Table of Contents
What is a passkey?
For over half a century, password-based authentication has been the de facto method for users to log into their online accounts. Yet, day by day (and data breach by data breach), passwords have caused friction for end users, provided cybercriminals with ammunition to carry out their attacks, and burdened IT teams with help desk tickets.
The growing adoption of passkeys has the potential to change all of this.
So, let’s understand what’s under the hood of passkeys and weigh their pros and cons so you can make an informed decision on implementing this passwordless authentication method.
Main points
What is a passkey? A passwordless, phishing-resistant authentication method using public-key cryptography.
How it works: Uses a public-private key pair; the private key stays on the device, and authentication happens via biometrics or a PIN.
Security & benefits: Eliminates phishing and credential theft, enables seamless MFA, and protects user privacy.
Considerations: Adoption is growing, but challenges include cross-device compatibility and implementation complexity.
What is a passkey?
A passkey is a phishing-resistant, passwordless authentication method based on public-key cryptography. It is designed to replace passwords (which are knowledge-based) with a more secure and user-friendly login experience.
A passkey consists of a private key, securely stored on a user's device, and a public key, registered with a service. Authentication happens via biometric verification (Face ID, fingerprint), a device PIN, or a security key, without the need to manually enter a password.
Over the past few years, passkeys have been adopted by major tech companies, such as:
Apple announced passkey support for work environments at WWDC 2023.
Google announced passkey support for Chrome, Android, personal email accounts, and Google Workspace.
Microsoft supports this method through Windows Hello and other passwordless services.
Shopify adopted this method to ease friction in the ecommerce shopping experience. Curious to learn more? Check out this ecommerce authentication guide.
PayPal introduced passkeys for more secure payment processes.
Experience passkey authentication on this demo site before you adopt it for your app.
Passkey vs. password
Passwords are based on the idea of a shared secret between the user and the service they are accessing. The user creates a password, which is stored on the service's server (often in a hashed form). When logging in, the user enters the password, which is then compared to the stored version. If they match, the user is granted access. However, passwords are vulnerable because they can be guessed, stolen, or reused across different sites, leaving them exposed to attacks like brute force or phishing.
Passkeys, on the other hand, eliminate the need for a shared secret. When setting up a passkey, a unique pair of cryptographic keys is generated. The private key is stored securely on the user’s device, and the public key is stored on the service's server. When logging in, the service sends a challenge that can only be completed by the private key, which is then verified by the public key on the server. To authenticate, users must also provide biometric data or a PIN, adding an extra layer of security. This method is phishing-resistant and ensures that sensitive data, like biometric information, never leaves the user’s device.
Read this complete breakdown of passkeys vs. passwords.
How do passkeys work?
As mentioned before, passkeys rely on public key cryptography, a technique that uses a public-private key pair to function. So, when a user registers, their device generates a key pair of:
Public key: Used to encrypt data and is stored on the server
Private key: Used to decrypt data and is stored on the user’s device (such as a phone, computer, or hardware security key). The private key never leaves the device.
Think of cryptographic keys like a mailbox with different keys for the mailman and the homeowner.
The protocols making all of this possible are WebAuthn and FIDO2, which enable applications to authenticate users with possession-based and biometric authentication.
Passkey authentication can be divided into two processes (also known as ceremonies): registration and authentication.
Registration ceremony
This process occurs the first time a user creates a passkey for a particular account. This is when the public-private key pair is created and stored on the app and device, respectively. The flow diagram below covers the registration ceremony:

The user starts the registration ceremony by choosing to authenticate with passkeys for the first time on an app.
The app gives the client (e.g., browser) the configurations to create a new credential.
The client passes these configurations over to the authenticator. The authenticator can be external (like a FIDO2 security key) or a platform authenticator (like Apple Face ID, Apple Touch ID, or Windows Hello).
The authenticator requests the client for user verification and presence.
The user completes verification (commonly done through biometric scans).
The authenticator now creates a public-private key pair and sends the public key to the client. The authenticator stores the private key.
The client sends the public key to the app for storage.
The user has now registered a passkey for the app. When the user next tries to log in on the same app, the authentication ceremony occurs.
Authentication ceremony
The flow diagram below shows how the authentication ceremony works:
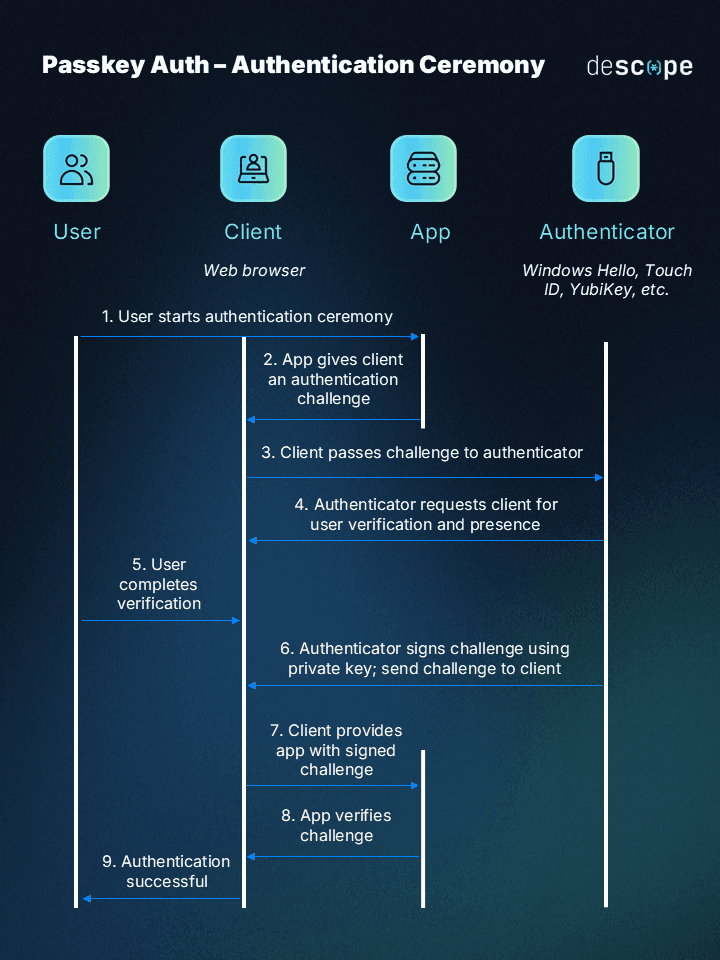
The user starts the authentication ceremony by selecting passkeys as the login method.
The app gives the client (browser) an authentication challenge.
The client passes this authentication challenge to the authenticator.
The authenticator requests the client for user verification.
The user completes verification using the method they selected during the registration ceremony (biometrics, pattern, PIN).
The authenticator signs the challenge using the private key created during the registration ceremony. It sends this signed challenge to the client.
The client provides the app with the signed challenge.
The app verifies the challenge with the public key.
If the challenge is verified, authentication is successful and the user is logged in.
Are passkeys secure?
Passkeys are among the most secure authentication methods available. They offer superior protection against broken authentication compared to traditional passwords or other passwordless methods. The private key is never shared with third parties, eliminating the "shared secret" vulnerability. Experts agree that passkeys are highly secure, with their biggest advantage being complete immunity to phishing.
Descope Chief Security Officer Omer Cohen:
“Passkeys only work with the service that created them, meaning there's zero chance of exposure on a spoofed domain. Phishing targets what the user might unknowingly divulge: credentials and OTPs. But you can't trick someone into sharing keys even they can't fully access.”
Can passkeys be stolen or hacked?
The private key used in passkey authentication can’t be stolen or hacked. It doesn’t reside on servers and requires a biometric scan to be accessed. Even if a device is stolen, the key itself remains secure.
Passkeys are so safe that people wonder if they would be able to recover them in case the device with he private key is lost. Most systems have recovery options. For example, Apple’s passkey recovery requires a security code and multiple verification steps. If the recovery process fails, the passkey data is destroyed, ensuring the method is virtually immune to theft and hacking.
So, are passkeys safer than passwords?
Yes!
Convenience isn’t the only reason passkeys are replacing passwords. Another major factor is the fact that passkeys do away with many of the security vulnerabilities that plague traditional passwords:
Weak passwords: Users often create easily guessable passwords, like pet names or birthdates, despite system requirements for complexity.
Brute-force attacks: Even strong passwords can be cracked by automated login attempts.
Credential theft: Stolen passwords, no matter how strong, can’t protect against cyberattacks.
Social engineering: Phishing and other tactics trick users into giving up their credentials.
Passkeys eliminate these risks, offering a far safer alternative to passwords.
Benefits of passkeys
Besides the security benefits, there are also many others that make passkeys loved and preferred by end users and app developers alike.
Better user experience: Millions of users are already familiar with device-based biometrics and PINs since they use these mechanisms to unlock and interact with their devices every day. Since passkeys use the same process to log into apps, they easily fit into users’ existing mental models. Not to mention, a scan of a face or fingerprint is much faster than creating, remembering, and typing in a “strong” 16-character password.
Frictionless MFA: By checking the user’s device (possession) and biometrics (inherence) in one user-facing step, passkeys are one of the safest MFA methods. By enabling MFA without added friction, passkeys can pave the way to truly universal MFA adoption.
Privacy-first: Any mention of biometrics often brings up privacy concerns, but passkeys take care of that from the outset. A users’ biometrics never leave their device, so there is no way attackers can “steal” biometric data. Passkeys are also unique for every app and cannot be used to track users across sites.
Drawbacks of passkeys
Since passkeys are still early in their lifecycle, there are a few things app developers should consider before adoption:
Compatibility: Although adoption grows by the day, passkeys will still take some time to be supported by all major browsers, sites, and platforms. It’s also unclear right now how users can transfer passkeys across devices from different providers (say when they move from an Android phone to an iPhone).
Implementation complexity: As easy as passkeys are for the end user, implementing them is not trivial for app developers. Compared to passwords and even other passwordless methods, passkey authentication has a lot more moving parts, testing, and validation involved. For this method to truly achieve widespread adoption, developers need the tools and resources to easily add this authentication method to their apps.
Learn more: Developer Guide: How to Implement Passkeys
Simple passkey authentication for your app
Want to add passkeys to your authentication flow? You can either build it in-house by learning the WebAuthn standard, spinning up FIDO servers, testing and validating the various flows, and handling errors. Or you can use Descope as your passkey provider!
Our drag-and-drop CIAM platform makes it very easy for developers to add passkeys to their apps with a few lines of code. Even customers of other identity providers such as Amazon Cognito, Firebase, Okta CIS, and Auth0 can use Descope as a federated IdP to add biometrics to existing login processes.
Sign up for a Free Forever account and get started with your passkey journey today. We’d love to have you over at AuthTown, our open user community for developers to learn about authentication.