Table of Contents
The benefits of OAuth and centralized identity management
This is Part 4 of the “The Power of Descope Flows” blog series that will cover how our drag-and-drop authentication platform can be used to add, modify, and update authentication on any app or website. In this blog, we cover how Descope Flows can be used to merge identities of a single user across many different authentication methods.
Check out Part 1, Part 2, and Part 3.
When adding social logins based on the OAuth and OpenID Connect standards to your app, it’s paramount to implement them with the highest levels of security in mind. Today, Descope disclosed an authentication implementation flaw affecting Microsoft Azure AD OAuth applications. When exploited, this misconfiguration can allow attackers to perform full account takeover on victim accounts – and incorrectly merging the attacker’s account with that of a legitimate user makes things much worse.
In this post, we will explore how Descope Flows – our drag-and-drop authentication workflows – can be used to verify user emails when the “email” claim from the identity provider cannot be trusted, ensuring secure unification of user identities across different authentication methods.
The related video below shows how to merge identities across different authentication methods - in this case, social logins, SMS OTP, and passkeys.
The benefits of OAuth and centralized identity management
If you’ve ever used “Log in with Google”, “Log in with Microsoft”, or similar methods online, you have seen OAuth in action. When implemented correctly, OAuth is a powerful, user-friendly standard that makes login swift and seamless.
Since authentication is based on pre-established trust with an identity provider, users don’t need to create an additional set of credentials for every new app they need to access. This not only makes the process frictionless for the user, but also improves security by obviating the need to create new passwords that can be easily leaked or stolen. Since a user’s identity is centrally managed, they only need to remember one set of login credentials across multiple applications.
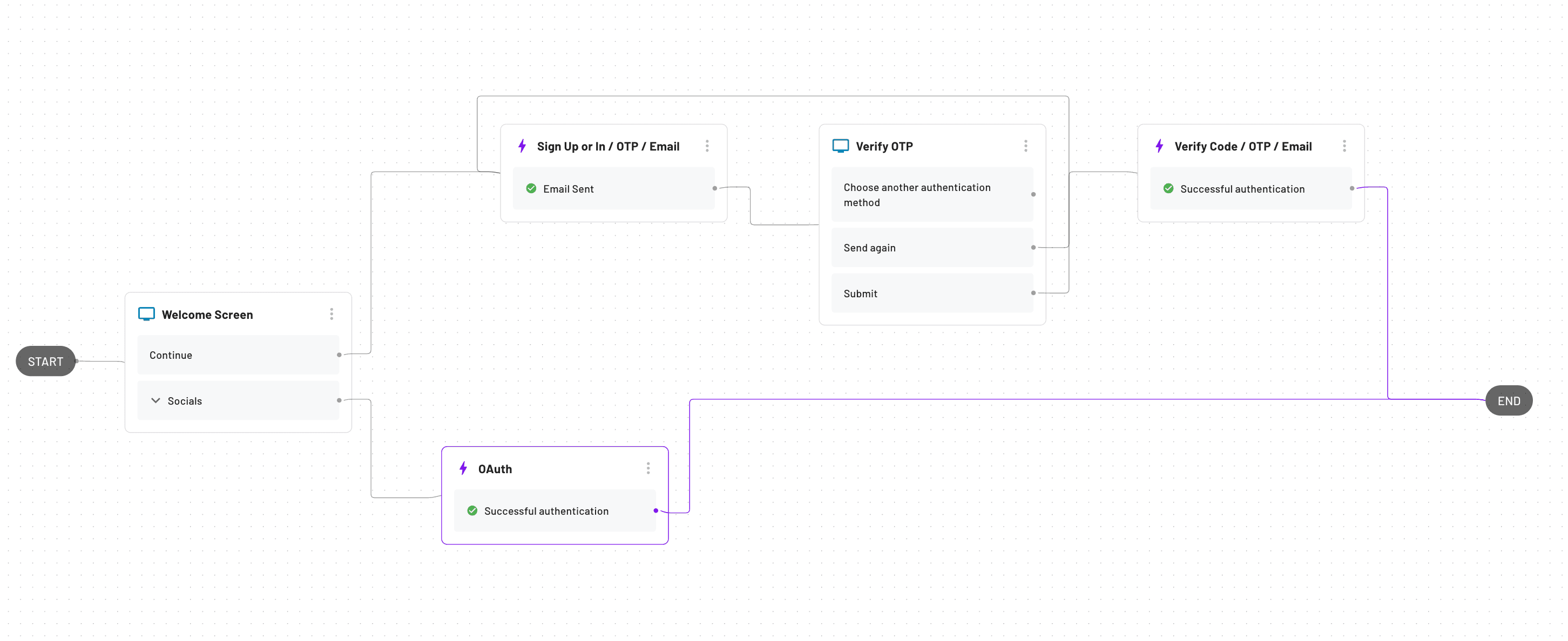
This is an example of a Descope Flow that allows both OAuth and Email based login:
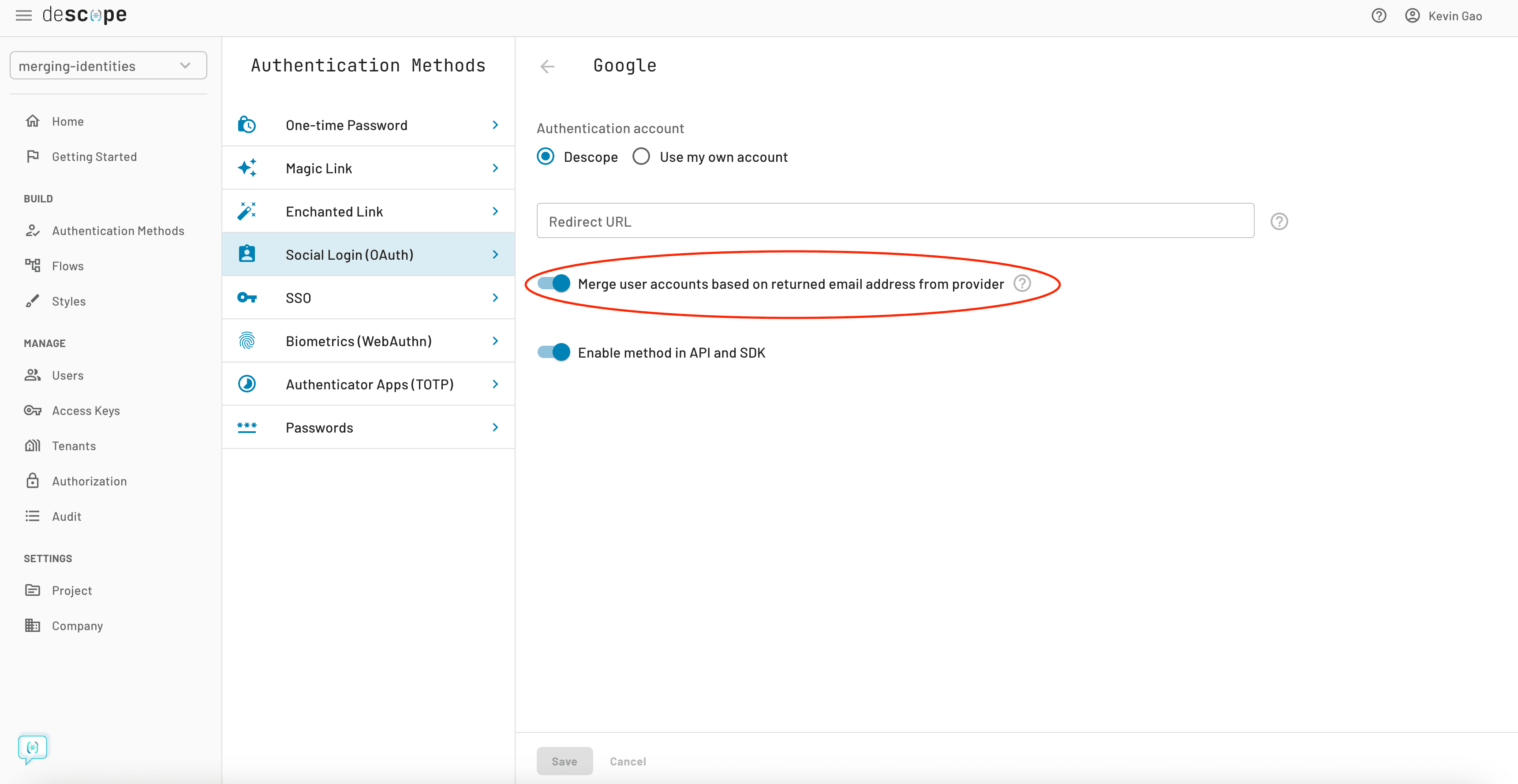
In the Descope Console, when you select “Authentication Methods” and then “Social Login (OAuth), you will see an option to “Merge user accounts based on returned email address from provider” as a toggle (Google shown as an example in the screenshot below). This option exists for every identity provider, enabling you to automatically merge users based on a single email across multiple email-based identification methods.
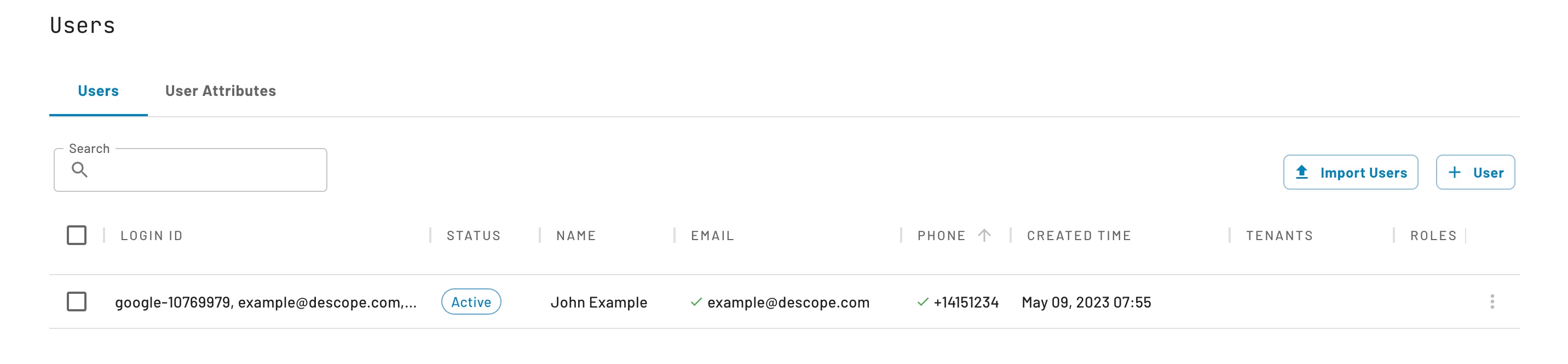
Every user and their respective attributes will then appear in the “Users” portal, under one unified identity. You will see that each user has either one or multiple login IDs, which are unique identifiers that are used to reference a user in authentication and user attribute management.
It’s clear that OAuth and centralized identity management have several benefits. However, there are many parts under the hood that have to work to ensure that your users’ identities are safeguarded.
The importance of email verification and login IDs
When implementing OAuth login, you essentially leave the ball of authenticating the user in the court of the OAuth identity provider (Google, Microsoft, etc.). When you get the claims back from a successful OAuth login, most auth platforms will just assume the user is successfully verified by trusting the details returned by the identity provider.
Generally speaking, there are two ways to manage identities once you get the claims back from the OAuth identity provider:
Verified email: Either merge the identities if a previous user with the same email exists, or create a new user
No verified email: Simply create a new user with a unique identifier from the OAuth identity provider without including the email that is returned in the OAuth claim.
However, if the “email” claim returned by the IdP is mutable and cannot be trusted, your app can be vulnerable to account takeover if you merge a new account with an existing account based on a common email. For example, Azure AD documentation states that the “email” claim should NOT be used as a unique identifier for authentication.
Imagine a malicious user changing the email address in their Azure AD account to that of a user that already exists in your platform. When that malicious user uses “Log in with Microsoft” on your app – and you erroneously merge the account with that of your existing user – they will be able to successfully impersonate your user.
Using Descope Flows, you can protect users from the aforementioned exploit by verifying the email when “Log in with Microsoft” is used before merging multiple OAuth accounts.
The solution: verify emails before merging identities
Adding email verification to your authentication flow is just a matter of dragging and dropping a few actions and screens in Descope. Here are the general steps:
Click “Flows” in the Descope Console and open up a Flow.
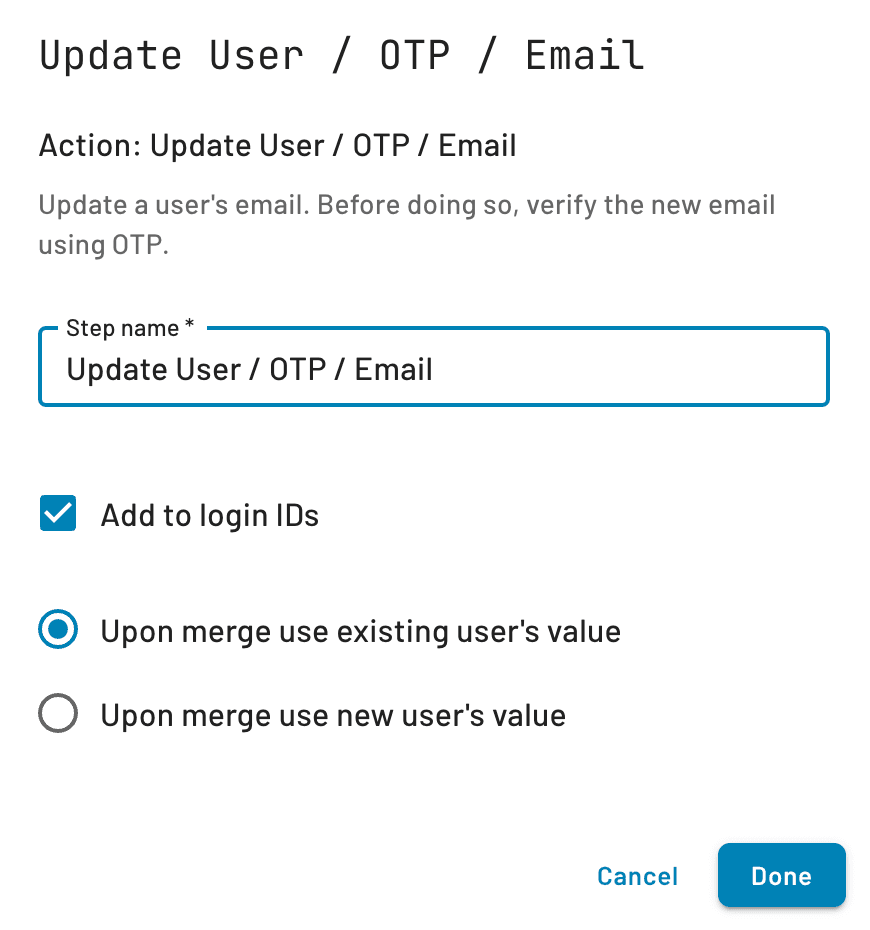
Add an Update User action block with either OTP, Magic Link, or Enchanted Link to your Flow.
Make sure to select the “Add to Login IDs” and “Upon merge use existing user’s value” options (More on this below).
Add another Screen block that will prompt the user to input their email address for validation via OTP, Magic Link, or Enchanted Link, depending on the block you added in step 2.
Connect the OAuth Successful Login block to the Screen, and connect the Screen to the Update User action block.
After that, just end the Flow, and you’re done!
The email verification section of your Flow will look something like this:
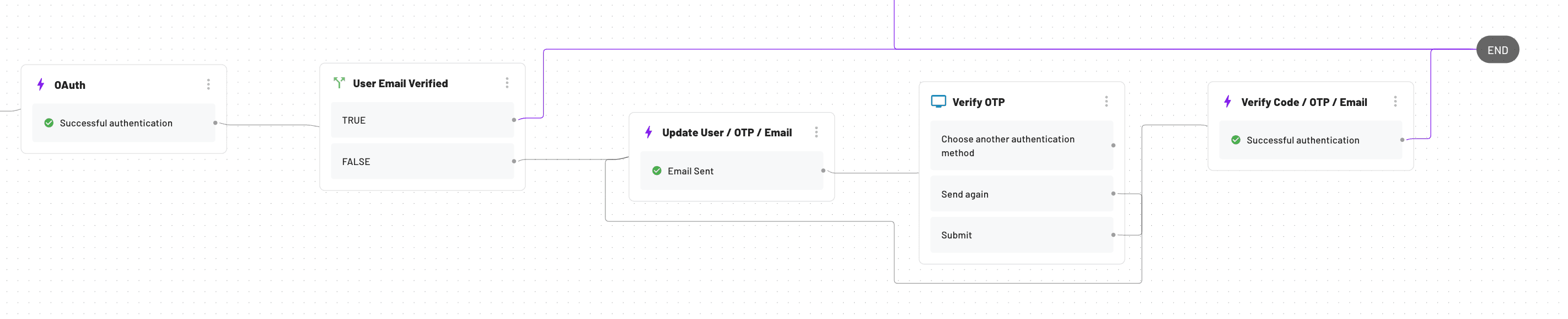
With this Flow, you can easily customize your app’s authentication to verify the email of new OAuth users and merge their identities with previous accounts, while also protecting against the misuse of unverified emails.
You may also be curious about the two merge options under the “Add to login IDs” checkbox. The purpose of these options is to either keep the previous user’s attributes, or replace all of them with the ones from the new user’s only in case of conflicts. Don’t worry though: in either case the login IDs used for authentication will be preserved!
The importance of secure OAuth
The world of authentication, identity management, and authorization can get complicated quickly, especially if you are building these initiatives in-house. As online identities get more interconnected with standards such as OAuth, it’s vital that apps and authentication platforms implement these standards with a security-first mindset. This includes verifying the user’s email if the “email” claim returned by the OAuth identity provider can’t be trusted (as is the case with Azure AD).
Descope helps app developers centralize user identities across authentication methods, streamlining user management and enhancing the end user experience. The ability to drag-and-drop email verification into authentication flows saves a lot of time for developers, provides a visual representation that can be reviewed by product and security teams, and is more future-proof than writing tons of new code.
If you’re curious to try Descope, sign up for our “Free Forever” tier and join AuthTown – our open user community – if you have any questions as you explore our authentication platform.