Table of Contents
What is an authenticator app?
In today's digital age, protecting your customers’ online accounts has become more important than ever. With the rise of cyber threats such as phishing, ransomware, and identity theft, securing users’ online presence is crucial. Using an authenticator app is one of the most effective ways to do so.
This article will explore what an authenticator app is, how it works, and its benefits and drawbacks.
What is an authenticator app?
An authenticator app is a mobile or computer application that generates time-based one-time passwords (TOTP) for the purpose of multi-factor user authentication or sometimes step-up authentication. It provides an additional layer of security by requiring users to enter a generated code to verify their identities.
Authenticator apps have become popular in recent years due to their improved security and low costs. They share benefits with other passwordless authentication methods in this regard.
Google Authenticator, Microsoft Authenticator, and Authy are some examples of popular authenticator apps.
How authenticator apps work
Authenticator apps work by synchronizing a shared secret between the app and the server. This code is based on the current time and the shared secret.
The app generates a TOTP code within set intervals of time. The time frame is usually between 30 and 90 seconds. The server compares the code entered by the user to the code generated by the app. If they are the same, the user is allowed to access their account.

Here’s a step-by-step overview of how these apps work:
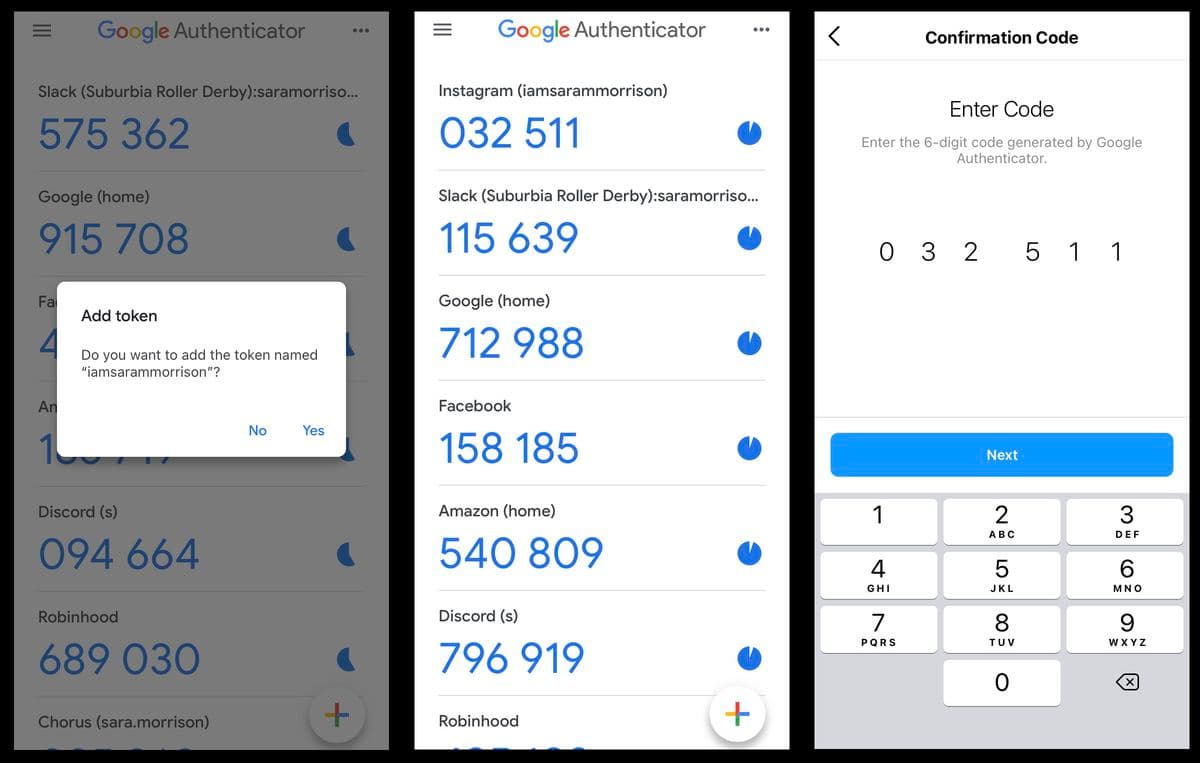
Setup: During the initial setup process, the user associates their account with the authenticator app. This is done by scanning a QR code or manually entering a secret key provided by the application. The secret key is securely exchanged between the app and the server.
Shared Secret: The app stores the shared secret securely on the user's device. This secret is unique to the user and the specific account being protected.
Code Generation: The app continuously generates time-based codes using the shared secret and a TOTP algorithm. The codes are typically six or eight digits long.
Code Presentation: The user can open the app and view the current code associated with their account. The code updates at regular intervals to ensure uniqueness and security.
Verification: When the user attempts to log in, they are prompted to enter the current code displayed in their app.
Code Validation: The server receiving the authentication request retrieves the shared secret associated with the user's account. It uses the same algorithm as the app to generate a code independently.
Code Matching: The server compares the code entered by the user with the code it generated based on the shared secret. If the codes match, authentication is successful, and the user is granted access to their account.
Code Expiration: As the code generated by the authenticator app has a limited validity period, it becomes invalid after that time window. The user will need to generate and enter a new code for subsequent login attempts.
Benefits of authenticator apps
Here are four key benefits of using an authenticator app:
Increases security: Even if an attacker manages to steal a username and password, they won't be able to log in to the user account without the app-generated verification code. This reduces the risk of account breaches, account takeover fraud, and broken authentication.
Works offline: Authenticator apps work even when users are offline, which makes them ideal for use when traveling or in areas with poor Internet connectivity.
Improves user experience: They offer a convenient and user-friendly method of 2-step verification. These authentication codes are readily accessible on their mobile devices, removing the need for external devices or services.
Strengthens brand identity: Authenticator app interfaces can be customized to reflect the branding of the app or organization using them.
Drawbacks of authenticator apps
While authenticator apps provide significant benefits, they also have some drawbacks. Here are a few to consider:
Device dependency: If a user loses their device, or it malfunctions, they lose access to their authenticator app. They may need to go through a lengthy account recovery process as some auth apps do not offer backup codes.
Limited availability: Authenticator apps may not be universally supported by all platforms or services.
When to use an authenticator app?
Developers and businesses should consider using authenticator apps as an additional security layer when they want to enhance user protection.
Here are some scenarios where authenticator apps can be beneficial:
High-security applications: If an application or service handles sensitive user data or involves financial transactions, using an authenticator app for stronger security is highly recommended.
Remote work: For applications that provide remote access to corporate networks, authenticator apps can ensure that only authorized users can connect to the network.
Cloud-based services: Businesses that utilize cloud-based services, such as cloud storage or collaboration platforms, can implement authenticator apps to secure user accounts accessing those services.
Customer account protection: If your application involves user accounts that contain personal information or user-generated content, using an authenticator app can help protect those accounts from unauthorized access.
That said, authenticator apps can be beneficial for a wide range of industries where account security is crucial:
Banking and finance
Healthcare
E-commerce
Cloud services and SaaS
Enterprise and corporate networks
Social media
Government and public sector
Gaming and entertainment
While these industries can benefit significantly from authenticator apps, it's important to assess the specific security needs and compliance requirements of each organization to determine the most suitable security measures.
Sounds too complex? Descope makes it easy
While the benefits of using an authenticator app are clear, some organizations may find adding TOTP authentication to their app complex or intimidating. That's where Descope comes in.
Descope helps developers easily add TOTP authentication to their products using drag-and-drop workflows, SDKs, and APIs. Our platform abstracts away the complexity of authentication – while also making it frictionless and secure – so that app builders can spend more time on core product initiatives.
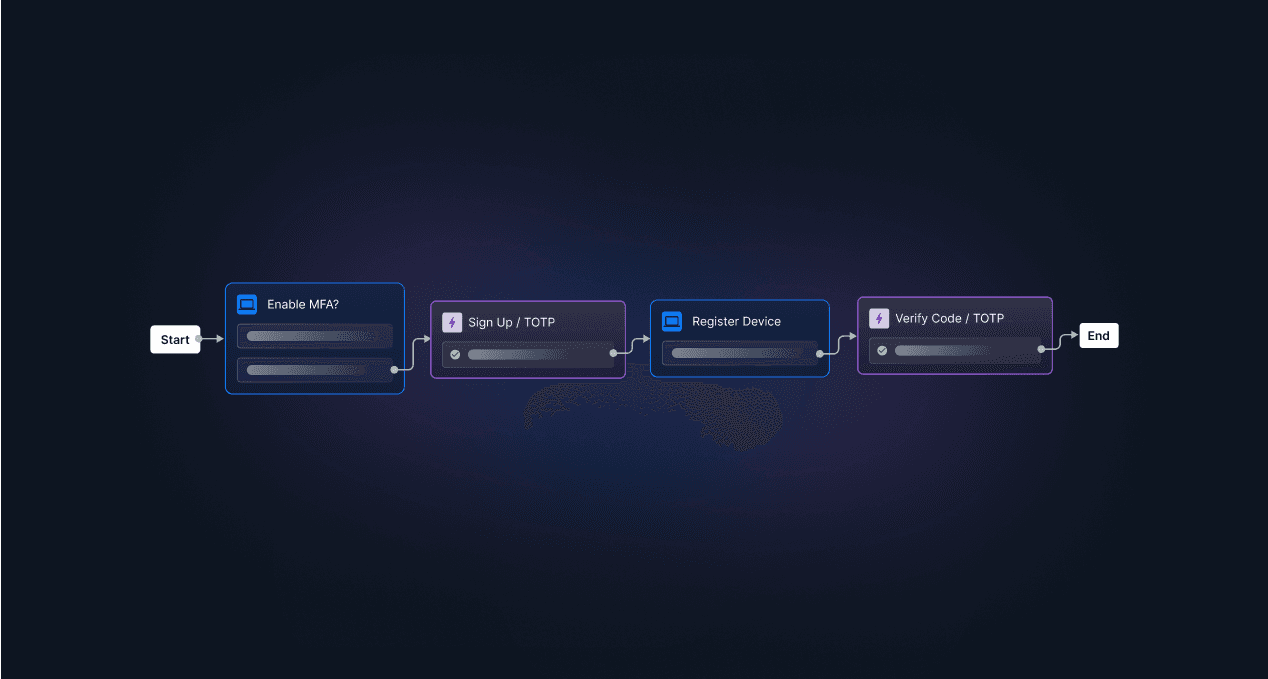
Ready to see Descope in action? Sign up for Descope and secure your app with an authenticator app that requires just a few lines of code today.






