliability.
Enhanced security
YubiKeys offer robust, resilient protection against numerous cyber threats. They provide phishing-resistant authentication through hardware-bound passkeys, significantly reducing the risk of ATO (account takeover). Unlike smartphones or traditional OTP methods, YubiKeys require physical presence for authentication, effectively eliminating risks associated with remote attacks and credential theft. In short, YubiKeys can’t be duplicated, hijacked, monitored, or interfered with.
Case in point: Cloudflare stopped a 2022 SMS phishing attack targeting its workforce using FIDO2-compliant Yubikeys.
Improved user experience
While they may appear more cumbersome, YubiKeys can quickly surpass a smartphone’s speed and accessibility. Authentication with a YubiKey is often as simple as inserting the key and tapping it or using NFC, then entering a short PIN. This is typically faster and more convenient than a long, hard-to-remember password, and it’s much speedier and more secure than manually submitting an OTP.
Additionally, YubiKeys don’t require a power adapter, their form factor can be extremely compact, and they don’t require constant software updates.
Reliability and durability
YubiKeys are designed to withstand much more than daily wear and tear, offering greater protection compared to smartphones. They’re resistant to water and crushing, and they have no moving parts or battery to short-circuit. YubiKeys’ physical ruggedness makes them ideally suited for a wide range of environments, from field operations to heavy industry.
Because of their long lifespan, YubiKeys are a highly cost-effective alternative to issuing company smartphones and are much more secure than a BYOD (Bring Your Own Device) policy.
Easily support YubiKey authentication with Descope
YubiKeys offer a powerful solution for reinforcing authentication security across countless industries and use cases. They’re physically tough, phishing-resistant, and built on dedicated hardware proven to defend against cyber threats. With strong authentication options for both passkeys and OTPs, YubiKeys address many of the security obstacles organizations and individuals face daily.
While YubiKey authentication can significantly boost your security posture, integrating it with your systems, service, or app can be difficult and complex. At Descope, we make development easier regardless of the authentication method. Adding passkeys with Descope Flows is as easy as selecting an authentication type, picking a login screen, and deploying.
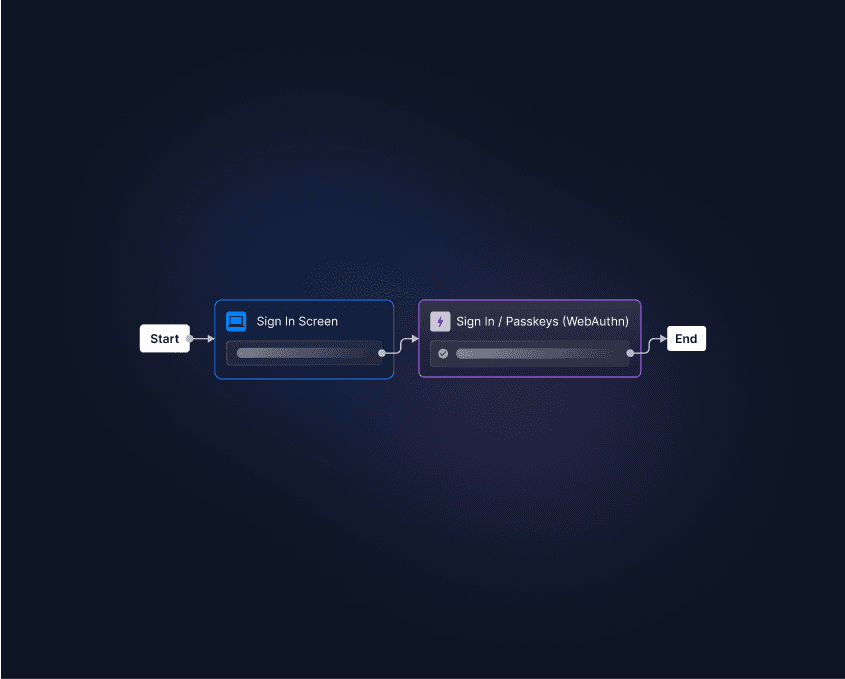
Descope’s flexible platform empowers developers to quickly and effortlessly implement YubiKey authentication, combining the security benefits of possession-based authentication with the accessibility of our drag-and-drop interface.
To get started integrating YubiKeys with passkeys or OTPs using Descope, sign up for our “Free Forever” plan today. Have questions? We’re waiting to connect with you at AuthTown, our open developer community.





