Table of Contents
What is facial recognition authentication?
Facial recognition software has become so commonplace that it has become second nature for us to use it for unlocking phones, tablets, and other daily-use devices. And the underlying tech has broad utility, with over 70% of world governments leveraging facial recognition. Around 40% even used it to combat the spread of COVID-19. Almost everyone is familiar with facial recognition, even if they don’t use it.
What is facial recognition authentication?
Facial recognition is software that uses a scan of a person’s face or likeness to authenticate their identity. In multi-factor authentication (MFA) systems, facial scans are one form of inherence factor—an element unique to a person. Inherence factors are used alongside a knowledge factor (something a person knows) or a possession factor (something a person has).
An example of facial recognition in practice is unlocking any iPhone since the X. When Apple launched Face ID in 2017, people heralded it as the future of seamless, secure access to devices. And today, facial recognition is one of the more popular forms of biometric auth because of its ubiquity across popular consumer devices. Most contemporary smartphones and tablets feature it.
Developers can use facial recognition authentication to improve the user experience and security of their app or website.
How does facial recognition work?
Facial recognition generally works by leveraging an accurate, in-depth scan of an individual’s facial features. That scan is abstracted and stored securely on the user’s device; users are then prompted to provide a new face scan on login attempts. The subsequent scans are then compared against the original:
If they’re deemed accurate matches, access is granted.
If they don’t match, a re-attempt may be prompted, or the user may be asked to provide an alternate form of identification.
Facial recognition auth begins with a complex model of the individual’s face. This is most often performed by camera hardware directly on the device from which users are authenticating. The scans form a 3D model of the face’s underlying anatomical features through machine learning.
The way authentication utilizes facial scan data on the device—such as Apple's Face ID—or its own data depends on the implementation. Some organizations may opt for different security thresholds requiring a more complex image.
But, no matter what, follow-up login attempts must utilize the camera on a user’s device. This means that facial recognition auth always depends on the hardware, software, and user device permissions.
How accurate is facial recognition?
The accuracy of facial recognition technology has advanced significantly in recent years, making it a powerful tool for identity verification and authentication. Leading algorithms boast high accuracy rates, with top-performing systems achieving near-human precision.
However, challenges such as variations in lighting conditions, angles, and demographic biases can impact accuracy. Continuous advancements in machine learning and artificial intelligence are addressing these challenges, improving recognition rates across diverse populations.
Using facial recognition systems responsibly involves factors like transparent algorithms, data quality, and regular updates for accuracy and fairness.
Advantages of facial recognition auth
Here are four advantages of using facial recognition technology:
Convenience
Facial recognition offers unparalleled convenience for users. Users can authenticate themselves with a simple glance, eliminating the need to remember and input passwords or carry physical tokens. This frictionless experience enhances user satisfaction and encourages widespread adoption.
Enhanced security
Biometric authentication through facial recognition provides a high level of security. Each person's face is unique, making it difficult for unauthorized individuals to gain access. Apple estimates that, with Face ID’s technology in particular, the odds of a random person’s face unlocking another user’s account is less than one in one million.
Most device-based facial recognition technologies being compatible with passkeys and WebAuthn further bolsters security.
Efficiency and speed
Facial recognition authentication is extremely efficient and fast. Users can gain access with a brief look, saving valuable time compared to traditional authentication methods. This speed is particularly advantageous when quick and secure access is essential, such as in time-sensitive environments or high-traffic areas.
Contactless interactions
In an era of heightened hygiene concerns, facial recognition offers a contactless authentication method that minimizes physical touch. This is especially valuable in public spaces, healthcare settings, and other environments where reducing germ transmission is a priority.
Facial recognition applications
Here are some common use cases for facial recognition technology across different industries and sectors.
Access control and security
Building entry: Offices, hotels, and residential complexes can grant authorized individuals access to buildings or specific areas without needing keys or access cards.
Airport security: Airports enhance security by matching travelers' faces with passport photos, ensuring accurate identity verification during check-in and boarding.
Financial services
Mobile banking: Banks can provide secure and convenient access to mobile banking apps, allowing users to check balances, transfer funds, and make payments.
ATM withdrawals: Facial recognition at ATMs can reduce the risk of card theft and PIN-based fraud while enabling users to withdraw funds more securely.
Retail and ecommerce
Personalized shopping: Retailers can identify and greet loyal customers, offering personalized recommendations and discounts based on previous purchases.
Online authentication: Facial recognition enables users to securely and conveniently log in to their online accounts by analyzing their unique facial features for seamless authentication.
Healthcare
Patient identification: Hospitals and clinics can accurately match patients with their medical records, reducing the risk of medical errors and ensuring proper care delivery.
Telemedicine authentication: Facial recognition can confirm the identity of both patients and healthcare professionals during virtual consultations.
Education
Campus security: Educational institutions can enhance campus security by using facial recognition to identify authorized personnel and visitors, improving overall safety.
Attendance tracking: Facial recognition can streamline attendance tracking in schools and universities, automating the process and reducing administrative workload.
Law enforcement and public safety
Criminal identification: Law enforcement agencies can compare images of suspects with databases of known criminals, aiding in criminal identification and investigation.
Finding missing people: Face recognition CCTV systems empower police to swiftly locate missing children (and adults) by matching reference photos with past video appearances, enabling real-time alerts for accurate recovery.
Embrace facial recognition technology with Descope
Facial recognition technology offers multifaceted solutions that span across industries and challenges. Its capacity to enhance security, streamline processes, and personalize experiences showcases its versatility.
Descope helps developers easily add facial recognition for both authentication and identity verification in their user journeys. For authentication, Descope supports passkeys and device-native biometrics like Face ID and Windows Hello – developers can add these capabilities to their apps in minutes using drag-and-drop workflows.
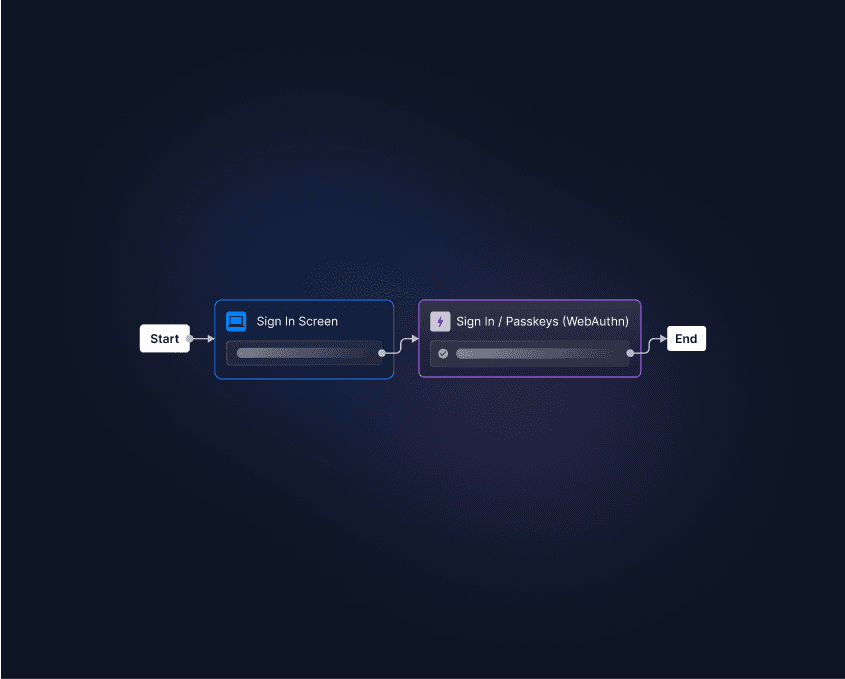
Descope also integrates bidirectionally with services like Amazon Rekognition to enable ID collection and verification processes within user journey flows. Data and actions from Amazon Rekognition can be weaved into Descope’s authentication flows to verify user-provided identification and do a “selfie check” as a risk-based MFA measure.
Sign up for a Free Forever account with Descope to “descope” authentication from your daily work. Have questions about our platform? Book time with our auth experts.





