Table of Contents
What are access tokens?
In recent years, the term “access token” has emerged as a cornerstone in the architecture of secure online interactions. Much like how JWTs have revolutionized authentication and authorization, access tokens are now instrumental in determining access in the digital sphere.
In this article, we'll delve into the fundamentals of access tokens, shedding light on their mechanics and the benefits they offer in contemporary web security and user verification processes. Whether you're deep in the trenches of web development or simply keen to understand the magic behind your secure online sessions, we hope you enjoy this exploration into the world of tokens.
What are access tokens?
An access token is a compact digital artifact, typically in the form of a JSON Web Token (JWT), that grants permissions to a user (the resource owner) to access certain resources. These tokens act as an electronic key, ensuring that the user has the correct permissions to access the data they are requesting.
In the simplest terms, an access token is a credential that can be provided as proof of authorization. Once a user logs in to a system, rather than constantly checking their username and password (or hopefully conducting some other passwordless method of authentication) for each subsequent request, the system provides them with an access token. This serves as a "key," granting the user access to specific resources without needing to re-enter their credentials.
Below is an example:
{
"amr": [
"oauth"
],
"drn": "DS",
"exp": 1698175401,
"iat": 1698174801,
"iss": "P2SAc2Ou4l9d5GlpYWyUZRYtNHM6",
"rexp": "2023-11-21T19:13:21Z",
"sub": "U2XDs389PTVB8xtfRlixPb4luUD7"
}Let’s quickly go over what this JWT means:
The `amr` field tells us how the token was created, in this case being with the OAuth authentication method.
`exp` provides the expiration time.
`iat` specifies when it was created.
`iss` functions as a signature, telling us the entity that issued it.
`sub` identifies the intended recipient, whether a user or another entity.
Access tokens vs refresh tokens vs ID tokens
Before delving further into access tokens, it's crucial to distinguish them from refresh tokens and ID tokens. While all three types of tokens are used in authentication and authorization processes, they serve different purposes:
Access tokens: As mentioned, these tokens allow users access to certain resources. They often have a short lifespan (typically ranging from minutes to hours) to ensure security. Once expired, the user cannot access the resources until they obtain a new token.
Refresh tokens: These tokens have a longer lifespan and are used to obtain new access tokens once the original ones expire. By using a refresh token, users don't have to re-enter their credentials, ensuring a smooth user experience.
ID tokens: ID tokens are used to confirm that a user has been authenticated. Typically used in the context of OpenID Connect, the ID token is passed from the OIDC provider to the application as proof of successful authentication.
Why are access tokens important?
Here are some benefits of using access tokens:
Improved security: Access tokens have a limited lifespan, curbing the damage an attacker can cause even if they successfully steal a token.
Scalability: Access tokens allow systems to authenticate requests without repeatedly hitting the main authentication server or database. This reduces the load on such systems, leading to better scalability and performance.
Fine-grained access control: Access tokens can encode specific permissions (or scopes), enabling systems to allow or deny operations based on the token's content. This way, users only access resources they're permitted to access.
Better user experience: With access tokens, once a user logs in, they can enjoy a seamless experience without constant interruptions for re-authentication.
How do access tokens work?
Access tokens are commonly used in OAuth 2.0, a popular authorization framework. Here's a simplified flow of how it works:
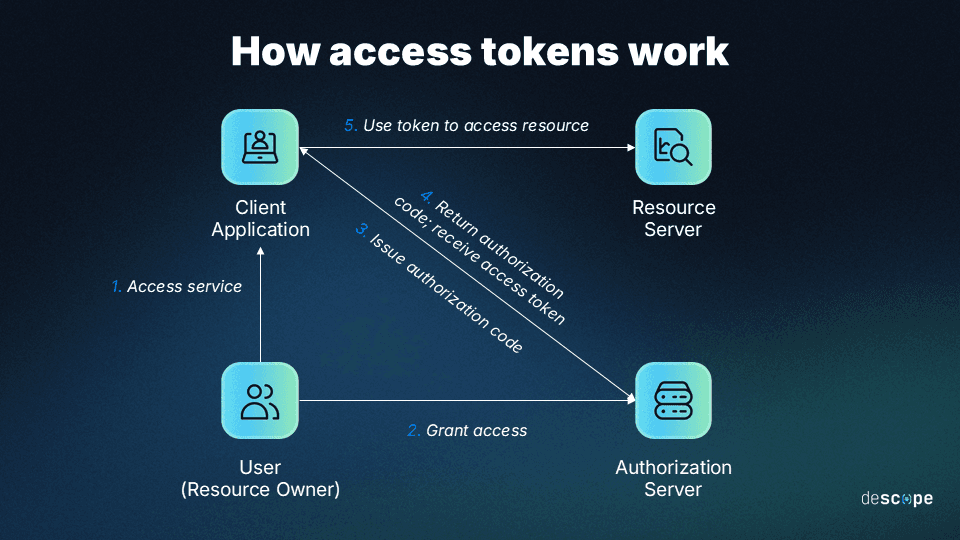
Authorization request: The client (like a mobile app) requests authorization from the user to access specific resources.
Granting authorization: If the user grants permission, an authorization code is sent to the client.
Requesting token: Using this authorization code, the client then requests an access token from the authorization server.
Issuing token: Upon validating the client's request, the authorization server issues an access token (and optionally, a refresh token).
Accessing resources: The client can now use this access token to request resources from the resource server. The resource server will validate the token and, if valid, grant access to the requested resources.
Best practices for using access tokens
Access tokens can improve user experience and security when implemented thoughtfully. Here are some tips on how to use them in an optimal way:
Use HTTPS: Always transmit access tokens over HTTPS to prevent interception by malicious parties.
Short lifespans: To minimize potential damage from leaks, ensure your access tokens have a short lifespan. Take the nature of your app into account while determining lifespans. Sensitive operations (e.g. banking, healthcare) should especially have short lifespans.
Handle breaches: Implement mechanisms to quickly detect, revoke, and reissue tokens if you suspect a breach.
Storage: Store tokens securely, especially on client-side applications. For instance, in web applications, consider using HTTP-only cookies or Web Cryptography API for secure storage.
Avoid overly broad scopes: When issuing tokens, be specific about their permissions to limit potential misuse. Issuing very broad scopes can have serious ramifications if an attacker gets hold of an access token – they can establish persistence in your systems and cause damage even after it has expired.
Conclusion
Access tokens, especially when implemented as JWTs, have undoubtedly simplified the process of authentication and authorization in today's digital age. When implemented correctly, they offer a secure, efficient, and scalable method for resource access.
If you’re looking to simplify access token management for your app, Descope can help. Our no-code CIAM platform helps developers easily add authentication, authorization, and identity management to their apps using drag-and-drop workflows.
Create a Free Forever account to start using Descope today. Have questions about our platform? Book time with our auth experts.




