Table of Contents
What is session fixation?
With so many material and sensitive transactions taking place online, securing web applications and user access has never been more important. If users are tricked into misusing a web application without their knowledge, a session fixation attack can occur and the app’s security becomes compromised.
This guide takes a deep dive into what session fixation is, the primary causes of an attack, and how these types of attacks can be prevented.
What is session fixation?
Session fixation is a web-based cyberattack where the cybercriminal exploits the vulnerability of a web browser’s session management system to hijack a real user’s session. They do it so by tricking a web user into using a particular session identifier, or session ID.
To break it down, session IDs are how web applications authenticate users as they browse, storing the information in a cookie to be used for subsequent web requests. Essentially, session IDs enable users to remain logged in as they navigate through the website. However, improperly configured session IDs have their weaknesses and can provide attackers access to user accounts if compromised.
Session fixation happens when an attacker infiltrates a user’s web browser and tricks them into using a session ID that the attacker has access to. They start by accessing a web application login page, receive a generated session ID, and then get the victim to use and authenticate that provided session ID. This can happen through methods such as social engineering, which exploits human behavior in the form of scams and other tricks that get victims to click on malicious URLs.
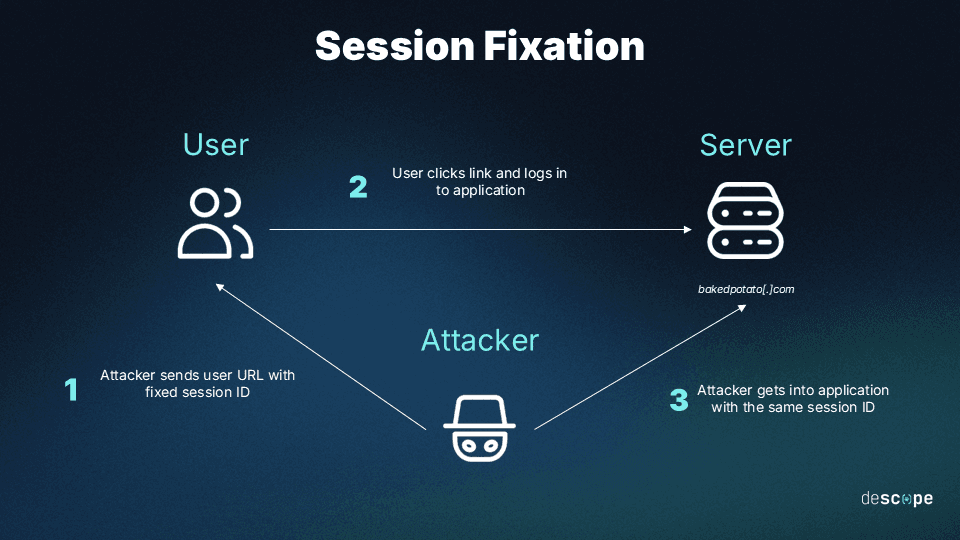
Once a victim uses the session ID, the attacker will be able to use it to access the user’s account and steal confidential data, make financial transactions, or complete full account takeover. This can put the system’s security at extreme risk, opening the door for more data breaches and cybersecurity attacks.
As an example, CVS experienced a medical data breach in 2021. It was found that their websites were using misconfigured databases, which allowed an attacker to steal healthcare data through a session fixation attack. Subsequent damage assessment found that more than a billion confidential search queries were potentially exposed, which includes data such as email addresses and prescriptions.
The risks associated with session fixation attacks cannot be understated—attackers use session fixation to weaken a company’s security posture and misuse sensitive information.
Session fixation vs. session hijacking
Both session fixation and session hijacking take advantage of improper session management and have a similar goal, which is to gain access to a session ID. However, they differ in the way that attackers achieve this end goal.
Session hijacking is when attackers steal an existing valid session ID by obtaining or guessing the session ID after the user has logged in. Usually, the attacker intercepts the session ID as it travels through insecure network, like unencrypted public Wi-Fi.
Session fixation, on the other hand, is a subset of hijacking where a predefined session ID is planted into a victim’s web browser, and once the user logs in to the web application, they’ll be using the same session ID the attacker already knows. The attacker can then replicate it to gain access at the same time or maintain access after the legitimate access ends.
How session fixation works
Attackers can fixate a user’s session ID using a few different techniques depending on the application. This includes MITM attacks, cross-site scripting (XSS), cross-site request forgery (CSRF), and even physical attacks.
MITM attacks: These attacks involve someone on the network intercepting communications between a user and a website in one of two ways: Address resolution protocol (ARP) poisoning or evil access points. ARP poisoning happens when an attacker sends an unsolicited reply to the target network device claiming that the attacker’s device is the gateway to the network. Evil access points are Wi-Fi access points that mimic a real access point nearby, such as airport Wi-Fi.
XSS attacks: Cross-site scripting vulnerabilities come from untrusted data that gets interpreted as code. This usually happens when HTML or JavaScript is generated, edited, or uploaded unsafely.
CSRF attacks: Cross-site request forgery forces a user to take actions on a web application in which they are authenticated, like changing their personal information, transferring funds, etc.
Physical attacks: A person who has physical access to a web browser can set specific cookies in a website before another user logs in to that same device.
The fundamental flaw exploited in session fixation is the web application's handling of session IDs. Specifically:
The application accepts externally provided session IDs without sufficient validation.
It does not regenerate a new session ID at the time of login or authentication, which is a critical step in securing session management.
Here’s a step-by-step overview of how a session fixation attack works:
Identifying a vulnerable application: The attacker identifies a target web application that is vulnerable to session fixation.
Obtaining or generating a session ID: The attacker either generates a new session ID by initiating a session with the target web application or uses a predetermined session ID that the application accepts.
Fixating the victim's session ID: The attacker tricks the victim into using the fixated session ID using one of the methods explained above.
Victim authentication: The victim logs in to the web application, unknowingly using the session ID chosen by the attacker.
Session hijacking: Since the attacker already knows the session ID, and now that it's been validated and associated with an authenticated session (i.e., the victim's logged-in session), the attacker can use the same session ID to access the web application as the victim.
How to prevent session fixation
The primary causes of session fixation attacks stem from insufficient web application security and unsafe session management practices. But as with any cybersecurity threat, developers can take certain measures to prevent session fixation attacks.
Preventing session fixation attacks starts with detecting vulnerabilities in web applications. These vulnerabilities include the aforementioned XSS and CSRF as well as other security gaps like weak credentials, broken access control, authentication failures, and security logging and monitoring issues.
There are several preventative measures and security best practices developers can undertake to mitigate the risk of these vulnerabilities and help avoid session fixation, including secure session management. Session management bridges the gap between web application interactions and the stateless nature of HTTP. It involves creating, maintaining, and terminating sessions to ensure the security of exchanged data during a session. Best practices for secure session management include:
Using secure, random session identifiers and assigning them long enough numerical values to prevent guessing the ID via compute.
Implementing HTTPS for every session to encrypt the data during transit.
Automatically checking for expired, invalid, or red-flag session IDs.
Enforcing session expiration to minimize the risk of an attacker exploiting an active session.
Regenerating session IDs after login to prevent session fixation attacks.
Implementing refresh token rotation and reuse detection.
Session management can also be secured by using token-based sessions, which leverage small, textual pieces of data (or tokens) to control user access across devices. A token is included in the authorization header of HTTP requests to authenticate sessions. Time limits and other security features can be built directly into the tokens.
Seamless and secure session management with Descope
Understanding and mitigating threats like session fixation is paramount for safeguarding user data and maintaining trust. The best way to prevent session fixation is to have proper session management practices set in place to secure your web applications.
If you prefer not to have your developers take care of session management on top of all their existing responsibilities, Descope can help. Our drag-and-drop CIAM platform helps customers “descope” session management from their daily work, while also providing secure and frictionless authentication experiences to their end users.
Sign up for a Free Forever account with Descope to streamline and secure your session management. Have questions about our platform? Book time with our auth experts.





