Table of Contents
What is RBAC?
Having a robust access control model is critical for every business. Unauthorized access can lead to data breaches and lack of legitimate access can harm the user experience. The solution (or at least one of them)? Role-based access control.
By tying access permissions to users’ specific roles, RBAC provides a secure, efficient way to safeguard sensitive information. In this article, we’ll explore what is RBAC, how it works, the concepts that underpin it, and the different models you can use to tailor access control to your needs.
What is RBAC?
RBAC—short for Role-Based Access Control—is a user authorization method that controls access to protected resources based on the user’s role within the organization. Instead of granting permissions directly to the users, the permissions are assigned to specific roles, and users are assigned to these roles.
This access control approach simplifies management and ensures that users have access only to the resources they need to perform their job duties. For example, in a hospital system:
A Doctor role might have permission to view and edit patient records.
A Nurse role might have permission to view records but not edit them.
A Receptionist role might have permission to schedule appointments but no access to medical records.
While RBAC is widely used today, the underlying technology and principles it is built on are half a century old. The National Institute of Standards and Technology (NIST) traces the history of RBAC back to the 1970s. The version we commonly use today originated in 1992 when computer scientists Ferraiolo and Kuhn introduced a model that was refined into an industry-wide standard by 2004.
Since then, RBAC has become one of the most common and effective access control methods, with no signs of slowing down. In fact, its market value was $10.83B in 2024 and is projected to grow to $24.3B by 2032.
How RBAC works
As the name suggests, the central concept in RBAC is the role. This aspect of the user profile ultimately determines the resources and the type of access they get. Roles may be tied to the person’s job title or position within a company or the functions and responsibilities. Example roles: Admin, Manager, Editor, Viewer.
Users can also hold multiple roles, which may be dynamic rather than static, such as temporary or seasonal roles that change over time. What makes the role most important in RBAC is its relationship to permissions.
Namely, the role defines what permissions the user has. Permissions refer to the ability to access and perform certain functions within the intended app or system. For example, a user may have permission to read certain documents but not edit them, or they might be able to edit a file but not view the complete edit history, delete it, or change its location. Access depends on their assigned permissions. Some common examples of permissions include Create, Read, Update, Delete (CRUD). A hypothetical set of roles could thus be:
Admin: Full CRUD permissions
Editor: Create and Update permissions
Viewer: Read-only permissions
In some RBAC deployments, roles define permissions, whereas in others, roles are seen as a set of permissions granted to a user. Regardless of the type of RBAC, roles and permissions together control user access. For example:
Alice (Manager) can approve budgets but cannot delete system configurations.
Bob (Viewer) can view reports but cannot modify them.
In summary, the key components of RBAC are:
Roles: Defined based on job functions (e.g., "Admin," "Manager," "Viewer").
Permissions: Specific actions or access rights assigned to roles (e.g., "Read," "Write," "Delete").
Users: Individuals assigned to one or more roles based on their responsibilities.
Rules: Policies dictating which roles have access to what resources.
Common types of RBAC
Just as three core concepts govern all RBAC (roles, permissions, and user access), there are three main types of RBAC into which the most common deployments fall:
Traditional: This is the most basic form of RBAC, serving as the foundation for other variations. Users are assigned roles that define their permissions. These roles are then authenticated before any actions are authorized.
Constrained: In these models, users have restricted capability to hold multiple roles and permissions simultaneously. This prevents users and potential attackers from performing potentially exploitable actions without authorization.
Hierarchical: These models categorize roles based on levels of access permissions. Higher-level roles (i.e., administrators) have greater access, whereas lower-level roles (i.e., guests) have fewer permissions that their superiors must grant.
Many deployments are hybrids that incorporate elements of constraint or hierarchy to some or all of the system, depending on adopters’ needs and risks.
Read more: Fine-Grained Authorization Explained & When to Use It
RBAC vs. other access control models
There are many versions and iterations of RBAC, not to mention access control in general. Other models that can be used instead of (or in addition to) RBAC include:
Relationship-based access control (ReBAC): A relatively newer approach, where the access permission depends on the relationship between the user and the resource. ReBAC is effective for creating authorization frameworks where hierarchies, nesting, and collaboration are required. Explore the difference between RBAC and ReBAC for more details.
Attribute-based access control (ABAC): Similar to RBAC, but authorizing decisions are based on individuals’ attributes, including but not limited to their role. Although highly customizable and accurate, ABAC can be resource-intensive. Explore the difference between RBAC and ABAC for more details.
Rule-based access control (RuBAC): The most customizable model available, where access decisions are based on any parameters deemed appropriate, including some external or unrelated to the user. This model is well-suited for settings with larger user bases.
Mandatory access control (MAC): Limits access based on the sensitivity of the data in question. Greater security means reduced overall accessibility and ease of use.
Discretionary access control (DAC): Typically allows users with granted access the authority to control others’ access. While it offers flexibility, security concerns can arise depending on the application or resource being accessed.
Compared to these other access control models, RBAC offers a happy medium of accessibility and security, which makes it an ideal fit for a wide range of B2B authentication use cases and adopter needs.
7 Benefits of RBAC
RBAC offers several clear benefits, with the most obvious one being security. Access control is one of the key pillars of cyber defense, ensuring that sensitive data is only accessible to authorized individuals and thus preventing data breaches.
Beyond being critical to keeping systems safe, RBAC is crucial for meeting regulatory compliance requirements. Many frameworks, such as HIPAA for healthcare data, the EU's GDPR for data protection, and PCI DSS for payment card information security, mandate stringent access control measures. RBAC addresses these requirements with straightforward and effective controls, keeping the organization compliant.
RBAC is also highly user-friendly when implemented correctly. From the user’s perspective, it seamlessly integrates with standard login and account management processes. Users' roles inherently manage access, allowing them to focus on their tasks without being burdened by security complexities.
For IT teams, RBAC significantly reduces workload. They no longer need to manually update individual user permissions, making processes like user onboarding and offboarding, adjusting permissions across different tenants, and upgrading access levels more streamlined and efficient.
Another advantage of RBAC is scalability. As organizations grow, adding new users or updating permissions is as simple as assigning roles, ensuring a seamless transition when roles or organizational structures evolve. However, organizations must guard against role explosion and avoid creating an excessive number of roles to handle nuanced use cases.
RBAC also promotes organizational transparency. By defining roles clearly, teams across departments can better understand who has access to what and why. This helps with audits and builds trust, as employees know their access is based on a structured, need-to-know basis rather than arbitrary assignments.
Finally, RBAC can lead to significant cost savings. By reducing the time IT teams spend on manual permission management and minimizing potential downtime from security incidents, organizations can reallocate resources to other priorities. This efficiency, combined with relatively manageable implementation times, makes RBAC one of the most cost-effective strategies for access control and account management.
How to implement RBAC
The specifics of RBAC implementation will vary based on the organizational environment and app architecture. That said, it usually breaks down into five steps:
Assess organizational needs: Determine if RBAC is suitable, and identify the specific type of RBAC that best aligns with your organization's needs.
Define roles and permissions: Clearly outline roles and permissions, including any hierarchies or dynamic elements relevant to your organization.
Create policies and procedures: Establish policies and procedures for role assignment and account management for a structured approach.
Map roles to users: Assign roles to users and provide training so they understand their permissions and responsibilities.
Test the system: Evaluate the system's effectiveness and security, and if it meets regulatory compliance standards.
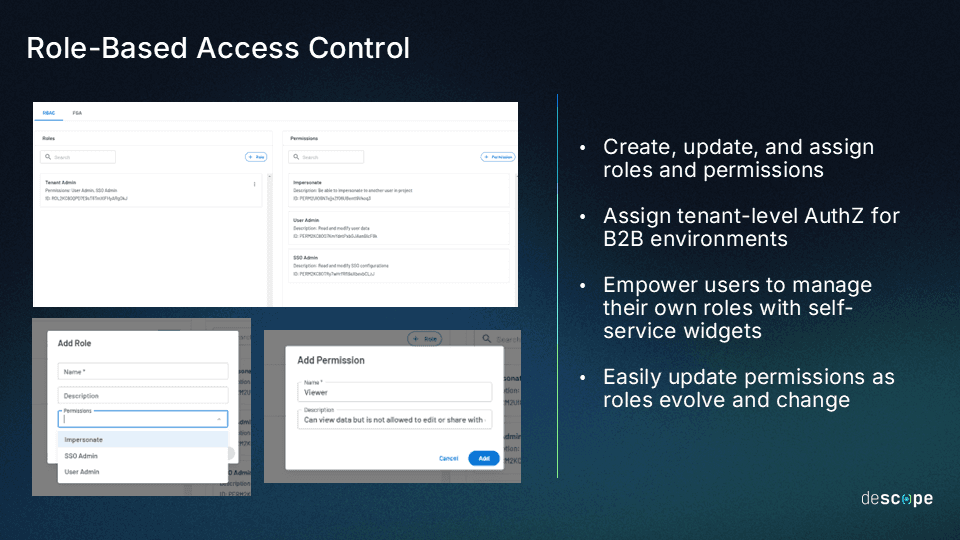
RBAC made easy with Descope
RBAC is pivotal for both security and efficiency, but implementing and scaling it in-house can quickly get complicated. Descope is a no-code CIAM platform that helps B2B app builders add tenant-aware RBAC (as well as ReBAC and ABAC) to their applications. Coupled with SSO, SCIM provisioning, tenant management, and MFA, this enables B2B app teams to delight their enterprise customers without spending unending developer cycles on in-house implementation.
Explore our RBAC documentation to learn more. Or if you’re ready to begin, sign up for a Free Forever account.