Table of Contents
The importance of strong IAM in banking
In the banking sector, where security and trust are paramount, the adoption of sophisticated customer Identity and Access Management (IAM) strategies is indispensable.
Without robust IAM, cybercriminals can use broken authentication in mobile banking applications to steal funds, victimize bank customers, and cause legal, ethical, and reputational complications for the bank.
Because of the direct tie between account management and financial fraud, IAM is considered a core part of most regulatory frameworks related to data privacy and security—especially in banking.
If you’re facing challenges with existing CIAM systems or would like to implement a new one from scratch, Descope can help your organization easily add secure, seamless authentication and user management to any customer-facing application. Find out more.
The importance of strong IAM in banking
Managing access and user identities is critical to security in every industry, but it’s especially important for banks and financial institutions. User identity and account mismanagement can lead to cybercriminals stealing or defrauding individuals and institutions. One study found that authentication weaknesses cause up to 80% of global financial breaches.
In addition, in 2023 banking and financial services ranked among the most commonly targeted industries for ransomware attacks, just behind information technology.
Protecting user identities safeguards banks and their customers from these threats.
User identity management is also a key part of regulatory compliance for banks and financial institutions. Know Your Customer (KYC) and Anti-Money Laundering (AML) legislation requires banks to carefully identify their account holders and ensure that they are who they say they are over time. Governing bodies such as the Financial Industry Regulatory Authority (FINRA), the Financial Crimes Enforcement Network (FinCEN), and the Securities and Exchange Commission (SEC) require banks and financial institutions to implement IAM practices systematically.
Beyond satisfying requirements, secure IAM flows bring other benefits to banks.
Seamless login and account management options maximize customer satisfaction while lowering costs associated with helpdesk queries. And mitigating the threats associated with data breaches makes attacks less likely—the average cost of a data breach in the financial industry was $5.9M in 2023—while also maintaining a strong brand reputation.
Customer authentication: The first line of defense
In cybersecurity terms, authentication is the practice of confirming an individual’s identity so that they can access a specific platform, such as their online banking account. The most basic version of this is when a user verifies their identity by inputting credentials known only to them, such as a unique username and a password.
However, most banks today use multi-factor authentication (MFA), which requires at least two knowledge, possession, or inherence factors to verify a user.
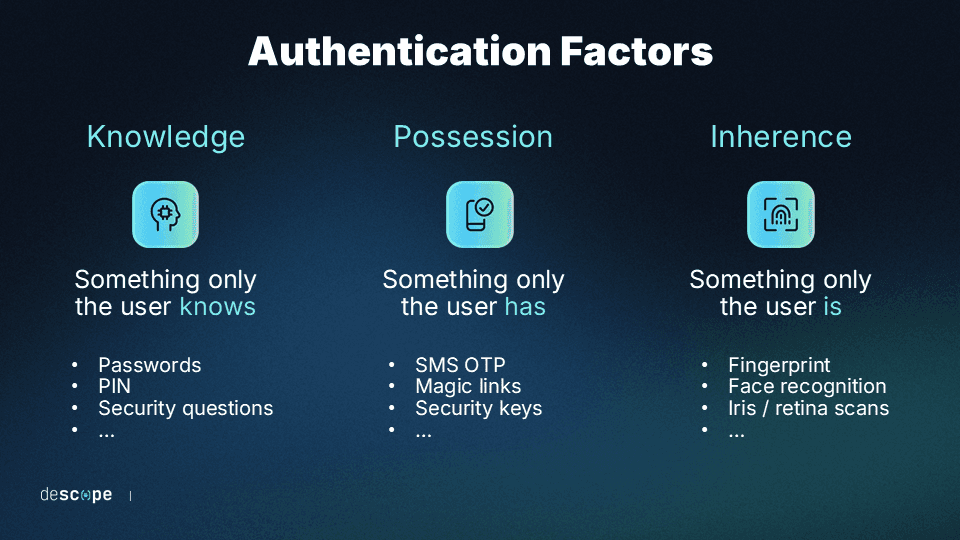
A traditional example of MFA that has been used by banks for decades is the standard access procedure at an ATM. Namely, a customer can usually verify their identity by scanning a card (a possession factor), and then also punching in their personal identification number (a knowledge factor).
These days, since most customers use mobile banking apps, their identity is typically verified using credentials (a knowledge factor) and then OTP authentication, face recognition or fingerprint scanning ( inherence factors)
Best practices for customer identity authentication in banking include deploying authentication methods, like:
Biometric auth (passkeys): Banks can leverage passkeys for mobile banking by using devices’ built-in face- or finger-scanning technology. Passkeys are unphishable, familiar to users since they unlock their phones in the same way, and provide a seamless experience.
Adaptive authentication: This is a dynamic approach that changes the specific requirements for user login depending on real-time analysis of risk factors present at login. For example, a banking app might analyze the user’s location, whether they are using a secure VPN, or the time of their login attempt, and compare it against their access history. Anomalies might mandate the use of an additional factor.
Identity orchestration – This is another overarching approach that streamlines logins and account management across different software and functionalities. In a banking context, it can be used to connect account functions like withdrawals and transfers with other banking and financial services platforms, keeping interoperability secure and easy.
These and other considerations make for secure authentication in a banking customer IAM deployment.
Customer authorization: The second line of defense
Authentication is not the only consideration in IAM. Banks and financial institutions also need to account for secure authorization, which is more granular control over which specific functions the authenticated user has access to given their level of permissions.
This is critical in banking contexts because distinct functions such as transfers, withdrawals, and account opening and closing have varied implications for a user’s security. So, in practice, certain functions may require more strenuous vetting and verification than others.
Recommended approaches for authorization in contemporary online banking include:
Role-based access control (RBAC): A user’s role determines the data, locations, and functions they have access to. For banking software, it can be used to give full account functionality to primary account holders and limited access to other users.
Fine-grained authorization: This dynamic approach is based on more minute criteria than RBAC, such as limiting overall access or specific functions based on recent activity. For example, a customer's access rights can be automatically adjusted based on the current context, such as lower transaction limits at higher risk levels or outside regular hours.
When choosing the right authorization model, it’s important to balance security, user experience, and admin / implementor experience. All IAM needs to be easily intelligible to users and scalable by IAM practitioners to be effective.
Federated SSO: Unified customer journey
Many banks have multiple customer-facing applications such as an online banking account, a mortgage account, separate accounts for credit cards, partner portals, and so on. As the number of apps and Identity Providers (IdPs) increase, more user friction is added and financial institutions risk losing visibility into the customer journey. Knowing how customers are engaging with the business across multiple apps can unlock insights that can drive future growth.
Federated authentication is a popular solution to break customer identity silos. By building a system (or using a third-party provider) to centralize user identities across apps, route user logins to the right IdP, and bridge connections across disparate auth systems, financial institutions can grow their portfolio without fragmented identity management.
Here are some ways federated authentication can help banks:
Connecting off-the-shelf apps (e.g. support portal) to the right IdP by using protocols such as SAML and OIDC.
Consolidating identity management after M&A activity.
Providing IdP resilience by routing login attempts to a backup IdP during traffic surges or downtime.
Implementation considerations and best practices
Beyond authentication and authorization, banks and financial institutions also need to ensure security across all matters of user account management. Passwordless authentication reduces the need for users to create and remember passwords, which can automatically make account management both safer and easier for all parties involved.
However, banks need to carefully balance users’ convenience with security considerations.
For example, baseline MFA flows without advanced measures are vulnerable to MFA fatigue attacks (also known as MFA bypass). These schemes victimize users and banks by mimicking the MFA notifications they’re accustomed to receiving in the hopes of breaking authentication. The best ways to defend against them often involve incorporating more stringent login procedures, which may cause friction if they’re poorly implemented or users feel they aren’t supported.
Another issue with standard-issue MFA deployments is that they can be vulnerable to phishing attacks. Phishing-resistant MFA is specifically designed to prevent these threats, using dynamic behavioral analysis and other risk-based metrics to ensure security. Banks using MFA should prioritize methods like these despite any up-front resources required for implementation.
Apart from adaptive MFA – which enforces MFA based on the risk of the login attempt – it’s also important to add security controls based on the risk of the user action. That’s where step-up authentication comes into play.
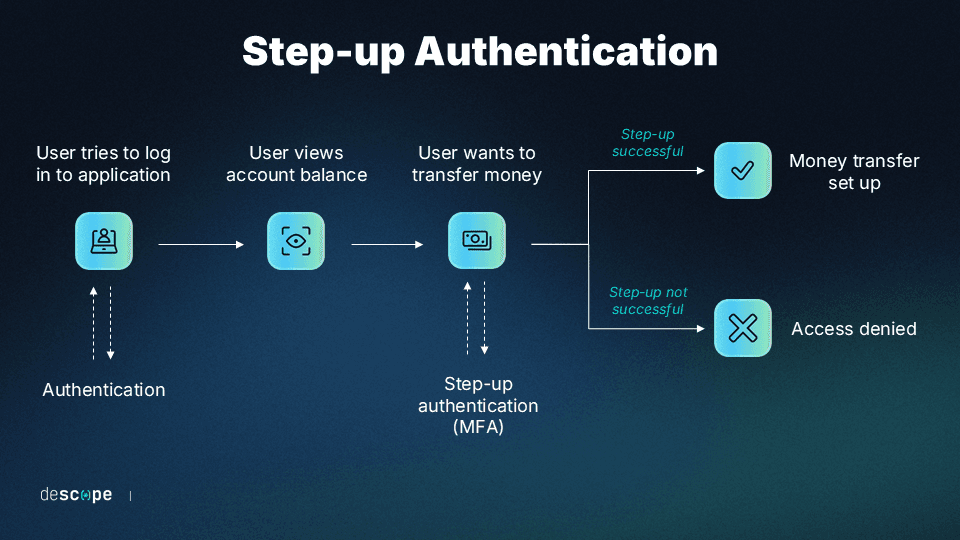
Step-up authentication is a mechanism to add an additional auth check before a sensitive user action (e.g. transferring money to an external account). Using OTPs or magic links are popular options for step-up auth.
Beyond these known risks, cyber threats and regulatory requirements around customer identity are constantly changing, and banks need to be ready to adapt if a new risk—or law—emerges.
Secure and user-friendly CIAM for banks with Descope
In the banking sector, where the stakes of security breaches are extremely high, adopting robust IAM practices is not merely a recommendation—it's a necessity. Financial institutions face the dual challenge of protecting sensitive customer information and financial assets while delivering a seamless experience that meets the modern consumer's expectations for convenience and rapid access.
Descope recognizes the unique pressures faced by the banking industry and offers a comprehensive suite of solutions designed to address these challenges head-on. Our workflow-based CIAM platform brings together the power of secure authentication, seamless user experience, and advanced customer IAM capabilities, all while ensuring compliance with stringent regulatory requirements.
Here’s what Arkadiy Goykhberg, CISO of Branch Insurance (a Descope customer) had to say:
“Ensuring that customer authentication processes are secure is a tricky balancing act. Descope’s flexible workflow approach has helped us add strong, phishing-resistant WebAuthN authentication when end-user hardware and software support it and fall back on other MFA options when it can't be supported. Visualizing the user journey as a workflow enables us to audit and modify the registration and authentication journey without making significant code changes.”
Whether you're looking to upgrade your existing customer IAM solution or implement a new one from scratch, Descope provides the tools and expertise needed to make the process as smooth and secure as possible.
Sign up for a Free Forever account with Descope and drag and drop your customer journey flows. Have questions about our platform? Book time with our auth experts.