Table of Contents
What is WebAuthn?
One of the biggest recent advancements in authentication, authorization, and user account management across all virtual platforms has been the shift toward passwordless authentication. Over a third of all organizations worldwide plan to adopt or continue using passwordless authentication in the next one to three years. And two of the top options available to them are WebAuthn and FIDO2.
WebAuthn is one of two key components of FIDO2, though it can be used without invoking the full FIDO2 stack. Below, we’ll provide an overview of these two authentication protocols, dive into their similarities and differences, explore the benefits of using one or both, and explain how to implement them.
What is WebAuthn?
Web Authentication API, better known as WebAuthn, is an open standard for user authentication on web applications. It leverages public-key cryptography, a highly secure framework involving key pairs, to authenticate users across services without a password. To learn more about public-key cryptography, check out our guide to all things WebAuthn.
The history of WebAuthn dates back to 2013, when it was proposed because of rising concerns about password security. After years of development, Level 1 was published as an official World Wide Web Consortium (W3C) recommendation in 2019, with Level 2 following in April of 2021. In that same month, a First Working Draft (FWD) of Level 3 was proposed, and its final form is imminent.
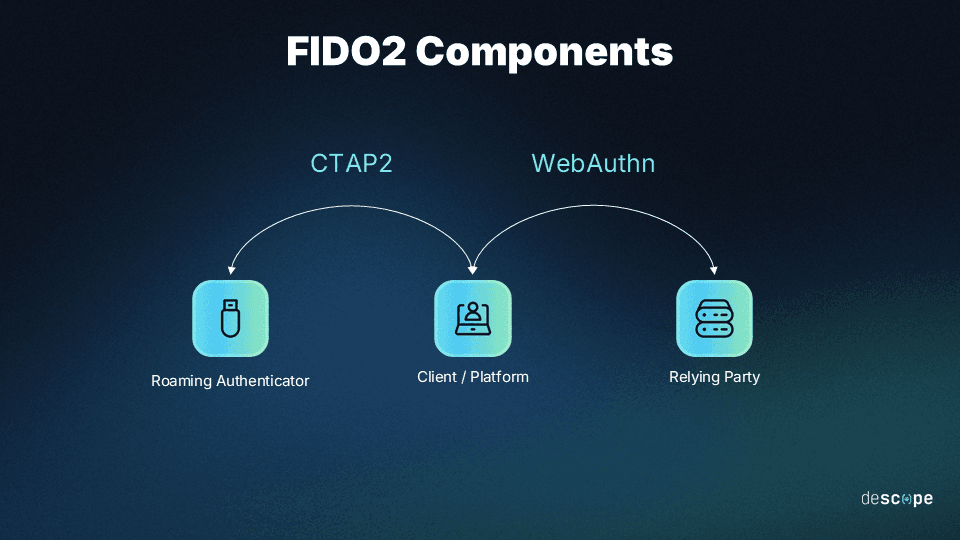
Along with Client to Authenticator Protocol (CTAP), it's one of the two components of FIDO2, which we’ll discuss shortly.
Today, WebAuthn is supported by most browsers and major websites, and players such as Google and Apple have incorporated features of the forthcoming Level 3 into their browsers ahead of its publication. Android users can enjoy native FIDO2 compatibility with Fido2ApiClient, while support on Apple devices is still forthcoming.
WebAuthn works by associating a user with something they are or possess, such as biometrics or hardware security key, though the most common application is via a mobile device that can combine both factors. Once the association is made, a passkey is generated which is then used for any future login attempts.
This process ensures security by focusing on inherence and possession factors rather than knowledge factors (passwords) that can be stolen or cracked. At the same time, it maximizes the user experience (UX) and minimizes friction.
What is FIDO2?
FIDO2 is an open authentication standard comprising two components, CTAP and WebAuthn, published by the Fast Identity Online (FIDO) Alliance. As its name implies, FIDO2 is an updated version of the original FIDO specification, and it enables passwordless authentication across web and mobile applications.
The FIDO Alliance, which launched in 2013, has grown substantially, presently including over 300 companies dedicated to streamlining secure authorization. The roots of what would eventually become FIDO2 were there from the beginning, and many of its component parts have been renamed and incorporated into the present version, FIDO2.
The other main component of FIDO2 is the Client-to-Authenticator Protocol (CTAP), which provides a uniform standard for communication between the client (i.e., a website or app) and roaming authenticators (e.g., a smartphone). Combining this with the cryptographic authentication of WebAuthn, FIDO2 enables seamless, secure passwordless authentication across a wide variety of applications.
WebAuthn vs FIDO2: key differences
Given the interconnectedness of FIDO2 and WebAuthn, they’re often referred to interchangeably. However, there are key differences between them:
FIDO2 is the broader term and standard that covers the entire passwordless authentication system (WebAuthn + CTAP).
WebAuthn specifically refers to the web API part of FIDO2 that developers use to enable browser-based (or Android-native) passwordless authentication.
Simply put, it’s impossible to have FIDO2 without WebAuthn.
However, it’s worth considering how WebAuthn and FIDO compare to other common solutions.
Use cases for WebAuthn and FIDO2
Choosing between various authentication protocols often comes down to the specific use cases and needs in a target deployment. For example, SCIM and SAML are most apt for identity management or single sign-on (SSO), respectively. Likewise, whether to use OIDC or SAML depends on whether target systems are more web/mobile based (OIDC) or utilize more legacy software (SAML).
Choosing between a full FIDO2 implementation and WebAuthn is similar, with one key difference: imbalance.
Using FIDO2 requires WebAuthn, but it is possible to use CTAP with a platform-specific API rather than generic WebAuthn. Some major platforms implement CTAP in this way, like Microsoft's Win32 WebAuthn API or Google's FIDO2 API for Android. As the names of these APIs suggest, they are compliant with the WebAuthn and FIDO2 specifications, but they offer extra integration with their specific platforms. Regardless, all FIDO2 use cases are WebAuthn use cases by default. And it’s a boon, as most environments using contemporary and emerging technologies will favor the greater security and assurance that come with FIDO2’s combination of WebAuthn and CTAP.
However, mature organizations that depend heavily on legacy software may have no choice but to use WebAuthn with the older FIDO 1.0 Universal Authentication Framework (UAF) or Universal Second Factor (U2F).
The biggest benefits of WebAuthn and FIDO2
WebAuthn and FIDO2 are more similar than different, and this becomes much more apparent through the benefits they provide. Both streamline login, account management, and overall authentication processes.
This all starts from favoring passwordless authentication methods over traditional password-centric ones, which are susceptible to credential theft and weak or mismanaged credentials. Well-intentioned users could create weak passwords or fail to update them due to fatigue from the abundance of accounts. And simply having credentials to steal makes users prime targets for cybercrime.
In addition, both platforms make account management significantly easier for users, which improves overall UX and cuts down resource costs for IT helpdesk calls and other support.
Another major benefit of both WebAuthn and FIDO2 is their widespread adoption. No less than 85% of all devices worldwide can use one, if not both, of these authentication standards, and that number is constantly increasing as platforms add or increase their support. In a recent example, the chat platform Discord added full support for WebAuthn security keys in August of 2023, which instantly made logins both safer and easier for over 500 million registered users.
Implementing WebAuthn and FIDO2 in applications
For developers, WebAuthn and FIDO2 can be installed in nearly any software project. And for adopters, beyond simply adding the functionality, there are also issues of inventory and staff training to account for, along with compatibility scanning to ensure seamless interoperability.
Setting up passkey authentication with WebAuthn and/or FIDO2 is as simple as:
Installing or importing and then initializing the software development kit (SDK).
Enabling users to sign up through information channels to and from target browsers.
Implementing user sign-in through a single call between the platform and browser.
Adding user device intake and update functionality to allow for new biometric signifiers.
Enabling session validation (i.e., granular session management) for long-term security.
Developers can streamline implementation further with Descope flows (see below).
Some challenges that dev teams and adopters can face when implementing WebAuthn or FIDO2 involve the sheer scope of user, device, and key registration. The process is relatively complex compared to traditional password setups, and a high volume and diversity of users, devices, and accounts can lead to high resource demand. There are also issues with support in legacy-heavy tech stacks, particularly with FIDO2, where migration adds more potential costs for IT teams.
How Descope simplifies WebAuthn and FIDO2 integration
Descope allows dev teams to add WebAuthn and FIDO2 to any program, app, website, or other development project in a swift and cost-efficient manner. Our platform powers biometric authentication alongside a wide variety of other authentication solutions and approaches, giving developers, leaders, end users, and all other stakeholders various options for seamless, secure authentication management.
Descope Flows allow all the benefits of WebAuthn and FIDO2 to be added near-instantaneously with a no-code, drag-and-drop process. Simply select the specifications you’d like to implement and place them into your project—and watch adopters and end users reap the rewards.
Sign up for a Free Forever account with Descope to simplify your auth with SAML, OIDC, or any other protocol you need. Have questions about our platform? Book a demo with our auth experts.






