Table of Contents
OTP authentication challenges
We’re excited to announce nOTP (no-tee-pee), a new authentication method that logs users in via WhatsApp to provide a frictionless experience while greatly reducing SMS messaging costs. If your business is currently struggling to scale OTP authentication and has a WhatsApp-heavy user base – which is pretty much any user base with a smartphone – nOTP can help.
If you’re a watcher more than a reader, book a nOTP demo and see how it can work for your app! Some other “get to the point” resources below:
Experience nOTP for yourself on this demo site.
Watch this demo video for under the hood details.
For more on the Why and What of nOTP, keep on reading.
OTP authentication challenges
People love dunking on passwords (we are usually first in line), but we sometimes forget that not all passwordless methods are created equal in terms of security and UX. While OTP authentication is certainly preferable to creating, forgetting, and resetting passwords ad infinitum, it comes with its own set of challenges.
Here’s what we have heard from hundreds of customer conversations:
OTP costs are not scalable: Whether organizations maintain their own messaging infrastructure or use a third-party provider to deliver SMS OTPs, the impact on variable costs is not sustainable as their user base grows.
Fatigue and friction: Plenty of users – especially in APAC – have grown tired with the preponderance of OTPs in their lives. This has weakened the perception of OTP and also makes users more vulnerable to social engineering.
Security gaps: OTPs are tougher to compromise than passwords, but they are susceptible to phishing, SIM swapping, man-in-the-middle attacks, and other bypass attempts.
Deliverability worries: Since OTPs depend on users’ phone connectivity and the SMS provider’s deliverability, message failures are bound to happen, causing friction and dropoff.
International travel: SMS OTP deliverability is tied to your users’ SIM. This presents authentication difficulties during scenarios like international travel unless users have a roaming SIM or purchase additional packages. Even with a roaming package, text messages often get dropped when traveling internationally and are considered unreliable.
With nOTP, our goal is to provide businesses a better phone-based authentication method that delights end users, speeds up onboarding, and doesn’t burn a hole in your pocket.
nOTP in a nutshell
nOTP is a way for users to log in via WhatsApp without needing to provide a login ID, enter a code, or indeed type anything at all. Here’s how end users will experience nOTP:
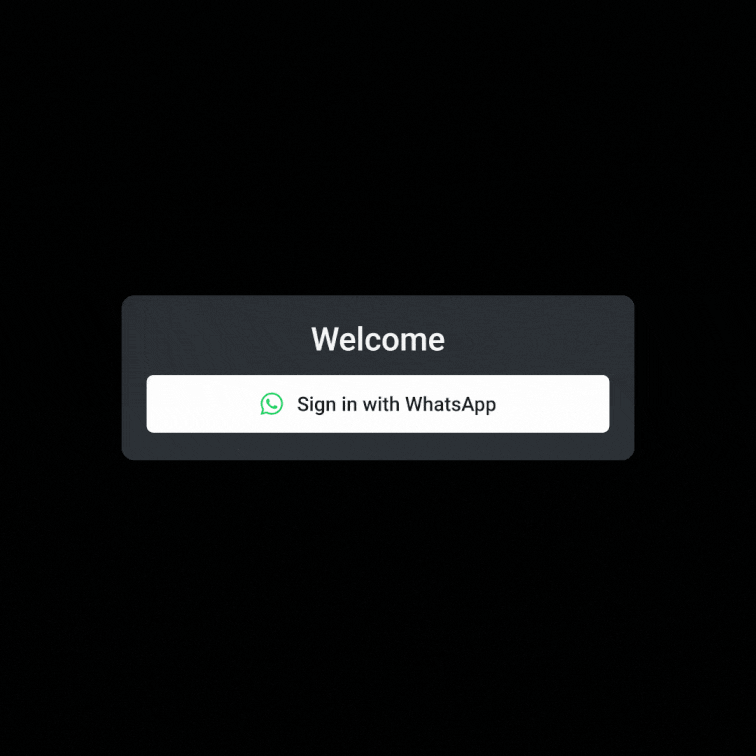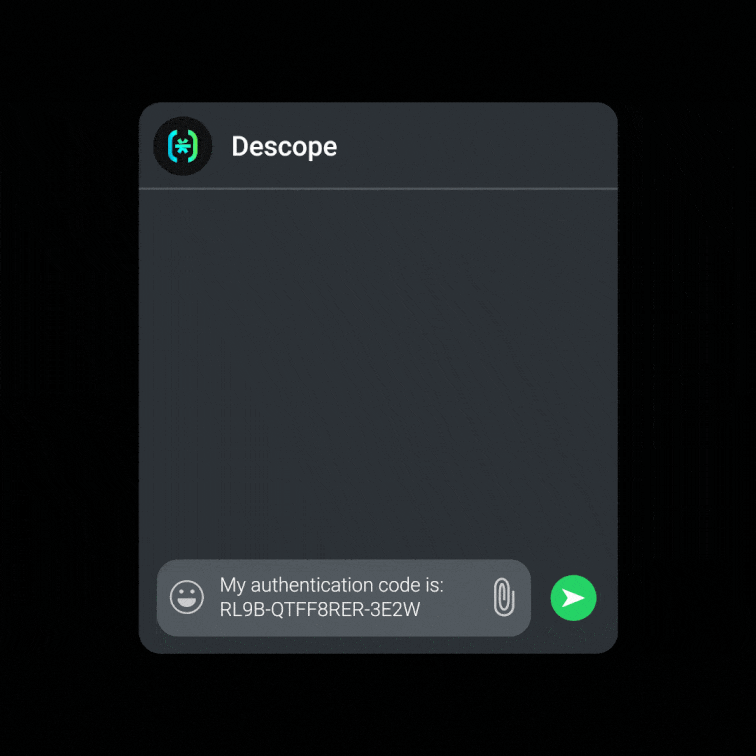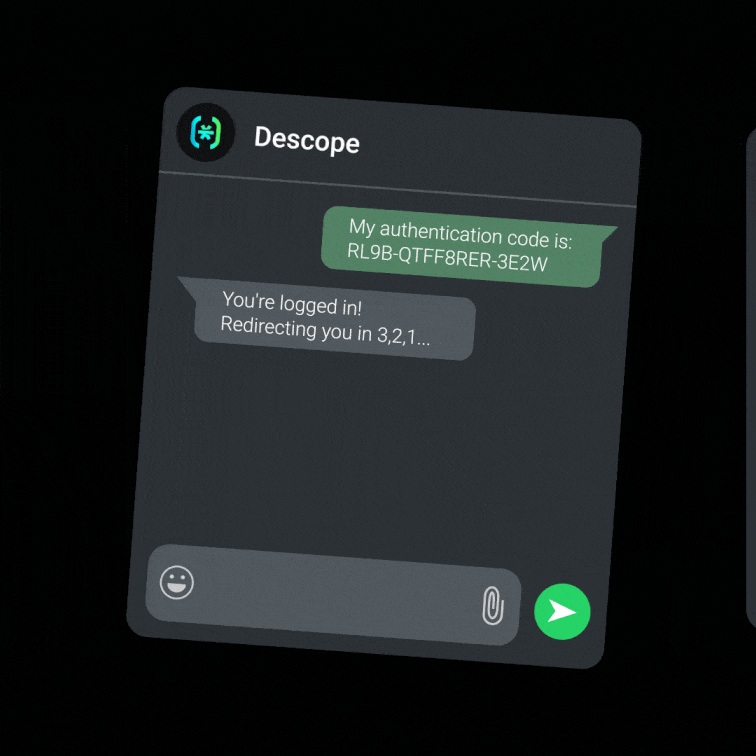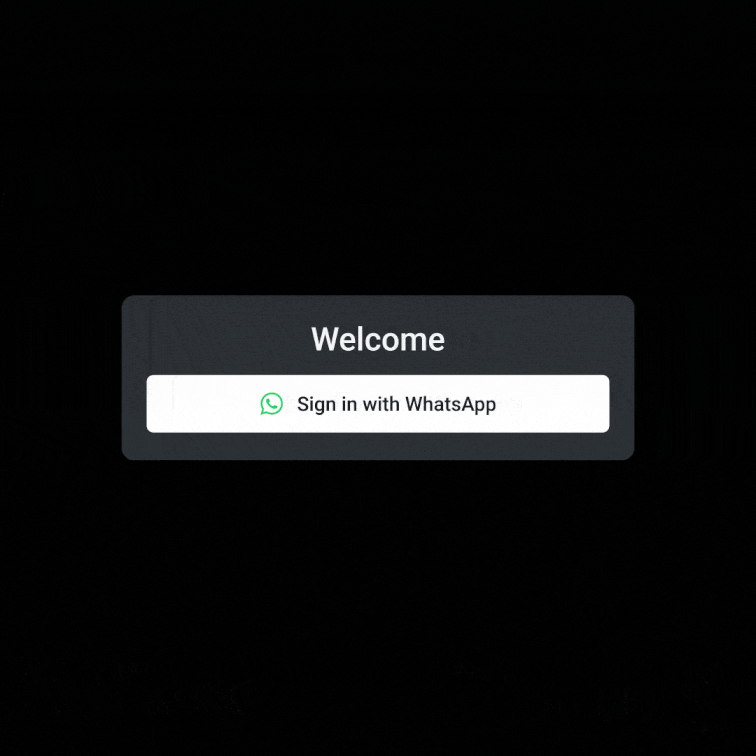
Scan a QR code OR click a “Sign up / log in with WhatsApp” button.
Press “send” on a pre-populated message that opens up in their WhatsApp app.
Get logged in!
Seems magical at first glance, so let’s pull back the curtain a bit.
Why did the user not have to type any login ID (phone number, username, etc.)? Because Descope uses the incoming user message in WhatsApp to identify and authenticate the user, including getting their validated phone number.
Why are there no / low messaging costs involved? Because user-initiated conversations are not charged, and free-form business replies within 24 hours aren’t charged either. Zooming out, WhatsApp has been known as a budget-friendly alternative to SMS authentication, so nOTP has a positive impact on COGS either way.
The demo video below goes into more detail on nOTP.
Let’s take a look at how the nOTP process actually works.
Under the hood
Customers can implement nOTP using Descope Flows (our no / low code visual workflow editor) or SDKs. With a toggle, you can also choose whether to automatically open the user’s WhatsApp in a new tab to start the authentication process to provide a more native experience.

Here’s a simplified view of how a nOTP flow works. The three entities involved are the user’s device, Descope, and the WhatsApp client.

The user starts the process by clicking on the “WhatsApp” login button or scanning a QR code, depending on your app’s nOTP implementation approach.
Descope sends back two things:
A user code, which is a multi-character code used to authenticate the user.
A machine code, which is leveraged by the user’s device to poll Descope on whether the user code has been used or not.
The first poll to Descope returns a negative response (i.e. the code has not been used yet) – this redirects the user to WhatsApp with the prepopulated user code in a message.
When the user sends the prepopulated message, Descope checks the code and sends back an approval or error message to the WhatsApp conversation with the user.
If the user is approved, the next poll from the user’s device to Descope will return a positive response. The user is then logged in.
You can find a more detailed explanation of nOTP including Descope setup instructions in our documentation.
nOTP use cases
nOTP can be used by any business currently using OTP or other phone-based authentication methods. The two most germane use cases that come to mind are:
Mobile app authentication
WhatsApp authentication is a powerful method for mobile-native applications, especially those that already have a WhatsApp Business presence and use the channel for customer communications.
Imagine this: your users click a “Log in with WhatsApp” button, are redirected to a WhatsApp conversation with your business, press “Send” on a prepopulated message, and are logged in. This approach provides a more native experience without manual context switching, opens the door to more omnichannel user communications, places zero cognitive load on your users, and is faster than using OTP.
TV / smart device authentication
Authenticating on smart devices like TVs has many points of friction. Users generally have to manually type out a URL on another device, log in with their credentials, and enter a code to authenticate their account on the TV. Or even worse, users sometimes have to type in their login credentials on the TV using a magic remote, virtual keyword, or other subpar methods.
Using nOTP can bring this process into the 21st century.
Imagine this: your users scan a QR code displayed on the TV, are redirected to a WhatsApp conversation with your business, press “Send” on a prepopulated message, and are logged in to their account on the TV. This approach is faster and more seamless than requiring users to perform laborious and error-prone tasks (e.g. typing in URL, typing in code).
Conclusion
Messaging services like WhatsApp are a key customer communication channel for many businesses. With nOTP, WhatsApp can now also become a trusted authentication channel that your users will greatly prefer over being asked to enter in yet another OTP.
If you’d like to see a nOTP demo and discuss any use case you have in mind, book time with our team.
P.S. What’s with the name?
When creating something new, choosing what to name it can be a tricky affair. There’s a spectrum of names from descriptive (e.g. Chat Authentication, WhatsApp Authentication) to fanciful (e.g. Yeehaw Auth) that we could have gone with.
Ultimately, we went with nOTP to directly pit this auth method against the auth method it is destined to usurp. While developing the tech, we also noticed it was defined by points of friction that were not present.
No user-submitted login ID. No typing in a code. No SMS costs. No OTP. nOTP. It tracks.