Table of Contents
Challenges in B2C authentication
Descope's authentication and user management features are tailored to support any consumer or SaaS application. Here, we'll focus on the B2C capabilities. To learn more about how we support B2B CIAM, you can read this blog.
Our platform offers seamless, passwordless authentication methods, including magic links, passkeys, social logins, One Tap, and one-time passwords (OTPs) via email and SMS. Additionally, we provide flexible, drag & drop authentication options and prebuilt User Interface (UI) components to streamline your development process.
This blog will delve into the challenges of B2C authentication, its significance, and how Descope can help organizations improve onboarding, boost conversions, enhance ATO protection, and efficiently manage user identities. We'll explore the unique functionalities that Descope offers and how it can simplify and expedite your B2C authentication strategy.
Challenges in B2C authentication
B2C authentication presents distinct challenges that require careful consideration:
Bots and account takeover: Safeguarding user accounts from malicious bots and unauthorized access is crucial. Learn more about bot attacks and mitigation strategies in our detailed article.
User friction and drop-offs: Complicated authentication processes can lead to user frustration and increased abandonment rates. The FIDO Alliance reports that 60% of users have given up on accessing an app due to password frustrations.
Static user journeys: Hard-coded authentication flows can hinder necessary changes and adaptations. Engineering teams constantly have to decide whether to implement authentication changes or other core product initiatives.
To address these challenges, B2C organizations need a flexible and secure authentication system that enhances user experience without compromising security.
Implementing B2C authentication with Descope
Descope provides a suite of features tailored to meet B2C authentication needs:
Authentication methods
Descope helps your organization enhance user experience with a variety of authentication methods:
Passkeys: Utilize both device-bound and cross-device passkeys to allow users to log in to your apps using fingerprints or facial scans. Passkeys are becoming a popular auth method for B2C apps since they provide a frictionless experience while also being impossible to phish. Get started with your passkey implementation in this developer guide.
Magic Link: Enable users to log in via a link sent to their email or SMS, eliminating the need for passwords. Perfect for verifying an email with the simple click of a button, phishing resistant due to the same-device requirement.
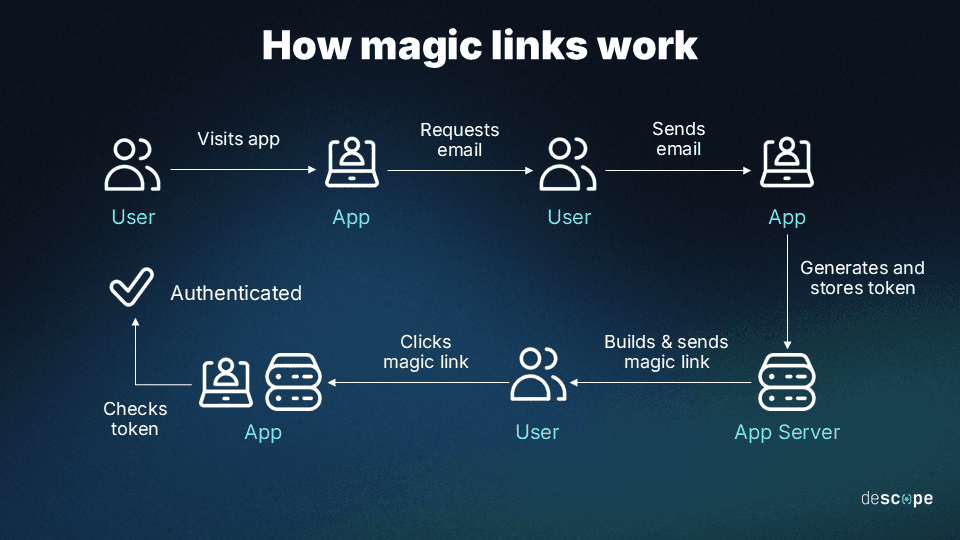
Enchanted Link: Allow users to authenticate by clicking a link on a different device, enhancing flexibility and security. Enchanted links are useful for cross-device workflows, such as signing into a TV app via a mobile device.
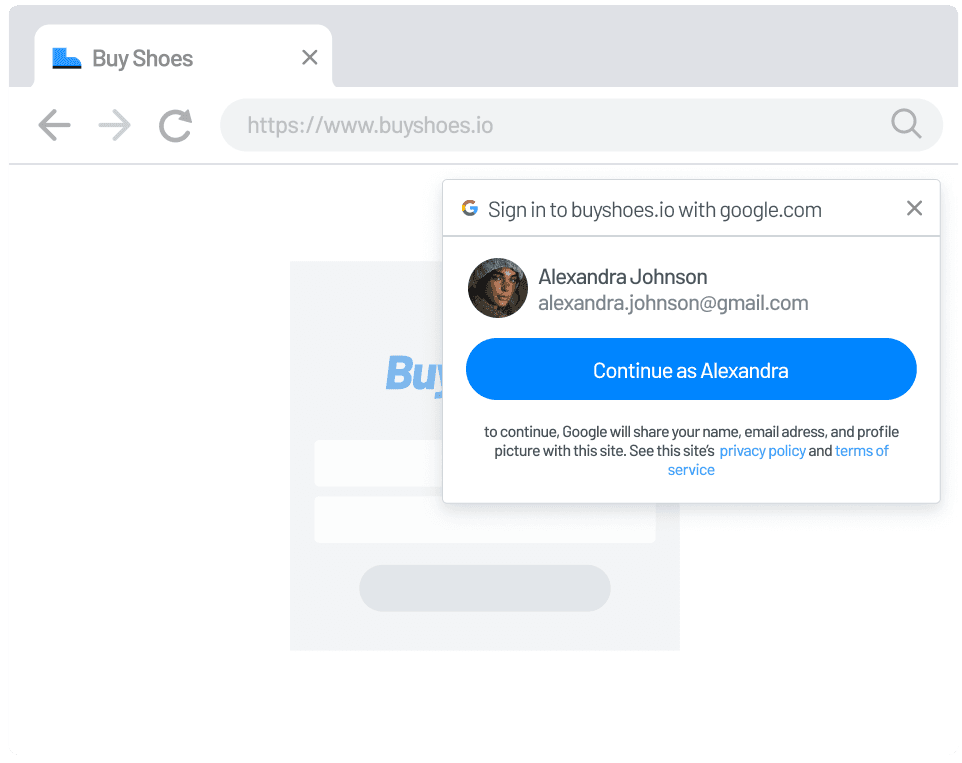
Social Login (OAuth): Allow users to sign in using existing social media accounts like Google, Facebook, or LinkedIn, streamlining the registration process. Lowers barriers to entry, especially when paired with audience-friendly options like Discord for gamers or GitHub for developers.
Google One Tap: Simplify the user login experience with Google One Tap, allowing users to sign in effortlessly without being redirected to a separate login page. This frictionless authentication method enhances user engagement and retention.
One-Time Password (OTP): Provide single-use codes sent via email or SMS for secure authentication without passwords. Ideal for scenarios where users need quick, temporary access without the overhead of account creation.
Single Sign-On (SSO): Enable users to access your application using their existing enterprise credentials through SAML-based SSO. Ideal for enterprise environments where centralized authentication is critical.
Authenticator Apps (TOTP): Support time-based one-time passwords generated by authenticator apps like Google Authenticator or Authy. Great for applications wanting a similar experience to SMS OTP but without the cost of sending messages.
Passwords: For applications that still use passwords, move them over to Descope while also enforcing complexity rules and integrating with the "Have I Been Pwned" database to ensure compromised passwords are not used.
nOTP (WhatsApp): Simplify the login process by allowing users to authenticate via WhatsApp without the need for codes or typing. nOTP is great for regions where WhatsApp adoption is high, ensuring a frictionless user experience.
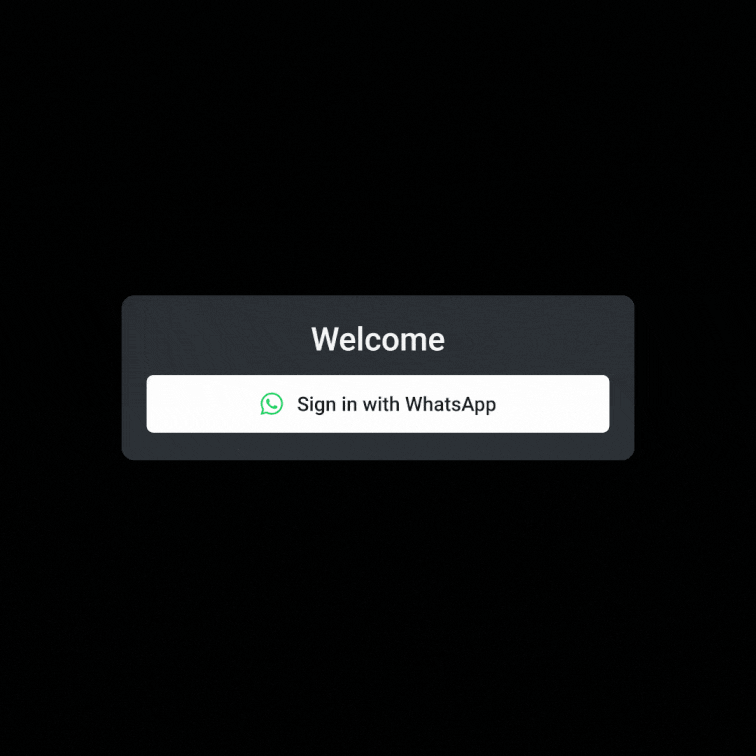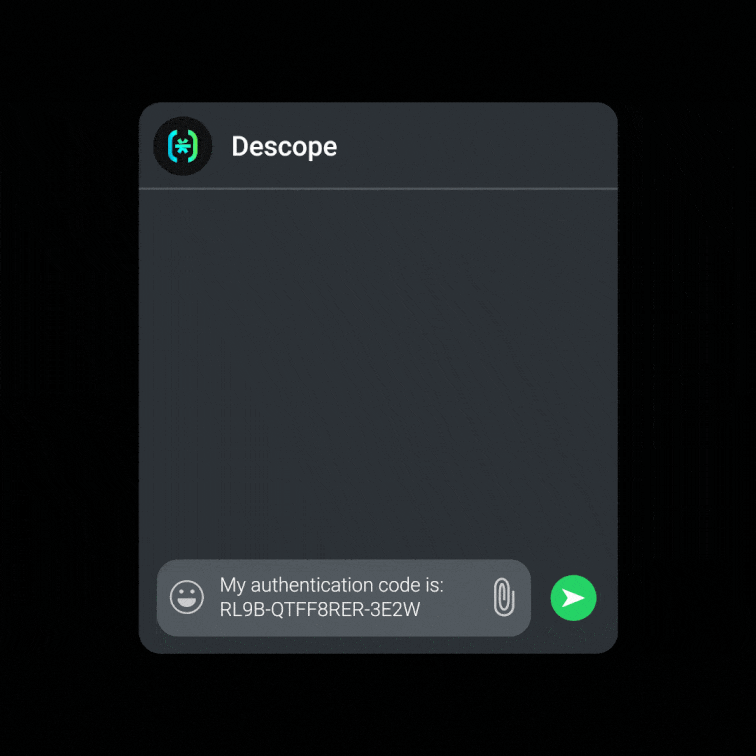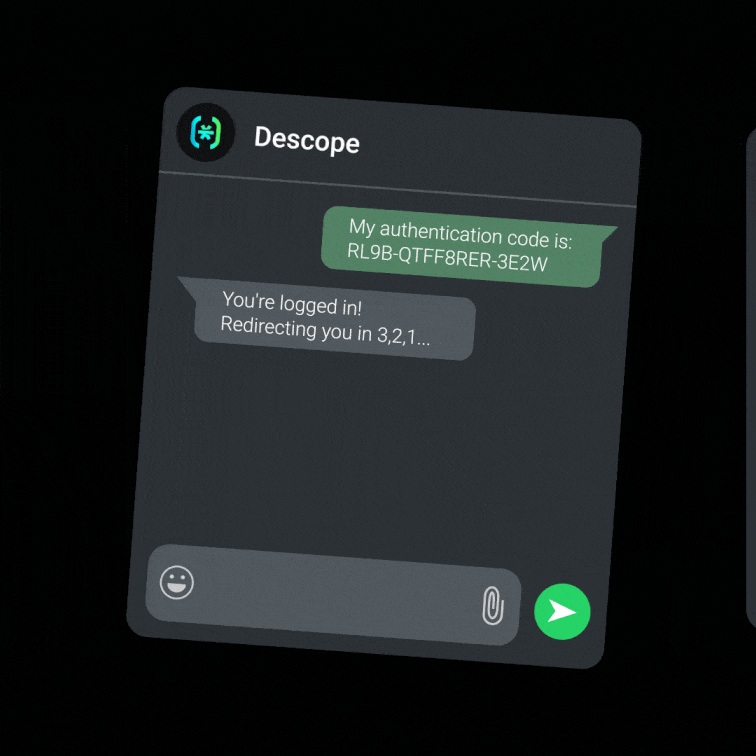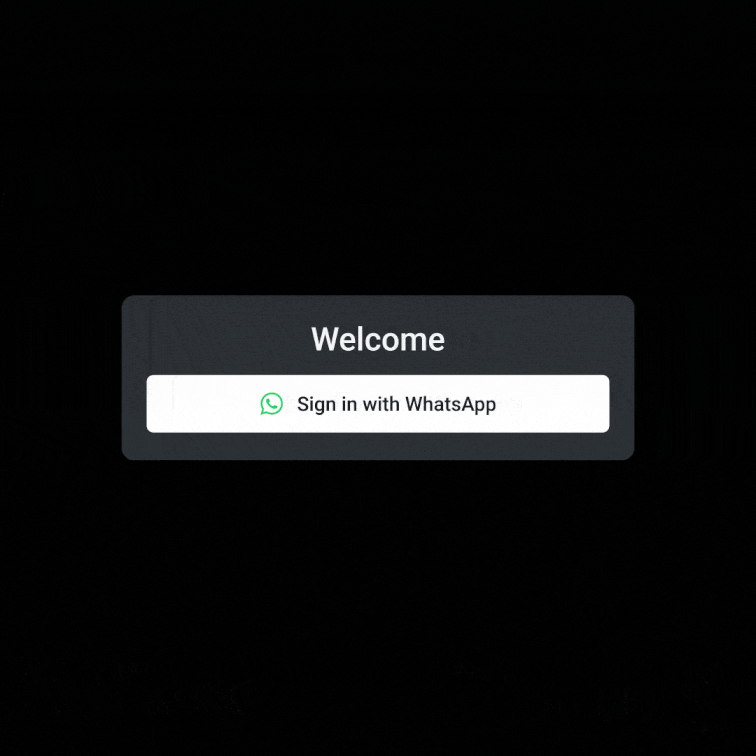
Embedded Link: Generate a single-use token for authenticating an existing user with the ability to be sent via any format, whether email, SMS, or something else entirely.
Simpler onboarding, improved conversions
Descope helps improve user onboarding and reduce abandonment by offering features like:
Passwordless auth: Swapping passwords for more user-friendly methods like passkeys, social login, and One Tap gets users into your app faster while also being more secure.
Low-friction purchases: Use methods like embedded links to send users directly to unfulfilled shopping carts or time-bound promotions.
Anonymous users: Allow users to explore your app without registering, then progressively profile them to gather more information over time.
Progressive profiling: Collect user details incrementally, reducing the upfront friction of a lengthy registration form.
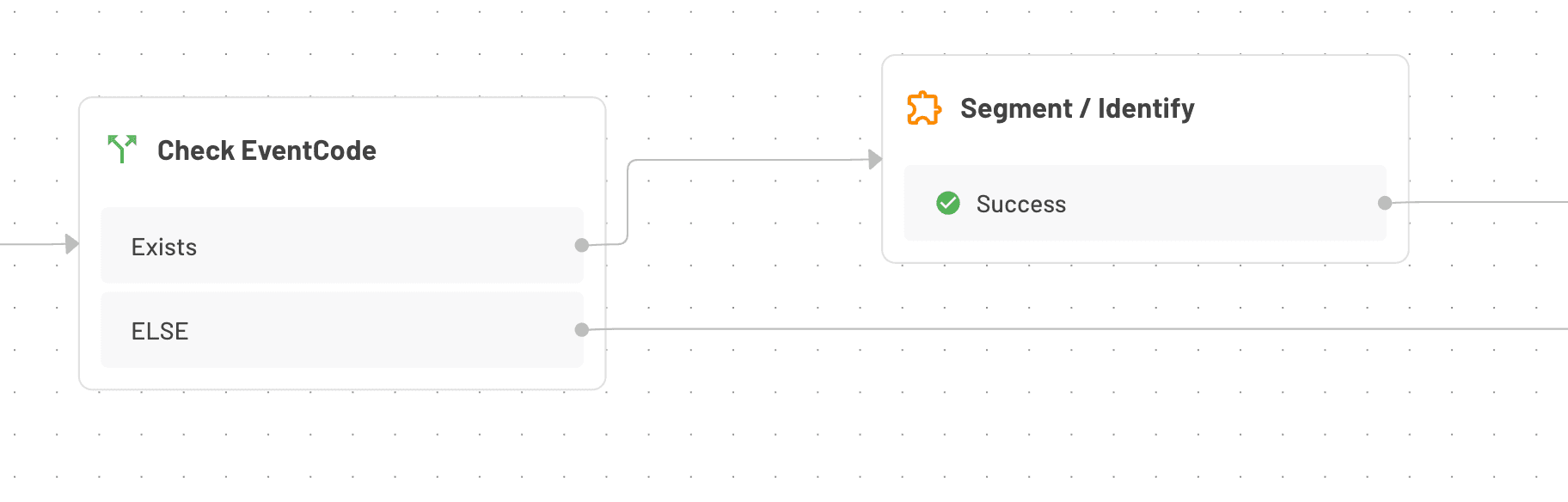
Connectors for GTM tools: Integrate with tools like HubSpot, Segment, and Amplitude to sync identities and provide personalized experiences.
Flexibility and customizability
Tailor authentication flows to your application's specific needs:
Multi-factor authentication (MFA): Implement any authentication method as a first or second factor to enhance security. If you already have a CIAM provider but are looking to improve MFA, use Descope as an OIDC Provider to augment existing auth systems with strong MFA.
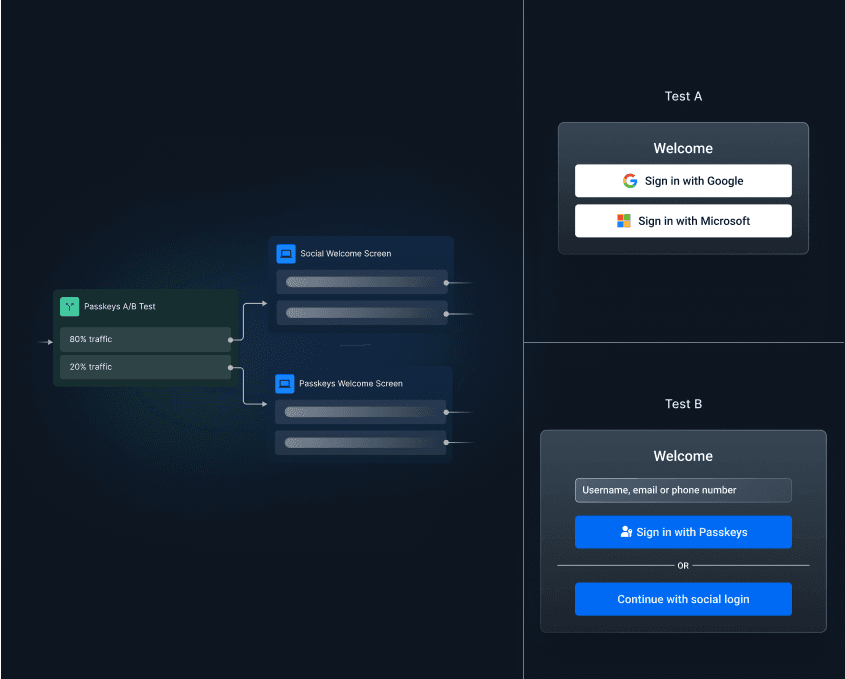
A/B testing: Conduct experiments with different authentication methods or user journeys to determine the most effective approach for your audience. Successful A/B testing can identify identity flows that boost user conversions and reduce drop-offs by tailoring experiences to specific user groups (e.g., comparing Magic Links vs. Social Login for new user registrations).
Get some A/B testing examples in this blog.
User impersonation: Allow support teams to impersonate end users for troubleshooting and support purposes. This streamlines customer support by enabling agents like employees or Managed Service Providers (MSPs) to replicate user issues (like authentication errors) in real time without requiring sensitive credentials, resulting in faster issue resolution and improved customer satisfaction.
Customizable templates: Personalize email and text templates to align with your brand identity and communication style. Create localized templates for email/SMS notifications to cater to different regions and languages, enhancing user trust and engagement.
Self-serve user profile management: Empower users to manage their own profiles with easy-to-embed widgets and a no-code widget editor. Customize profile management flows, such as updating user details or preferences, without requiring backend changes. This reduces the load on your support team and improves the user experience.
Omnichannel user journeys: Deliver seamless and unified user experiences across devices and channels. Enable native mobile flows, cross-device passkeys, and SSO to ensure users can securely authenticate across your B2C digital properties. Support cross-platform interactions and eliminate friction by providing a consistent experience on web, mobile, and other connected devices.

Security minus friction
Ensure robust security measures without compromising user experience:
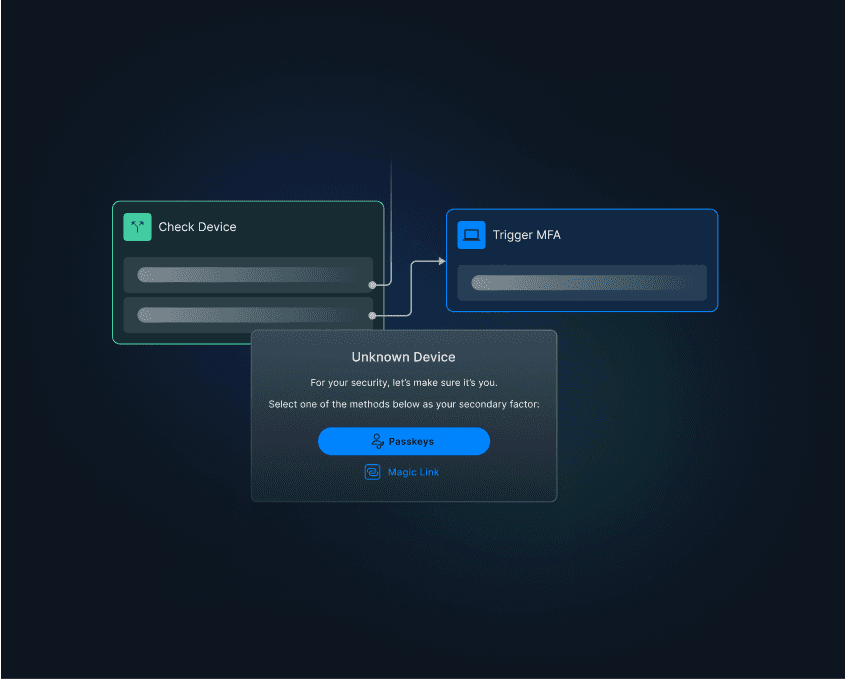
Adaptive MFA: Implement conditional multi-factor authentication based on risk factors such as new devices, VPN usage, or impossible travel scenarios. Unlike standard MFA, which applies uniformly to all logins, or step-up MFA, which triggers during sensitive actions, Adaptive MFA dynamically evaluates risk in real time. For example, it might require additional verification for a login from an unrecognized device but allow seamless access from trusted locations, balancing security and user convenience.
Bot protection: Utilize built-in bot detection and integrate with third-party fraud prevention services to safeguard against automated attacks. Explore our range of connectors for enhanced security here.
Fraud connectors: Integrate with services like reCAPTCHA, Forter, Telesign, and AbuseIPDB to enhance security and prevent fraudulent activities without adding undue friction for legitimate users. Drop in data and actions from connectors right in your Descope user journey, easily stack risk scores from different providers, and switch out one fraud score source for another without spending any engineering time.
Password security: For applications that still use passwords, enforce complexity rules and integrate with the "Have I Been Pwned" database to ensure compromised passwords are not used.
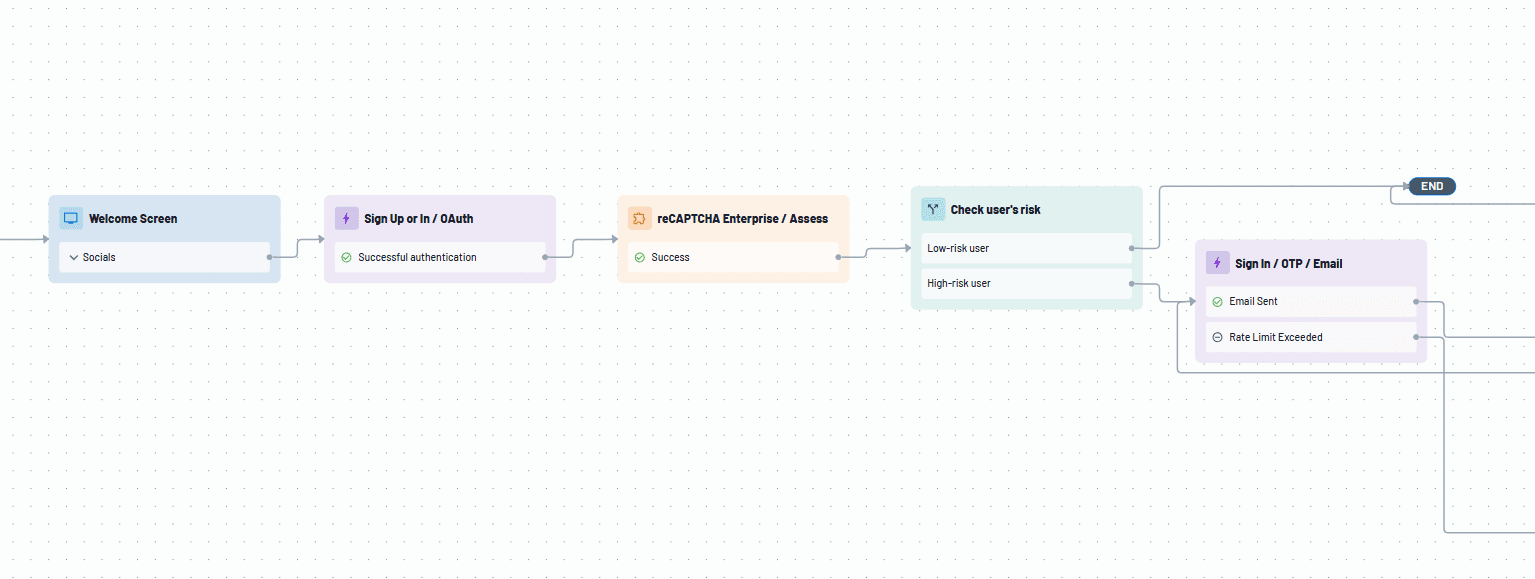
Descope Flows
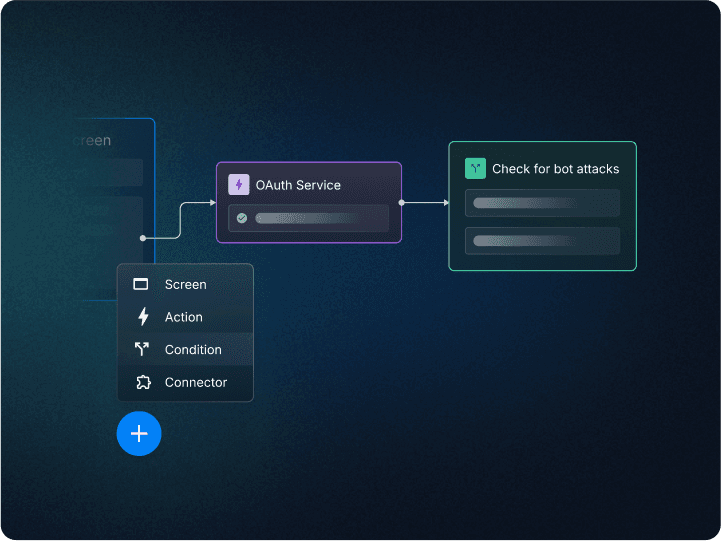
Descope provides a visual, no-code interface called Flows, enabling you to design and customize authentication processes effortlessly. With the Flow Builder, you can define authentication-related application logic in a visual workflow, creating flows for user sign-up, sign-in, MFA, and other similar use cases. Once created, these flows can be embedded into your application (eg. via SDKs).
This intuitive platform allows you to:
Select authentication methods: Choose from various authentication options to suit your application's needs.

Add multi-factor authentication (MFA): Enhance security by incorporating additional verification steps.
Adjust styles: Customize the appearance of authentication screens to match your brand identity.
Implement conditional logic: Require additional layers of authentication for users exhibiting risky behavior.
Customers love Descope Flows because it:
Decouples auth from the app: Descope Flows are futureproof by allowing you to make ongoing changes to authentication workflows without modifying your app's codebase. This separation helps reduce maintenance overhead and improve agility, for instance letting you easily replace passwords with social login or email OTP with magic link.
Harmonizes actions across frontend and backend: Descope Flows enable seamless integration of frontend actions (such as screens and user interactions) with backend logic (such as token management, routing to Identity Providers, and handling custom claims).
Works in concert with the SDLC: Descope Flows fit directly into your software development lifecycle (SDLC) by enabling continuous integration and continuous deployment (CI/CD) practices. You can manage your authentication workflows through version control and automate deployments across different environments. For instance, to learn more, you can check out our Github Template showcasing how you can integrate Descope via Github Actions.
By leveraging Descope Flows, you can streamline user engagement, reduce development time, and maintain robust security standards without writing extensive code.
Conclusion
Descope's CIAM platform empowers B2C application developers to implement secure, flexible, and user-friendly authentication and user management systems. By leveraging Descope's passwordless authentication methods, extensive customization options, and advanced security features, developers can enhance user experience, reduce friction, and protect against threats, all while accelerating time-to-market.
Ready to enhance your application's authentication experience? Sign up for a Free Forever Descope account and join AuthTown, our open user community for developers to learn about authentication.






