Table of Contents
What is coarse-grained authorization?
For IT and engineering teams, authorization remains a priority for their apps and systems to function as intended. It’s critical to guarantee that only authorized individuals gain access to particular resources to safeguard sensitive data from potential misuse or exposure.
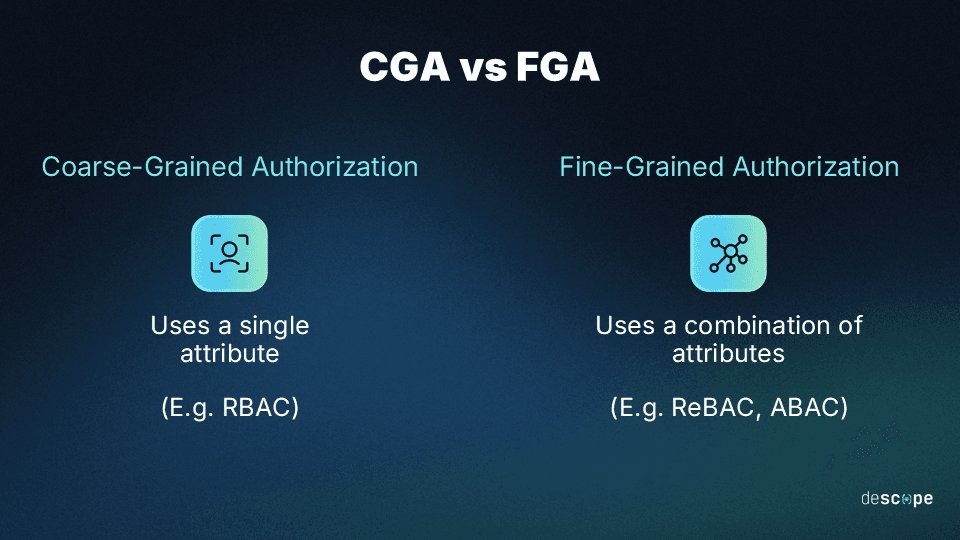
Two common authorization approaches govern access control through generalized conditions or more complex combinations of conditions. The former is called “coarse-grained,” while the latter is called “fine-grained”. Both have specific use cases, pros, and potential cons.
Coarse-grained authorization (CGA) uses one attribute (like user roles), making access control simple for smaller setups. Fine-grained authorization (FGA) uses a combination of detailed attributes, offering precise control for larger, intricate environments. CGA is straightforward and less time-consuming, while FGA delivers granularity at the expense of increased effort.
In this article, we’ll walk through fine-grained vs. coarse-grained authorization to determine the best option for your business.
What is coarse-grained authorization?
Coarse-grained authorization (CGA) is a method of implementing user authorization based on a single account attribute. For example, when users attempt to log in, view or edit a document, move a file from one location to another, or make any other action, the given attribute determines if they can.
The chosen attribute is loosely defined to allow for fewer restrictions in access and ease of use for all involved.
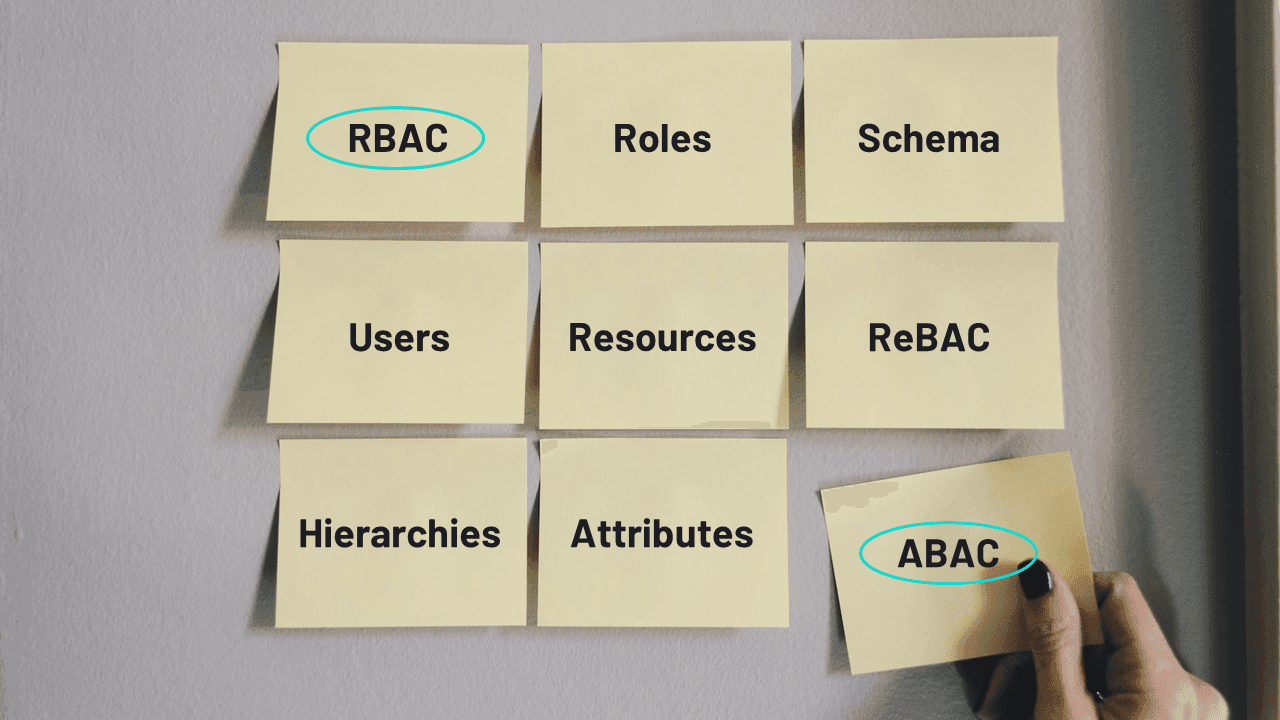
The most widely-used coarse-grained attribute is role, as in a role-based access control (RBAC) system. In these deployments, a user’s role—or, more often, the roles they’ve accumulated—will determine the scope of their authorization and privileges.
Pros and potential cons of coarse-grained authorization
The most significant benefit of any CGA deployment is its simplicity. In CGA setups, admins usually select individual attributes that are relatively easy to assign and manage. From the end user’s perspective, most elements of the login and access control process are seamless. On the management side, the only challenge inherent to the system is ensuring that user attributes are accurate and up-to-date.
Because of this simplicity, CGA systems incur relatively low setup and ongoing costs. However, things rarely stay simple for long.
When users’ roles and responsibilities are in flux, a flexible and dynamic approach may be required to accommodate fluidity in users’ status. Users might need permissions for important tasks that could be denied due to inaccurate attributes. Conversely, IT admins and developers may face "role explosion" or "role bloat" as the organization grows, needing to create and maintain a mountain of roles to account for all edge cases.
What is fine-grained authorization?
The other approach is fine-grained authorization (FGA), which implements access control through a combination of attributes for greater granularity. As there are more attributes to choose from, the authorization decision can depend on more than one simultaneously.
What this allows for, in practice, is a far more complex deployment based on more in-depth attributes (e.g., IP address, location history, relationship with resource)—or any combination thereof.
There are near-countless variables you can choose from for FGA, especially in interconnected systems. For example, in Microsoft Win32 applications, there are 1420 distinct attributes defined by Active Directory, any or all of which might be called upon for authorization.
While not all attributes may be viable, FGA deployments can be configured around the relationships between entities rather than the presence or absence of a single one. This drives relationship-based access control (ReBAC), a fast-growing authorization model that’s generally used in larger, more complex systems. For even greater granularity, organizations can also opt for attribute-based access control (ABAC).
Pros and potential cons of fine-grained authorization
The biggest benefit of FGA is the greater flexibility and control it offers to admins, leading to better visibility and more robust overall security. A proper FGA deployment is also future-proof and prevents role explosion – since FGA includes a combination of attributes, a user’s access can change dynamically if their role or any other attached attribute changes.
However, fine-grained controls can come with more significant resource costs and related considerations.
FGA systems may be more complicated to configure at startups, as developers and in-house IT staff must determine which attributes are used and in which combinations. This often requires creating rules and schemas as well as accounting for changes to attributes that could lead to exceptions or system-wide rule changes.
In addition, if niche attributes or relationships are selected, end users may have trouble understanding why they were denied access to a particular resource or action (unless communicated clearly by the system).
Which is better: Coarse-grained or fine-grained authorization?
In practical situations, neither solution is better or worse. Their use case depends on the environment in which they’re deployed.
Coarse-grained access control, for example, is generally better suited to organizations with smaller and less complex digital environments or those with smaller amounts of sensitive data. Meanwhile, fine-grained access control is usually better for bigger and more complex IT environments with a variety of users that have interconnected relationships to resources.
Here’s how the two approaches stack up across four significant criteria:
| Coarse-Grained AuthZ | Fine-Grained AuthZ |
|---|---|---|
AuthZ accuracy | Users may lack access to resources they need or retain access to resources after it should have been revoked | Authorization is based on the most appropriate attributes relative to the user, data, and overall IT environment |
Ease of use | Users log in and access files seamlessly as long as account roles and simple attributes are managed effectively | Improper setup and maintenance of attributes may lead to management complications and overhead |
Maintenance | Deployment and account maintenance are streamlined through the use of a single, generally simple attribute | Determining and managing attributes and relationships require significant attention to detail |
Scalability | While simple to set up, scaling CGA can lead to “role explosion” | A well-defined FGA system can scale effortlessly, although it does require more compute |
Security assurance | Attribute bloat can lead to unauthorized access and an overall lack of visibility and accountability for users | Greater control makes unauthorized access less likely, and there is more overall transparency |
Ultimately, the choice between coarse- or fine-grained authorization often comes down to the size and complexity of the IT landscape you’re targeting—and it might not even need to be a choice.
Can you use both coarse- and fine-grained authorization?
The most effective authorization systems usually employ a combination of CGA and FGA techniques. For example, you can start with RBAC for base level access control when your app / project is just getting off the ground. Later on, you can layer in ABAC for granting or denying access based on attributes and ReBAC when relationships between users and resources become important.
Whichever method you choose, it’s vital to ensure that your access control model definitions and implementation are consistent. Overly simple or needlessly complicated policies can lead to security loopholes and misconfigurations respectively.
It’s critical to note that access control is not a “one and done” initiative. Developers and IT admins should regularly review and update access policies to reflect their current organizational needs and security directives.
Authorization for your app with Descope
CGA and FGA are indispensable parts of any app’s architecture and implementation. However, as we’ve seen from this article, they are not trivial exercises and require a lot of time and effort to get right. That’s where Descope can help.
Descope is a drag-and-drop CIAM platform that helps organizations add authentication, authorization, and identity management to their apps using no / low code workflows. With Descope Fine-Grained Authorization, customers can use our SDKs and APIs to easily define and enforce ReBAC and ABAC for their apps.

Sign up for a Free Forever account and check out our ReBAC docs to get started with Descope FGA. Have questions about our platform? Book a consultation with our auth experts to learn more.