Table of Contents
What is Client-Initiated Backchannel Authentication (CIBA)?
Client-Initiated Backchannel Authentication (CIBA) is a decoupled authentication flow that separates the device where a client application runs (the “consumption device) from the device where the user authenticates (the “authentication device”). Unlike typical OAuth and OpenID Connect (OIDC) flows that use browser redirects, CIBA enables direct backchannel communication between the client and the OpenID provider.
Using CIBA, authentication can be initiated by the client application without requiring user interaction on that same device. The authentication happens out of band on a separate device, usually the user’s smartphone. Decoupling the two devices creates flexible yet secure authentication options, particularly for out-of-band scenarios.
Main points
What is CIBA? A decoupled flow that allows clients (e.g., apps) to initiate authentication without user interaction on the consumption device (where the client application runs).
How CIBA works: The client sends a request to the OIDC provider, which then authenticates the user on their separate device.
Security and benefits: A financial-grade protocol, CIBA offers phishing-resistant defense against fraud while eliminating the need to share sensitive information.
What is Client-Initiated Backchannel Authentication (CIBA)?
Client-Initiated Backchannel Authentication is a decoupled authentication flow that separates the device where a client application runs (the “consumption device) from the device where the user authenticates (the “authentication device”). Unlike typical OAuth and OpenID Connect (OIDC) flows that use browser redirects, CIBA enables direct backchannel communication between the client and the OpenID provider.
This approach allows authentication to take place on a trusted, separate device (usually the user’s smartphone), making it ideal for out-of-band scenarios like call centers or kiosks. The result is a more flexible, secure experience that doesn’t rely on the browser.
Read more: OpenID vs OAuth: Understanding the Difference
Core components of CIBA
Client-Initiated Backchannel Authentication consists of many key elements that work together to create a decoupled authentication flow. Because CIBA relies on the OIDC and OAuth 2.0 protocols, many of its constituent components require a working understanding of those frameworks.
CIBA concepts from OIDC and OAuth
Tokens: ID tokens, access tokens, and (optionally) refresh tokens are an essential part of the CIBA flow.
Grant type: CIBA uses an extension grant type, which essentially adds support for non-standard scenarios.
Scopes: Mechanism that limits an application’s access to resources and actions. Apps must request at least one scope, and the access token it receives is limited to the scopes granted.
CIBA endpoints
Backchannel authentication endpoint: The server endpoint where clients directly send authentication requests. This is where CIBA begins, without any browser redirection.
Client notification endpoint: An endpoint the client registers for receiving notifications from the OIDC provider when using the ping or push delivery modes.
Three token delivery modes
CIBA implementations can use one of the following token delivery modes at a time:
Poll mode: The client checks the token endpoint at predefined intervals to see if authentication is complete.
Ping mode: The OIDC provider notifies the client when authentication is ready, then the client retrieves the tokens.
Push mode: The OIDC provider delivers tokens directly to the client notification endpoint.
User identifiers
CIBA requires the client to provide one (and only one) of three possible identifiers:
login_hint: A simple identifier like email, username, phone number, etc.login_hint_token: A deployment-specific token format with custom user identifiers.id_token_hint: A previously issued ID token from the OIDC provider.
Binding message
A binding message is an optional, human-readable identifier displayed on both devices to help users verify they’re approving the correct request. The message typically includes a unique code that differentiates this request from any others. This helps combat prompt or MFA bombing, which attempts to confuse users with illegitimate authentication requests.
Consumption device & authentication device
The separate devices involved in a CIBA flow are known as the consumption device and the authentication device. Because CIBA decouples authentication from the device requesting authentication (the consumption device), the authentication device is needed to confirm the user’s identity.
CIBA flow example: authenticating with a call center agent
In a typical call center scenario, organizations must verify a caller’s identity before discussing sensitive information. CIBA streamlines this process by enabling secure, out-of-band authentication, even when the caller and agent are using different devices.
Here’s how a CIBA flow works using the poll token delivery mode:
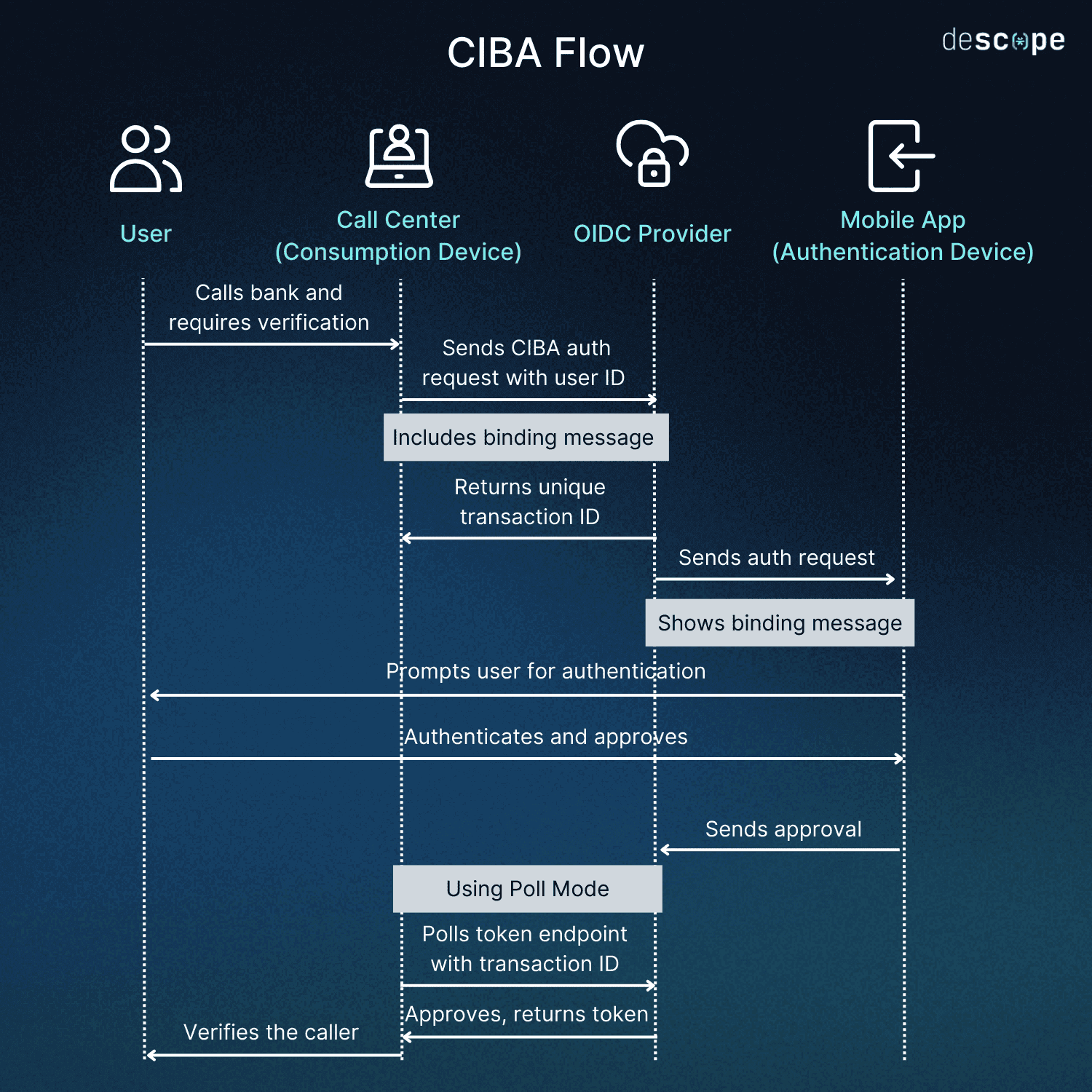
Initiation: The call center agent (using the consumption device) triggers a CIBA flow by sending an authentication request to the OIDC provider, including the caller’s identifier (e.g., phone number) and a binding message such as “Call Center Login.”
Acknowledgement: The OIDC provider immediately returns a unique transaction ID to the call center, acknowledging the request.
User notification: A notification is sent to the caller’s registered mobile banking app on their smartphone.
Prompt: The app may display a prompt with the binding message to help the user verify the context.
Authentication: The caller approves the request using biometrics or a PIN on their mobile device.
Approval: The mobile app sends the approval code to the OIDC provider.
Token retrieval: The call center periodically polls the token endpoint using the transaction ID.
Token delivery: When authentication is complete, the OIDC provider returns the tokens to the call center system in response to a poll request.
Verification complete: The call can proceed now that the caller has been authenticated.
This example illustrates poll mode, which is one of the three possible token delivery options in CIBA. The client and provider would select a single mode during implementation (poll, ping, or push) based on their specific requirements.
This example illustrates poll mode, which is one of the three possible token delivery options in CIBA. The client and provider would select a single mode during implementation (poll, ping, or push) based on their specific requirements.
Client-Initiated Backchannel Authentication in real-world scenarios
CIBA offers significant advantages over traditional authentication methods, especially in circumstances where user interaction is hampered by device limitations or out-of-band environments. Below are several examples of common CIBA implementations, noting how the specification offers better security and user experience:
Point of Sale (PoS) authentication
Automation in retail is increasingly popular as companies look for ways to reduce staffing overhead. Self-service terminals capable of initiating CIBA flows allow customers to pick up items from a brick-and-mortar store without having to flag down an associate.
For example, a customer who selected the “pick up in store” option arrives at the location and interacts with a PoS terminal. After entering a code or selecting their order, the terminal initiates a CIBA request. The user receives a push notification on their registered smartphone, authenticates via a mobile app, and the terminal unlocks the container to complete the purchase.
Read more: Cybersecurity in Retail: Key Threats & Defense Mechanisms
Call center authentication
Imagine a customer has called your support team and needs to verify their identity before proceeding. Security questions are notoriously fallible (and risky to communicate to a potential fraudster), and “sending a one-time code” for the caller to speak aloud is a well-known phishing technique. Understandably, users are reluctant to share personal information over the phone, but CIBA can solve this anxiety.
The call center agent can authenticate the caller by sending a push notification to their mobile banking app, where they verify their identity with on-device biometrics. This approach provides both a stronger security posture and better privacy, because sensitive information remains unsaid.
Read more: Customer IAM in Banking: Considerations & Best Practices
Face-to-face authentication
Whether it’s a bank teller, pharmacy tech, or a doctor’s office that needs additional verification, CIBA turns in-person authentication into a quick and painless process. A passport or driver’s license is often seen as the ultimate form of ID, but documents can be copied or stolen, and employees can be socially engineered. Not so with CIBA.
CIBA’s decoupled authentication goes straight to the user’s most reliable possession factor: their smartphone. Because a customer’s identity is already confirmed on their device, and the process can leverage inherence factors like fingerprints and facial recognition, CIBA constitutes a highly reliable, financial-grade protocol for verification.
AI agent authentication
When an AI agent needs to make a transaction or access sensitive data on behalf of a user, CIBA provides the authentication backdrop necessary for “human-in-the-loop” approval without disrupting the agent’s workflow. Because authentication can take place asynchronously, the agent can carry on with other tasks rather than waiting for the user.
Read more: What Is the A2A (Agent2Agent) Protocol and How It Works
CIBA for agentic AI
As AI agents become more capable of acting on behalf of their users, traditional authentication modalities pose significant security risks. CIBA strikes a balance between security and user experience, offering a compelling “human-in-the-loop” mechanism for the emerging agentic AI ecosystem.
No credential sharing
With CIBA, users never need to share passwords with AI agents, eliminating a massive security risk. The authentication secrets remain on a user’s device and are never exposed during the process.
For example, if the AI agent is presented as an LLM (Large Language Model) via a chat interface, traditional methods would force a redirect for authentication, potentially having to enter their credentials or re-authenticate. With CIBA, the user can simply tap their smartphone and proceed.
Human approval/oversight
AI agents will eventually be quite clever, but for the short term, they can’t be left to their own devices. For example, at the time of this writing, Claude Desktop in Computer Use mode could land on a website with a hidden prompt injection and be directed to take malicious action against the user. “Human-in-the-loop” refers to a security concept for agentic AI and tooling that recommends human approval for sensitive actions, like making a purchase, accessing sensitive information, or sending a Slack message to everyone in your organization.
Clear binding messages
In addition to looping in a human for approval, CIBA’s binding messages keep users apprised of their agent’s activity. Clear binding messages ensure that, if an agent wants to do something requiring extra authentication, you know exactly what it’s for.
In the not-too-distant future, a customer might tell their AI assistant, “Buy me a new pair of shoes,” and moments later receive a prompt with two options. After selecting one, they’re presented with a CIBA flow: a binding message explaining the transaction and requesting authentication.
Reliance on proven standards
Rather than reinventing the wheel for agentic AI authentication, CIBA leverages established protocols that have been tested and validated over years of refinement. The underlying mechanisms of CIBA not only enable asynchronous workflows—meaning the AI agent can continue with other tasks while waiting for authentication—but they also ensure a high level of phishing-resistant security.
While some organizations have proposed new authentication protocols specifically for AI tooling and agents, the rationale is questionable: are AI agents really so different as digital denizens that we require a novel framework? No, say most identity providers, as they look to existing standards.
CIBA’s future as an out-of-band authenticator
As AI agents become more integrated into our daily lives, the need for secure delegation mechanisms will only grow more intense. CIBA is in a unique position to become the new standard for human-in-the-loop design philosophy within AI systems. Because it neatly balances rigorous security with usability, CIBA has already seen adoption across the financial sector, one of the most demanding industries when it comes to protecting user data and privacy.
For now, the specification remains a mostly scenario-specific method when other options fail; however, the incoming deluge of agentic AI apps is likely to turn the tide in favor of CIBA over most alternatives. The fact that financial institutions trust it with high-value transactions will certainly contribute to its perception. As AI agents begin handling more sensitive tasks across industries, CIBA’s proven approach to secure delegation is bound to see broader implementation.
Stay ahead of the curve
As agentic AI continues to evolve, so does the need for secure, user-approved delegation. Client-Initiated Backchannel Authentication offers a strong foundation for managing these out-of-band authentication flows, balancing flexibility with phishing-resistant security.
For organizations exploring this next frontier, Descope’s Agentic Identity Hub brings these ideas to life with infrastructure built for human-in-the-loop AI.





