Table of Contents
What is user provisioning?
A recent study found that internet users have about 170 passwords on average, more than double 2020’s average of 80 per person. Across all of these passwords and accounts, there’s a real need for synergistic management to prevent security risks and bolster the user experience.
Enter user provisioning, a crucial element of identity and access management (IAM), especially at the enterprise level. With sound provisioning, organizations can manage user accounts at scale and with ease, which benefits users themselves, internal resource management, and all other stakeholders.
What is user provisioning?
User provisioning is a systematic approach to managing user accounts at scale. It involves all tasks related to managing the lifecycle of user identities across various platforms, including the assignment of roles, permissions, and credentials. It unifies create, read, update, and delete (CRUD) functions for easier management, more productivity, tighter security, and a better overall user experience.
In general, user provisioning works as an intelligence management suite that indexes users’ account data and updates it dynamically across accounts—see below for a deep dive into how.
In terms of use cases in a professional setting, it is leveraged for both personnel and clientele.
Staff, contractors, strategic partners, and other stakeholders with internal access depend on provisioning systems to access the data and systems they need for everyday tasks swiftly and easily. Ever-evolving tech stacks eat into productivity with excessive login, authentication, and re-authentication practices. Provisioning user data between accounts speeds up all processes.
For IAM specifically, provisioning plays a key role in enhancing security, compliance, and operational efficiency by ensuring that access rights are granted according to predefined policies and are revoked when no longer needed.
How user provisioning works
User provisioning can be achieved in several different ways. In the most basic systems, manual processes for account management might be employed. But mature systems overseeing large numbers of users often utilize software solutions to automate and optimize processes.
One such example is SCIM, or system for cross-domain identity management. SCIM uses both JavaScript object notation (JSON) and representational state transfer (REST) to transmit key account information between domains swiftly and securely, streamlining synchronization.
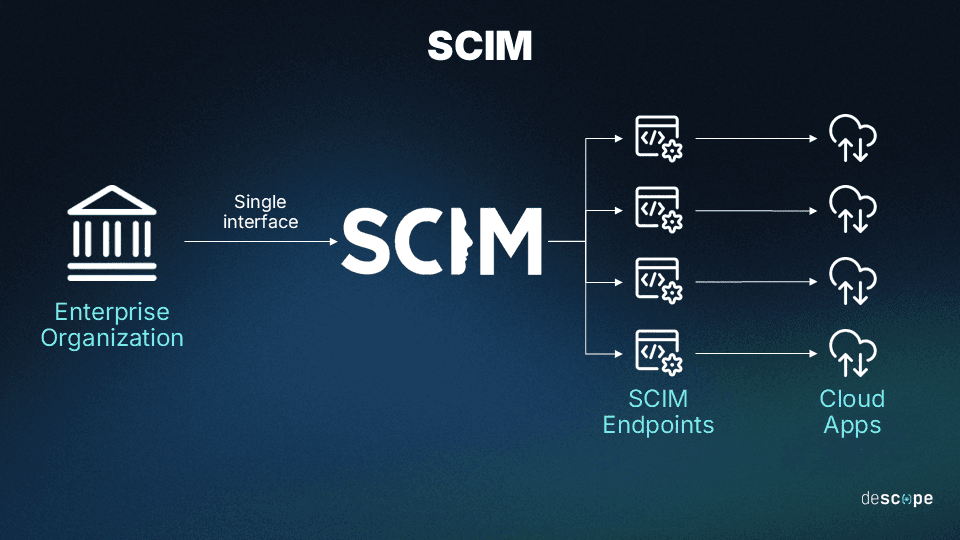
Whichever means or methods are used, the processes that need to be accounted for include:
User creation: Users are added to a system and have their accounts configured with all relevant personal information. Ideally, this is coordinated in close collaboration with HR.
Access rights assignment: Users are assigned roles, responsibilities, and other key factors determining their access rights. Typically, access rights are granted in accordance with predefined organizational policies, ensuring compliance and adherence to the principle of least privilege.
User maintenance: Users’ accounts and information are monitored and adjusted over time as their roles and responsibilities change, keeping authorization accurate across platforms.
User deprovisioning: Users are safely removed from systems when necessary (for instance, when an employee leaves a company), and all data is safely disposed of except any necessary for compliance, security, or other reasons. Regular clean-up processes ensure user access remains up-to-date and compliant with organizational policies.
Many organizations turn to third-party providers to enact user provisioning across interwoven systems. Whether in a standalone product or an identity as a service (IDaaS) model, third-party provisioning gives companies of all kinds and sizes access to efficient account management.
Benefits of user provisioning
User provisioning allows organizations to achieve greater security assurance through proper access control across any and all systems they use or are connected to. It centralizes users’ important account information, including use and behavior history, into a single accessible database for threat monitoring, risk mitigation, and post-incident investigation (if needed).
Security is critical in its own right, but it is also a central pillar of regulatory compliance.
Several widely applicable regulations explicitly call for some form of identity management, whether through user provisioning or other means. For example, the Payment Card Industry Data Security Standard (PCI DSS), which applies to most organizations that process credit card information, requires extensive IAM to protect cardholder data (CHD).
User provisioning streamlines compliance, making certifications easier to achieve.
Another major advantage felt primarily by users themselves is greater fluidity and ease of use across user accounts. Users spend less time logging in to their accounts, as well as less mental energy in creating and updating their lists of usernames, passwords, and other credentials.
Beyond the sheer number of passwords users have to manage, there is also the burden of repetitive password entry throughout a given workday. A recent study found that employees in the US enter passwords 12 times per day to access work systems—and 15 per day in Australia.
Making these processes easier removes stress and helps workers be as productive as possible.
User provisioning has the knock-on benefit of streamlining all IT processes with a unified source of truth across user accounts. This allows for greater visibility, transparency, and efficiency in all IT activities that involve personnel and account management, either directly or indirectly.
User provisioning challenges
Authentication and authorization management become difficult at scale as the volume and diversity of user accounts increase exponentially. The accuracy, consistency, and security of data are all paramount, which necessitates but also challenges a system like user provisioning.
One of the most pressing challenges to user provisioning and general account management at scale is the complicated regulatory context that comes with growth. Many regulations apply to sensitive data in a particular industry. And, even if an organization is not directly involved in that industry, it may need to meet its compliance requirements to take on clientele within it.
For example, the Health Insurance Portability and Accountability Act (HIPAA) applies directly to covered entities in healthcare, such as providers, plan administrators, and clearinghouses. But it also applies to these entities’ business associates, who in turn need to implement IAM and other controls to safeguard protected health information (PHI) across connected accounts.
Maintaining accurate and consistent user data across multiple systems is another significant challenge organizations face. Inaccurate or outdated user information can lead to security vulnerabilities, compliance risks, and operational inefficiencies.
Last but not least, managing user provisioning in large or rapidly growing organizations is challenging for several reasons:
Complexity of assigning unique resources to each user
The need for scalable systems to accommodate growth without losing efficiency
Varied access needs across different roles and departments
Demands of processing large batches of user accounts during events like company-wide onboarding, mergers, or acquisitions.
These factors pose significant logistical and technical obstacles.
User provisioning best practices
The difficulties detailed above make a careful approach to user provisioning especially important. Failing to implement it well can neutralize many of the benefits it provides.
Here are some ways to ensure user provisioning works to the best of its ability:
Standardized onboarding/offboarding: Ensuring all user accounts have uniform processes streamlines account creation, management, and deletion for all parties.
Automated user provisioning: Automating further streamlines processes, optimizes UX, and reduces the likelihood of costly errors.
Role-based access control (RBAC): Implementing RBAC further extends the utility of user provisioning by enabling seamless authorization across all connected platforms.
Regular reviews and adjustments: Reviewing accounts and governing configurations ensures all critical information and controls are up-to-date, secure, and compliant.
Strong overall authentication: Implementing strong auth controls elsewhere ensures inputs feeding into user provisioning systems are free from compromised information.
Getting a user provisioning system up and running is not in itself an automatic solution to all potential problems that can arise, but it’s an excellent start. One sure-fire way to make sure provisioning delivers on its promise is to implement it with powerful, efficient auth methods.
Seamless user provisioning with Descope
Efficient user provisioning is critical for maintaining security and operational fluidity within any organization.
Descope’s innovative approach to user provisioning, featuring automated SCIM provisioning and deprovisioning, simplifies and secures the user lifecycle management process. By offering customizable user models and the ability to enrich user data, you can adapt your system to meet unique requirements, ensuring compliance and good user experience.
Sign up for a Free Forever account with Descope and get SCIM-ready in minutes. Have questions about our platform? Book time with our auth experts.




