Table of Contents
The evolution from passwords to PCI DSS 4.0
Every time a major retailer, bank, or ecommerce platform suffers a breach, the same culprit emerges: compromised authentication. Despite billions spent on reinforcing outmoded security models, payment environments remain vulnerable to simple password theft and credential stuffing attacks.
The Payment Card Industry Data Security Standard (PCI DSS 4.0) aims to address these threats with stricter authentication requirements. But traditional methods—like one-time passwords (OTPs)—have proven both vulnerable to attack and frustrating to use. There's a solution, however, that elegantly addresses both security and usability concerns.
Passkeys, built on the FIDO2 standard, represent a fundamental shift in authentication strategy. Rather than relying on what users know (passwords), passkeys leverage what users have (their devices) and what users are (their biometrics). This evolution not only enhances security but also aligns perfectly with PCI DSS 4.0's authentication requirements.
This blog discusses how passkeys can help you meet 4.0 compliance while actually improving your security posture and user experience. We’ll explore their advantages in securing payment environments, and examine practical steps for implementation.
The evolution from passwords to PCI DSS 4.0
Passwords have been a staple of authentication for decades, but their inherent weaknesses make them a liability in modern cybersecurity. Breaches resulting from weak, reused, or stolen passwords are a leading cause of security incidents. While multifactor authentication (MFA) provides additional layers of security, traditional methods like SMS one-time codes remain vulnerable to phishing and interception.
PCI DSS 4.0 addresses these vulnerabilities through strict requirements in Requirement 8:
Requirement 8.4.2: Requires MFA for all access to the Cardholder Data Environment (CDE)
Requirement 8.4.3: Mandates MFA for remote access originating from outside the entity's network, including administrative, non-administrative, and third-party/vendor access
Requirement 8.5: Ensures MFA systems resist replay attacks and grant access only after successful verification of all factors
To comply, organizations must implement at least two independent authentication factors:
Knowledge, or something you know: Passwords, PINs
Possession, or something you have: Hardware tokens, smart cards
Inherence, or something you are: Biometrics, like fingerprints or facial recognition
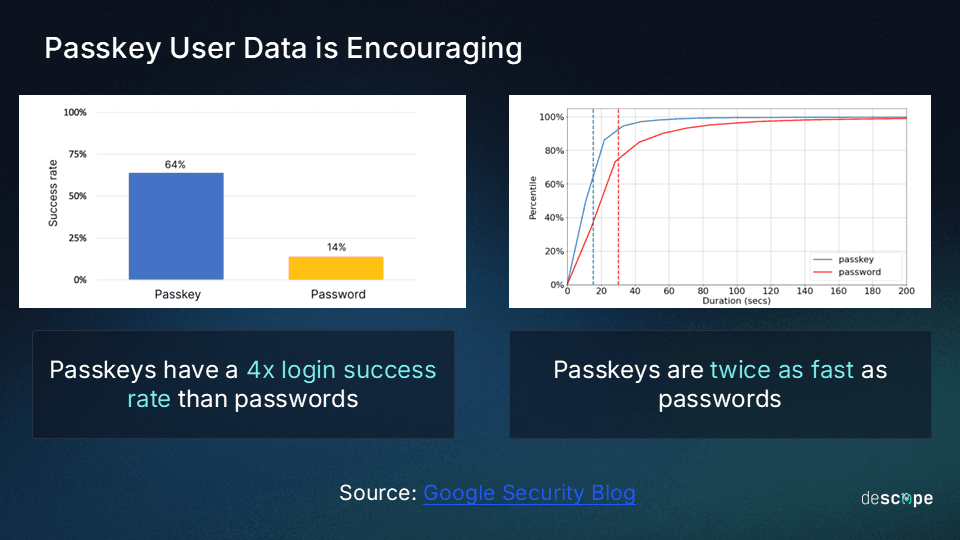
This is where passkeys shine. Built on the FIDO2 standard, passkeys replace vulnerable passwords with a combination of trusted devices ("something you have") and biometric verification ("something you are"). This approach not only satisfies PCI DSS requirements but eliminates the security gaps inherent in traditional authentication while providing a smoother user experience. In fact, the Google team found that passkeys were twice as fast as passwords and also had four times higher login success rate.
Passkeys vs. other passwordless methods for PCI DSS compliance
While passkeys offer numerous advantages, other passwordless options remain viable in specific contexts:
Hardware security keys: Devices like YubiKeys provide strong "something you have" authentication for high-security use cases.
Device-based authenticators: Smartphone apps like Microsoft Authenticator or Google Authenticator offer flexible MFA solutions.
Passkeys, however, excel in scenarios requiring seamless cross-device functionality and consumer-friendly adoption, making them an ideal choice for consumer-facing 4.0 compliance.
Why passkeys are a game-changer for PCI DSS compliance
1. Eliminating password vulnerabilities
Passwords are a major source of security breaches, vulnerable to phishing, credential stuffing, and brute-force attacks. Passkeys remove these risks by eliminating passwords entirely. Instead, private keys are securely stored on user devices and never transmitted, making them immune to interception or reuse.
2. Enhanced security with cryptography
Passkeys leverage public-key cryptography, ensuring that only the legitimate user can authenticate. The private key remains securely stored on the user’s device, while the corresponding public key resides with the service. Each authentication attempt generates a unique, cryptographically signed request, resistant to replay and man-in-the-middle attacks.
3. Improved user experience
Passkeys provide a seamless authentication experience. Users no longer need to remember or reset passwords. Biometric integration allows for quick, effortless login, reducing friction for employees and consumers alike.
4. Cross-device synchronization
Passkeys are securely synchronized across trusted devices via cloud ecosystems like Apple iCloud Keychain and Google Password Manager. This ensures continuity even if a device is lost, with users able to recover their credentials without compromising security.
5. Compliance with replay resistance
Requirement 8.5 of PCI DSS 4.0 specifies that MFA systems must prevent replay attacks. Passkeys fulfill this requirement by generating unique authentication signatures for each login attempt, ensuring that intercepted data cannot be reused.
6. Reduced operational costs
Password resets are a significant drain on IT resources, accounting for a substantial percentage of help desk requests. By eliminating passwords, passkeys reduce administrative overhead, allowing IT teams to focus on more critical tasks.
Real-world applications of passkeys in PCI DSS compliance
1. Securing remote access
Remote work has become a standard for many organizations, increasing the need for secure access to payment environments. Passkeys provide a robust solution by replacing VPN passwords with device-based authentication, satisfying PCI DSS 4.0’s MFA requirements.
Example use case: A payment processor implements passkeys to secure administrative access for remote employees, ensuring that all connections to the CDE meet compliance standards.
2. Enhancing consumer authentication
Ecommerce platforms and online payment systems often face user drop-offs due to cumbersome login processes. Passkeys streamline authentication for consumers, improving user satisfaction and conversion rates.
Example use case: An online retailer replaces passwords with passkeys for customer accounts, reducing account takeovers and enhancing the checkout experience.
3. Managing third-party vendor access
Third-party vendors often require access to sensitive systems, making secure authentication critical. Passkeys provide a scalable, secure way to authenticate external users without exposing the organization to unnecessary risk.
Example use case: A financial institution uses passkeys to manage vendor access, ensuring that all third-party connections comply with PCI DSS 4.0.
Steps to implement passkeys in a PCI DSS-compliant environment
Step 1: Evaluate current authentication systems
Assess your existing authentication methods to identify where passkeys can replace passwords or enhance security. Focus on high-risk areas in your payment environment, such as remote access points, administrative systems, and transaction authorization flows.
Step 2: Ensure compatibility with PCI DSS
Verify that your chosen passkey solution meets PCI DSS requirements for encryption, independence of factors, and replay resistance. Solutions based on FIDO2 and WebAuthn standards typically fulfill these criteria. Document how each requirement is satisfied for audit purposes.
Step 3: Secure enrollment processes
A secure enrollment process is critical to prevent fraudulent registrations in payment environments. Verify user identity during onboarding and implement additional checks for high-risk accounts, particularly those with transaction authorization capabilities.
Step 4: Educate stakeholders
Provide clear guidance to employees, vendors, and consumers on passkey benefits and usage. Focus on explaining the enhanced security and simplified user experience compared to traditional passwords and MFA methods.
Step 5: Deploy incrementally
Roll out passkeys strategically, starting with a portion of your userbase or with A/B testing. Gradually expand while maintaining familiar fallback methods during transition. Monitor login success rates to identify potential friction points.
Step 6: Monitor and audit regularly
Conduct periodic audits to ensure ongoing PCI DSS compliance. Monitor authentication logs for anomalies and verify that passkey systems remain resistant to emerging threats. Pay particular attention to authentication patterns around payment operations.
Conclusion
Passkeys represent a transformative step forward in authentication, offering businesses a secure, user-friendly solution to meet PCI DSS 4.0 requirements. By eliminating passwords, passkeys close critical security gaps while improving usability and reducing operational overhead.
For organizations navigating the complexities of PCI DSS compliance, passkeys are not just a compliance tool—they are an investment in the future of secure authentication. Whether securing remote access, enhancing consumer experiences, or managing vendor credentials, passkeys provide a robust, scalable solution for today’s challenges.







