Table of Contents
What is fine-grained authorization (FGA)?
Protecting sensitive data requires more than broad, one-size-fits-all access control. Fine-grained authorization takes precision to the next level by granting permissions tailored to user roles, actions, and context. Whether it’s a healthcare provider accessing patient records or a financial analyst reviewing account details, this approach ensures the right people access the right information—no more, no less.
In this article, we will learn the basics of fine-grained authorization, how it differs from a coarse-grained approach, its pros and cons, and popular FGA use cases.
But before we get into fine-grained authorization, it’s important to know the following terms used in the context of identity and access management:
Authentication is the process of validating the identity of a user, machine, or other entity (i.e. are you who you say you are?).
Authorization is the process of granting or denying access to resources based on the permissions assigned to the authenticated user, machine, or entity.
Now, there are three main types of authorization:
Role-based access control (RBAC) governs access and actions based on the role assigned to the user.
Relationship-based access control (ReBAC) governs access and actions based on the relationships between entities (users, resources, organizations, etc.).
Attribute-based access control (ABAC) governs access and actions based on various attributes associated with the user (role, location, time, department, etc.).
You can learn more about authorization concepts in the video below.
What is fine-grained authorization (FGA)?
Fine-grained authorization—also called fine-grained access control (FGAC)—is an advanced approach of granting or restricting access to sensitive data and systems based on multiple conditions beyond just the user's role. For example, FGA can give users access to a resource only if they have a certain role in the IT department and are logging in within office hours.
Principle features of fine-grained authorization include:
ReBAC: Permissions are granted based on relationships between entities, which may or may not include roles (e.g. User A is able to view Document A but able to edit Document B).
ABAC: Permissions are granted based on attributes like user roles, resource type, actions, or environmental factors (e.g., location, time).
Granularity: Instead of broad access permissions (e.g., "read all files"), it allows highly specific rules, such as "edit documents in Project A during business hours if user belongs to the Marketing department."
Dynamic: Fine-grained authorization often uses real-time evaluations of rules and policies to dynamically respond to changing conditions.
Policy-driven: Policies are defined explicitly using languages like XACML (eXtensible Access Control Markup Language) or implemented within frameworks, ensuring clear and enforceable rules.
FGA is a recommended authorization approach for organizations that need robust but flexible access control, especially in highly regulated industries or environments with sensitive data.
Learn the differences between RBAC vs ReBAC and RBAC vs. ABAC
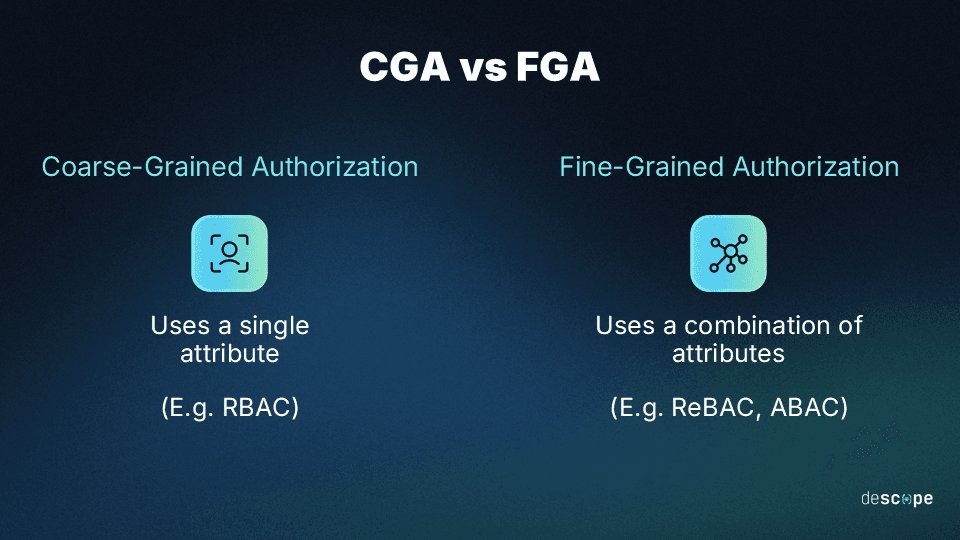
Coarse- vs fine-grained authorization
To understand fine-grained authorization better, we need to compare it to its counterpart: Coarse-grained authorization.
While both approaches work to control user access, they differ in their implementation.
Coarse-grained authorization grants or restricts access to resources based on a single attribute. This approach often defines access control at a broader level and is relatively simpler to set up and maintain.
Fine-grained authorization, on the other hand, relies on multiple attributes to govern user access. This leads to more granular authorization (hence the name) but also more time and effort spent.
RBAC is a common example of coarse-grained authorization since only user roles define their access permissions. While coarse-grained access control is an effective approach for simple systems, scaling it can lead to role explosion, leaving developers and admins with more roles to manage than they can handle.
ReBAC and ABAC are common examples of fine-grained authorization since various attributes and the relationships between them can be used to govern access. FGA is a good approach for complex organizations or systems and is more scalable without role explosion.
Learn more: Coarse-Grained vs Fine-Grained Authorization: Which to Use?
Pros and cons of fine-grained authorization
Fine-grained authorization is a powerful tool for certain scenarios, but it also has some potential tradeoffs that organizations should consider.
FGA pros
Granular control: By considering multiple attributes before making access decisions, organizations can define flexible and granular permissions.
Better security: By implementing tight access control rather than just basing it on roles, organizations can reduce the likelihood of data breaches and the “blast radius” of any unauthorized access that does occur.
Dynamic: Since FGA includes multiple attributes, a user’s access can change dynamically if their role or relationship to a resource changes.
FGA cons
Complexity: Implementing FGA properly is likely to require considerable time and effort. Admins will have to create and manage a large number of rules and attributes.
Auditing challenges: Monitoring logs for a variety of stakeholders and attributes can be a time-consuming and error-prone process.
Increased compute resources: The more roles, relationships, and attributes that form an FGA model, the more processing time and power they require to run in a reliable and performant manner.
Common use cases of fine-grained authorization
Now that we have covered the basics of FGA, the next logical question is when organizations should use this approach. While each app is different, here are some traits to consider before deciding if FGA is the right approach:
When your IAM systems are dealing with a variety of stakeholders (employees, customers, partners, contractors), FGA is a practical authorization approach. Using just roles, in this case, would lead to role explosion, but FGA can offer the right level of granularity to provide different types of users the access they require.
When you need to add self-serve user sharing on your app’s resources, FGA is the obvious choice. With FGA implemented, users can share resources with other users and assign different levels of permissions themselves (based on the options the app developers make available).
When your user base's structure contains many hierarchies and groups, FGA is the most scalable option available. By putting users in groups and departments (e.g. for a B2B SaaS app), permissions can be defined en masse to resources rather than on a per-user basis.
Implement fine-grained authorization with Descope
Fine-grained authorization is a powerful way for developers and IT admins to add flexible, granular access control to their apps. However, creating FGA functionality in-house can get complicated quickly, distracting developers from core product initiatives and leaving the door open for security gaps and vulnerabilities.
Descope can help. Our no / low code CIAM platform helps organizations easily add fine-grained authorization (RBAC, ReBAC, ABAC) to their apps using SDKs and APIs. Check out the docs for our authorization service and watch this demo video to learn more.
To get started with Descope, sign up for a Free Forever account and join the AuthTown community for any questions or feedback. Have more fine-grained authorization questions? Book time with our auth experts.






