Table of Contents
What is ABAC?
Timely, secure access to digital resources is one of the most important elements of all IAM deployments. Access control, broadly speaking, is what allows organizations to ensure users are able to access the files they need and that the people accessing those files are who they claim to be—rather than cybercriminals.
Attribute-based access control (ABAC) is one of the best ways to achieve these goals, leveraging important details about the user and information in question, along with the environment, to determine whether to grant access.
What is ABAC?
As the name suggests, ABAC is a fine-grained approach to access control that analyzes and makes decisions based on attributes related to the:
Entities making the request
Assets targeted and actions requested
Environment in which it all occurs
When a user attempts to gain access to a file or system, the ABAC solution checks against these components (fleshed out in the next section) and determines whether access is warranted. If the access case is deemed safe and appropriate, the user will be authorized. If not, they may be denied or asked to provide additional information.
Another approach that functions similarly to ABAC is role-based access control (RBAC). When comparing ABAC and RBAC, the former is more flexible and multi-faceted. Unlike ABAC, RBAC focuses solely on users and their roles, determining authorization based on this category alone.
Read more: Your Guide to Relationship-Based Access Control (ReBAC)
The core components of ABAC
At its base, ABAC is about managing complexity (while also being pretty complex itself). It’s what distinguishes it from RBAC and other access control bases. And it’s the reason some experts see attribute-based solutions as the future of security—and the end of data compromise. But, despite that complexity, ABAC attributes all exist within a relatively simple core of components hinted at above (users, assets, etc.).
The fundamental elements of any ABAC system break down as follows:
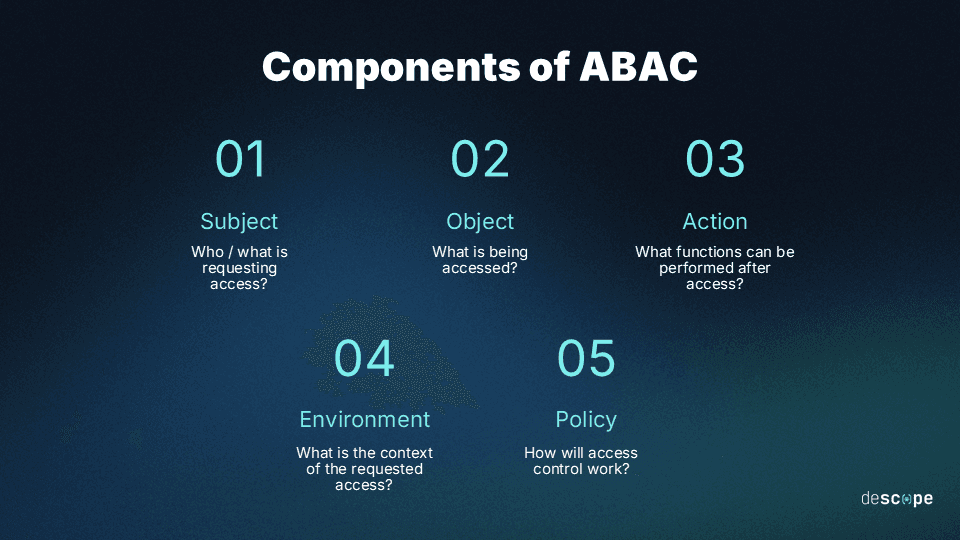
ABAC subjects
In an access control or auth context, a subject is an entity attempting to gain access to a given resource or area i.e.an object (see below). Attributes related to the subject may include the identity of the individual or machine requesting access, their role(s), their location, the devices or platforms they are using, their history of usage and access, and other related factors.
ABAC objects
Objects in ABAC are assets, resources, and locations that a subject is attempting to access. These may be individual files or other pieces of data, or they may be larger platforms on which this data is stored, transmitted, or processed. Attributes related to these include the kind of data, its properties, and sensitivity or other concerns related to legal or regulatory codes.
ABAC actions
Actions in an access control context are the specific functions a user is able to conduct if granted access. The most basic examples are viewing, editing, and downloading files. But attributes related to actions add conditionals and degrees of activity, such as limited viewing privileges or specific kinds of editing, deleting, copying, or other modifying functions a user can perform.
ABAC environment
The environment for ABAC purposes is the context in which an access request occurs. Attributes include the physical location and time of day for both subject and object, along with the virtual location and history of both. Advanced ABAC systems may also take into account any risks present or prevalent in the physical or virtual spaces the subject and the object occupy.
ABAC policies
Policies are the governance initiatives, rules, and intentions put in place to control how access does and should work within a given environment. Attributes include external laws and legal considerations at the state, local, or federal level, along with internal requirements and rules imposed by management. Other factors may include partner or industry-wide best practices.
How ABAC works
In practice, ABAC grants subjects (users) authorization by determining that they do, in fact, have the right to perform the kinds of actions they are requesting on the selected objects.
Here is the basic process by which this works in most ABAC configurations:
Attribute collection: Factors related to all components are identified and distributed, with relationships and contingencies mapped onto protocols for granting authorization.
Policy definition: Policies are drafted, disseminated, and implemented to ensure that attributes are managed accurately and adjusted as necessary manually or automatically.
Access request: Users attempt to access a resource. An access request is generated, containing the relevant attributes.
Policy evaluation: The system analyzes attributes associated with access according to applicable policies and determines whether and under what conditions to grant it.
Decision enforcement: The system either denies access outright or allows it under strict monitoring, with the ability to revoke it or request re-authorization later.
Logging and auditing: Access requests, decisions, and results, including detailed descriptions of the login process and the access session, are logged and analyzed.
Pros and cons of ABAC
The complexity of ABAC allows for unparalleled flexibility and configurability across access control and monitoring. ABAC systems can account for a wider variety of contingencies and exceptions than other, similar systems, which in turn makes preventing illicit access easier and more effective while also facilitating fast and easy access for legitimate, good-faith operators.
At its best, a well-functioning ABAC system encourages and leverages robust data collection, helping maximize and operationalize intelligence for UX, security, and many other purposes.
But, just like the benefits, the potential downfalls of ABAC also relate to its inherent complexity.
Attributes need to be managed carefully, and profiles and policies need to be updated to ensure that the system is functioning as desired. This requires greater bandwidth and overall resources both during implementation and throughout system lifecycles, which in turn can be costly.
In the most extreme cases, an over-complicated ABAC deployment can cause a combination of security vulnerabilities and bottlenecks that hamper daily access rather than streamlining it.
Is ABAC right for your organization?
ABAC makes the most sense for organizations that require the most flexible and scalable control over access. These include environments where roles and responsibilities are harder to define in terms of access needs and restrictions or those in which access privileges come close to case-by-case decisions for each individual stakeholder. If that’s the case, you may need ABAC.
For example, ABAC is well suited for:
Large enterprises with diverse departments, numerous employees and varying access needs.
Healthcare organizations where patient data safety is paramount.
Financial institutions, like banks, that deal with sensitive data and have to comply with regulatory requirements.
Government agencies handling classified information with varying clearance levels that need strict access control.
Read more: Coarse-Grained vs Fine-Grained Authorization: Which to Use?
Implementing ABAC: The hard and the easy way
Given the benefits of ABAC, it’s viable for a wide variety of use cases. The ways to add it to a given app or software project can vary, but the general process of implementation includes:
Identifying and collecting attributes to be used for authorization
Designing policies that determine relationships and protocols
Selecting tools and technologies, including but not limited to policy decision points, policy enforcement points, and attribute stores
Integrating the ABAC system with existing software
Deploying and monitoring access control functionality
Maintaining and updating policies, attributes, and tools
A less complicated way to implement ABAC is with an IDaaS provider like Descope, which supports both RBAC and fine-grained authorization like ReBAC and ABAC. Descope’s SDKs and APIs help organizations greatly simplify their FGA rollout.
Explore our ABAC documentation to learn more. If you’re ready to begin, sign up for a Free Forever account. Have questions about our platform or about authorization in general? Book time with our auth experts to learn more.




