Table of Contents
Common broken authentication attacks
If authentication is the process of verifying the identity of a user or entity requesting access to a system or application, broken authentication occurs when an attacker exploits a vulnerability in this process to gain unauthorized access. Session and credentials (username and password) management are the two most common aspects that are exploited by attackers to break authentication.
Broken authentication and session management
A session is an interaction between a user and an application. A new session starts when a user logs in to the application, creating a unique session ID. When the user logs out of the application or remains inactive for some time, the session automatically ends.
The security of a session depends on the unique session ID, which is a signifier that the user is authenticated. Poor session management can result in broken authentication attacks, where the attacker gains access to user accounts and sensitive data.
Impact of broken authentication
A successful broken authentication attack can provide cybercriminals with access to:
Sensitive personally identifiable information (PII) for members of an organization
Confidential and proprietary information
Administrative account passwords and access privileges
Financial data and access to bank accounts
The potential impact on an organization can be significant, depending on the type of account compromised or the extent of the broken authentication attack.
Common broken authentication attacks
Considering the vast majority of broken authentication vulnerabilities and their prevalence across business applications, cybercriminals tend to exploit them at every possible opportunity.
Examples of broken authentication attacks include:
Brute force attack
When deploying a brute force attack, an attacker repeatedly attempts to bypass an application’s access controls by guessing the required credentials. If the initial attack is successful, the attacker can then deploy secondary attacks, such as account takeover and credential stuffing.
To increase their chances of success with deciphering account credentials, cybercriminals use automated tools such as botnets to conduct brute force attacks.
Cybercriminals deploy simple brute force attacks based on the assumption that application users implement simple, easy-to-guess passwords like “Password1234” across their accounts. However, for more complicated variants like rainbow table attacks, they use advanced algorithms to bypass security.
Credential stuffing
Credential stuffing is another common example of a broken authentication attack. It occurs when cybercriminals obtain login credentials through data breaches and then use these same login and password combinations to access unrelated accounts at separate services or organizations. This is possible because many people reuse the same password across different services.
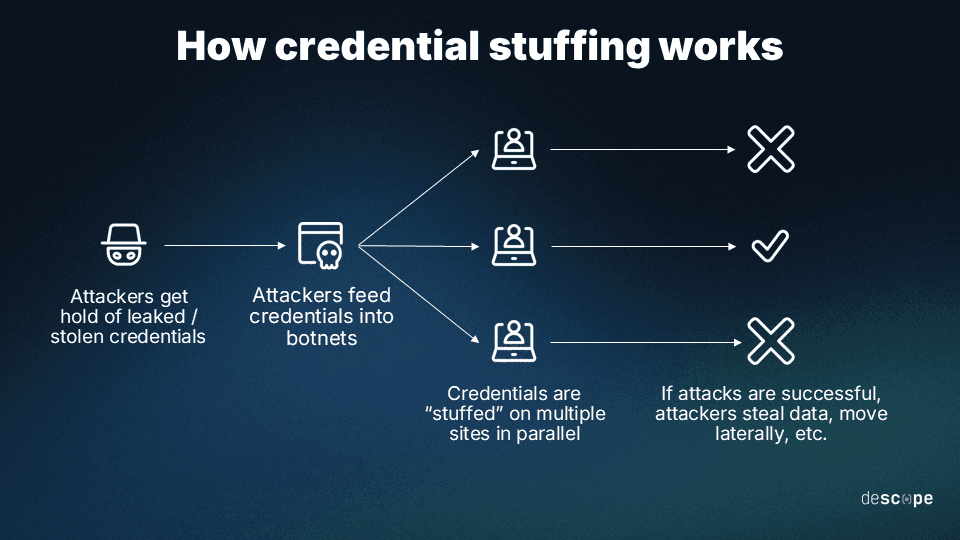
Like brute force attacks, credential stuffing also leverages botnets to automate and increase the odds of success when plugging random passwords to bypass access controls.
Session hijacking
Session hijacking is a type of attack where an attacker takes over a valid user's session. Depending on the level of access the user has, the attacker can steal users’ identities, perform actions on their behalf, initiate transactions, etc.
Examples of session hijacking attacks include:
Session sniffing – Here, an attacker will use a sniffer to “sniff” around networks to identify exploitable vulnerabilities, like non-SSL/TLS-encrypted applications.
Cross-site scripting (XSS) – An attacker can also exploit web application vulnerabilities to inject malicious scripts in email or website links. Upon clicking these links, a user unknowingly grants the attacker control of an otherwise protected web session.
A recent example of session stealing happened at CircleCI. Attackers infected an engineer’s laptop with malware to steal their 2FA-backed session cookie and used it to impersonate the employee from a remote location.
Phishing
Phishing is a type of social engineering attack where the attacker deceives an individual into revealing sensitive data. Since these attacks are socially engineered, victims are often clueless about when, how, or why the attack is happening.
Phishing attacks can take many forms, but some common examples include:
Emails that appear to be from a well-known company, such as a bank or e-commerce site, requesting the recipient to update their account information or confirm a recent transaction.
Messages that appear to be from a trusted person, such as a colleague or friend, requesting the recipient to click on a link or open an attachment.
Fake login pages that mimic a legitimate website to trick the user into entering their login credentials.
Most phishing attacks tend to appeal to victims’ emotions with a sense of urgency, eliciting excitement, confusion, or anguish that causes the victim to act impulsively.
Password spraying
Unlike brute force attacks, where cybercriminals try multiple passwords to access a single account, password spraying uses a single password across different accounts. This technique helps attackers stay undetected by security systems that lock out an account after too many failed login attempts.
Cybercriminals often use password spraying to target new accounts with common or weak passwords.
How to protect your business against broken authentication attacks
Considering the breadth and complexity of broken authentication attacks, how can you protect your business against them?
The most effective approach to mitigating broken authentication attacks involves multiple preventive steps:
Passwordless authentication
Many broken authentication attacks stem from the use of passwords as an authentication factor. Organizations should adopt passwordless authentication methods such as magic links, biometrics, social logins, and authenticator apps for their online services.
While the specifics of the aforementioned methods vary, one thing they all have in common is that they are more secure and more convenient for end users than passwords.
Multi-factor authentication
Gone are the days when users logged in to applications using a single form of authentication, such as a password.
To mitigate the risks of broken authentication, businesses must implement layered security i.e., multi-factor authentication (MFA). With MFA, users are required to provide two or more pieces of information to verify their identity before they can access their accounts.
Enforce strong passwords
Simple, easy-to-remember passwords like Password123 are easily exploitable and present serious broken authentication vulnerabilities.
While passwordless authentication is the ideal end state, passwords (if and when they are used) must meet applicable standards for minimum length and character variety. A longer and more complex password is at a much lower risk of being compromised during a brute force or password spraying attack than a shorter and predictably common one.
Password hashing
Hashing is a form of password protection in which a one-way function converts a plaintext password into a non-reversible and unique string of characters. The hashed password is then stored in a database rather than the plaintext password. So even with access to the database, it’s difficult for the attacker to use the passwords to cause compromise.
When combined with other techniques, like salting, password hashing makes it extremely difficult for cybercriminals to crack the credentials, making it one of the most effective protective measures.
Breached password detection
Adding tools like breached password detectors to your arsenal will help you protect your business from broken authentication. These tools track the account data that’s been reported compromised or stolen by major breaches, and effectively recognize when an attacker attempts to log in to an account using these credentials.
Upon recognition of credential stuffing, the breached password detector can notify users that their access credentials have been compromised. The users can then change their passwords immediately or modify their existing MFA controls.
Brute force protection
Your business can protect itself from brute force attacks by locking out an account as soon as multiple login attempts are registered to that same account. However, this is typically effective for a limited duration, say 30 minutes to an hour. And these brute force attacks can occur across multiple accounts, which could result in many users being locked out.
A more effective way to implement brute force protection is to block IP addresses detected as the source of multiple login attempts, whether at a single account or several of them.
Regulate session length
Another common way businesses protect themselves from broken authentication is by limiting session length to a set time. Predefined session lengths reduce the risk of attacks like session hijacking.
Businesses that process highly sensitive data, such as banks and airlines, typically use this safeguard to automatically log out users when time runs out during idle sessions.
Remove session IDs in the URL
Since session IDs are unique identifiers, they should not be left in easily accessible locations like website URLs. By leaving them in URLs, your business increases the risk of these IDs being compromised and rewritten to regain access to a user session.
Rotate and invalidate session IDs
Upon completing a session, a user must be logged out. The session ID must also be invalidated on the client and server sides, so it cannot be reused.
Fortify your application with seamless authentication
If you’re looking for a secure and easy-to-use authentication solution to protect your business from broken authentication attacks, Descope can help. Our drag-and-drop workflows enable you to build secure and frictionless authentication flows with a few lines of code.
Sign up for Descope and unburden yourself from authentication security responsibilities.






